
From "Chasing Shadows" to 2,048 Words That Determine Trillions in Crypto Assets
TechFlow Selected TechFlow Selected

From "Chasing Shadows" to 2,048 Words That Determine Trillions in Crypto Assets
Use a trusted wallet, back up your recovery phrase offline, and never disclose it to others.
Author: Tyler
Recently watched Jackie Chan's latest film "Chasing the Wind," and there was an interesting scene—over HK$10 billion in crypto assets locked in a wallet secured by a 12-word recovery phrase, with only the last word missing.
After watching, I tried it out and found that the 10th and 12th words weren't in the standard recovery word list. Clearly, the screenwriters did this on purpose to prevent anyone from reconstructing the wallet based on the movie and committing fraud, as similar scams on-chain aren't uncommon:
Scammers deliberately leak a wallet address with a balance (typically on the Tron chain, exploiting the Owner mechanism) to lure people into sending gas fees, waiting like hunters; once funds are sent, they're gone forever.

The interesting point here is that in the movie, they claim only the final word is unknown. But in reality, recovery phrases follow the BIP39 standard, which includes only 2048 words. That means brute-forcing the last word would require at most 2048 attempts. If further narrowed down—for example, if the movie reveals the word starts with "es"—the possibilities become even fewer, solvable within a minute.
Yet beyond the movie, a more important question worth revisiting is: What exactly is the relationship between recovery phrases, private keys, and public keys? Why does losing your recovery phrase mean losing all your assets?
1. Recovery Phrase : Private Key : Public Key/Address = "Keychain" : "Key" : "House Number"
A recovery phrase is a backup method following the BIP39 standard—a sequence of 12, 18, or 24 words randomly selected and combined from a dictionary of 2048 English words via algorithm.
This recovery phrase is processed through the PBKDF2 algorithm to generate a seed. This seed then derives a series of private keys according to path standards such as BIP32/BIP44, which in turn correspond to a series of public keys/addresses.
One recovery phrase → generates multiple private keys → generates multiple public keys → corresponds to multiple addresses
In other words:
-
Recovery phrase = keychain, often having a one-to-many relationship with private keys; theoretically, one recovery phrase can derive thousands of private keys;
-
Private key = key, each private key corresponding to control of one address;
-
Public key/address = house number, can be shared publicly; others use it to send you funds;
Thus, think of the recovery phrase as your "keychain," and each private key as one of the keys on it, used to sign transactions and prove ownership over a specific wallet address—when you initiate a transaction, you're using your private key to sign, telling the entire network: "This transfer is authorized by me."
2. Can You Pick Your Own Recovery Phrase?
You might wonder: Can I just pick my own 12 words? Like birthdays, favorite English words, or idol names—to make it more personal?
The answer: Yes, but extremely dangerous.
Because computer-generated randomness is truly random, while humans choosing words almost always introduce patterns (common words, habitual choices, sequence preferences), drastically reducing the search space and making your recovery phrase easier to guess.
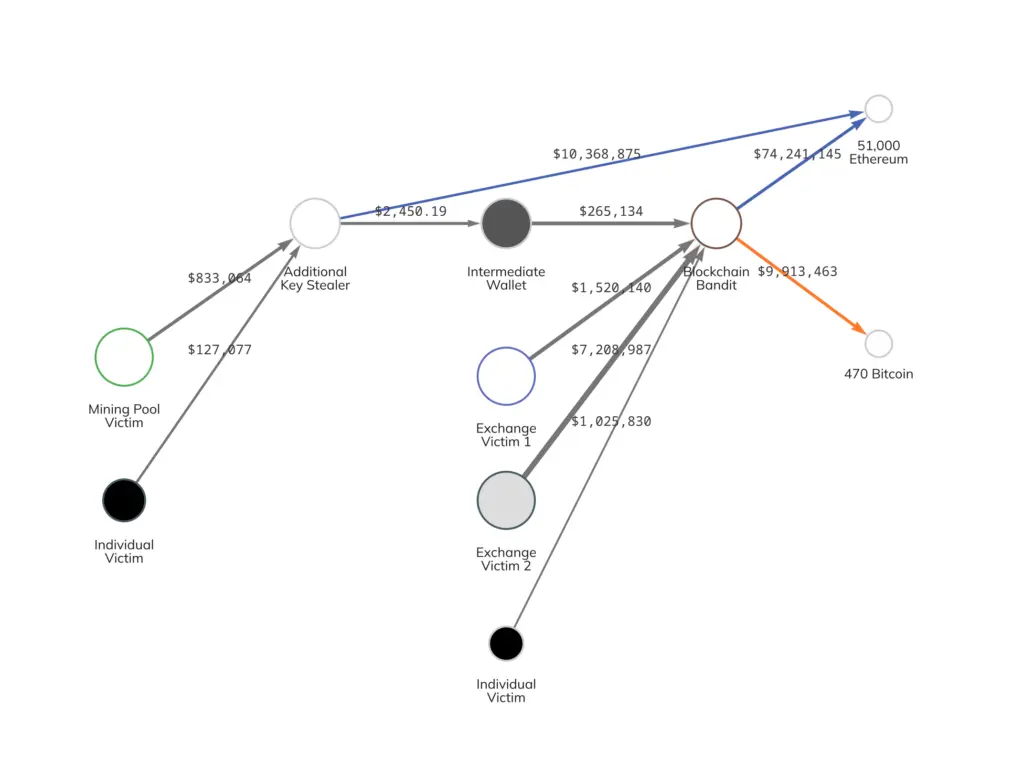
There have been past security incidents involving "pseudo-random wallets," where some wallets used pseudo-random algorithms to generate recovery phrases, resulting in severely insufficient entropy. Hackers were able to brute-force and exhaustively crack them—in 2015, the hacker group Blockchain Bandit exploited faulty random number generators and code vulnerabilities to systematically hunt weak-security private keys, successfully uncovering over 700,000 vulnerable wallet addresses and stealing more than 50,000 ETH.
Of course, some tech enthusiasts may roll dice (ensuring the dice are perfectly balanced) to generate randomness, then map results to the BIP39 word list—this could count as secure manual generation. But for most people, it's unnecessary and complicated, increasing the risk of mistakes.
3. Can You Brute-Force V God’s or Other Whales’ Wallets?
I used to fantasize about this too—imagining I generate a wallet one day and find millions of ETH inside, instantly becoming wealthy, effectively robbing some whale.
Admittedly, just thinking about it is tempting. But reality: the probability is virtually zero.
Why? Because the number of possible recovery phrase combinations is so astronomically large it defies human imagination:
-
12 words: ~2¹²⁸ ≈ 3.4 × 10³⁸ valid combinations
-
24 words: ~2²⁵⁶ ≈ 1.16 × 10⁷⁷ valid combinations
How big is this scale?
We all know sand on Earth is countless, but scientists have estimated an approximate total: assuming all beaches and deserts combined, Earth has roughly 7.5×10¹⁸ grains of sand. This means:
-
The number of valid 12-word combinations is about 4.5 × 10¹⁹ times the total number of sand grains on Earth
-
The number of valid 24-word combinations is a staggering 1.5 × 10⁵⁸ times the total sand grains
In other words, it's like each grain of sand on Earth turns into a whole new Earth, each filled with its own beaches and sand, and you must randomly pick out one specific grain pre-marked across all these countless worlds.
This scale far exceeds anything humans can comprehend.

Therefore, the probability of brute-forcing a wallet isn't merely "extremely low"—under known physics and computing capabilities, it's effectively zero. Dreaming of getting rich by "brute-forcing" is less realistic than buying a lottery ticket—you've got better odds winning the lottery.
Back to the movie scenario: if someone really only lacked one recovery phrase word, brute-forcing attempts would indeed be feasible.
Finally, a few security tips regarding wallets/recovery phrases/private keys:
-
Prioritize non-custodial wallets that have been tested over time and market-proven, with open-source code audits, such as MetaMask, Trust Wallet, SafePal, etc.; hardware wallets are recommended if possible;
-
Never screenshot, never store in cloud drives, never copy-paste, never share your recovery phrase or private key;
-
Best to write it down on paper (consider using stainless steel recovery phrase plates, resistant to moisture, fire, and corrosion), store securely, and keep 2–3 backups in separate locations;
-
Public keys/addresses can be safely shared—they’re your house numbers—but watch out for phishing links;
-
Use clean devices to manage wallets; avoid installing suspicious plugins or apps;
-
Remember this: Anyone asking you for your recovery phrase is 100% a scammer.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News












