
After Monero suffers 51% attack, does the Qubic community shift pressure to Dogecoin?
TechFlow Selected TechFlow Selected

After Monero suffers 51% attack, does the Qubic community shift pressure to Dogecoin?
The portability of computing power and the boundaries of security budgets are being re-examined.
Author: CoinW Research Institute

Recently, the AI blockchain Qubic reorganized Monero blocks in a short period under the "useful Proof-of-Work (uPoW)" mechanism, resulting in 60 orphaned blocks. Although whether this incident constitutes a strict 51% attack remains controversial, its market impact has gone beyond technical aspects. Uncertainty over network integrity forced exchanges to implement risk control measures, putting downward pressure on Monero's price. This attack reveals that the security budget under PoW mechanisms may be breached under external incentives, exposing structural vulnerabilities in mining power concentration and security boundaries.
More notably, Qubic's community voting subsequently listed Dogecoin—valued at over $35 billion—as a potential attack target. This move not only intensified market concerns but also reignited discussions about the relationship between externally incentivized mining power distribution and network integrity. The mobility of mining power and the boundary of security budgets are being re-examined. In this context, the following analysis by CoinW Research Institute offers a deeper examination of this event.
1. Qubic’s “51% Attack”: Marketing Narrative or Technical Threat?
1.1 How uPoW Breaks Traditional Security Budgets
In standard PoW architecture, the stability of mining power relies on internal chain security budgets—the closed-loop incentive formed by block rewards and transaction fees. Take Monero as an example: the network has now entered tail emission mode, with a fixed reward of 0.6 XMR per block, producing a new block approximately every two minutes, totaling around 720 blocks daily. The total security budget (approximately equal to miner block subsidies multiplied by XMR market price) is about $110,367 per day, which represents the minimum economic cost for an attacker to continuously control the majority of mining power.
Qubic introduces useful Proof-of-Work (uPoW), breaking this traditional limit. Unlike models relying solely on block rewards, Qubic provides miners with QUBIC block rewards while simultaneously directing mining power toward Monero mining. The rewards from Monero mining are converted into USDT and used to repurchase and burn QUBIC tokens on public markets. As a result, miners not only receive direct QUBIC block subsidies but also gain indirect benefits through the deflationary effects of token buybacks and burns, creating a higher overall return than mining XMR alone. This enabled Qubic to rapidly mobilize substantial mining power in a short time, causing six block reorganizations and nearly 60 orphaned blocks. In fact, as early as June this year, Qubic began mining Monero and Tari, converting the rewards into USDT for QUBIC token buybacks and subsequent burning. According to official Qubic disclosures, this mining mechanism yields over 50% higher profits compared to mining XMR and Tari individually.
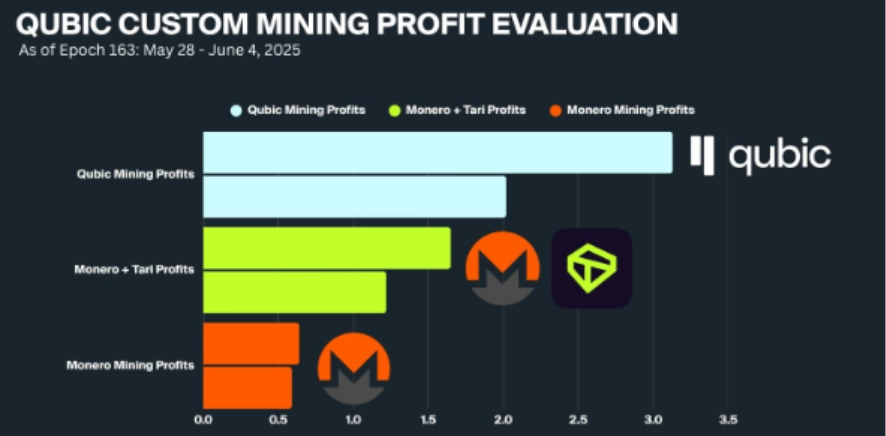
Source: qubic.org
1.2 Doubts Surrounding Qubic’s 51% Attack Claim
Although Qubic claims to have executed a "51% attack" on Monero, this assertion has been questioned by the community. According to public data from research institute RIAT, Qubic’s peak hash rate was only about 2.6 GH/s, while Monero’s global network hash rate stood at approximately 6.25 GH/s during the same period. In other words, Qubic’s share of mining power was less than 42%, significantly below the threshold required for a true 51% attack. Further data supports this assessment: CoinWarz reported that Monero’s network reached a peak of 6.77 GH/s on the day of the incident, while MiningPoolStats recorded a daily monitoring value of about 5.21 GH/s. This indicates that Qubic’s peak mining power was a transient fluctuation rather than sustained control. According to MiningPoolStats, Qubic’s current mining pool hash rate is about 2.16 GH/s, accounting for 35.3% of the network. These discrepancies suggest instability in Qubic’s control capability and lack of persistent dominance.
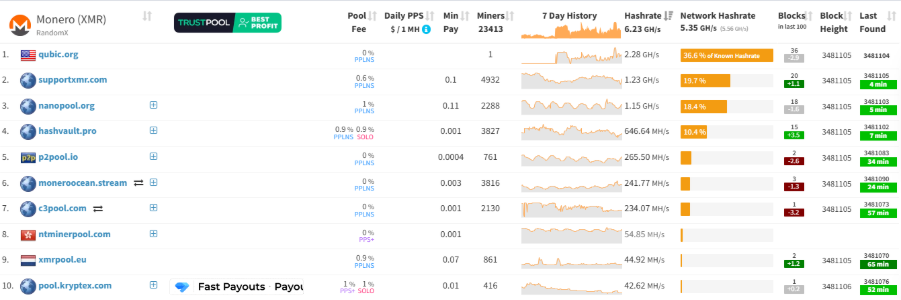
Source: miningpoolstats
Despite doubts over majority control, Monero’s network security was not materially compromised. However, Qubic’s mining power disturbance impacted the market in the short term. Kraken suspended XMR deposits due to network integrity risks, later resuming with an increased confirmation threshold of 720 blocks and retaining the right to suspend again. This shows that even without a genuine 51% attack, the mere possibility of computational manipulation can strain exchange security protocols, challenging both liquidity and confidence.
2. Dogecoin Emerges as Next Potential Target
2.1 Dogecoin as the Next Potential Attack Target
Following Monero, Qubic has set its sights on Dogecoin as the next potential target. Recently, Qubic’s community launched a vote to determine the next possible 51% attack candidate. The final results showed Dogecoin receiving over 300 votes, significantly outpacing alternatives like Kaspa and Zcash. This vote drew market attention, indicating that Qubic’s focus has shifted from privacy coins like Monero to a mainstream meme coin with a larger market cap and broader user base.
Qubic has attracted market attention because it demonstrated a novel economic incentive model during the Monero incident. This is not traditional hacking but rather leveraging economic incentives to "rent" mining power, thereby reshaping PoW security assumptions. If this model extends to Dogecoin, it could amplify market anxiety. Interestingly, after the vote, Qubic’s community clarified that their actions toward Dogecoin would involve mining, not "attacks." Based on Qubic’s current official stance, the event is widely interpreted as a marketing-driven maneuver rather than a purely technical attack.
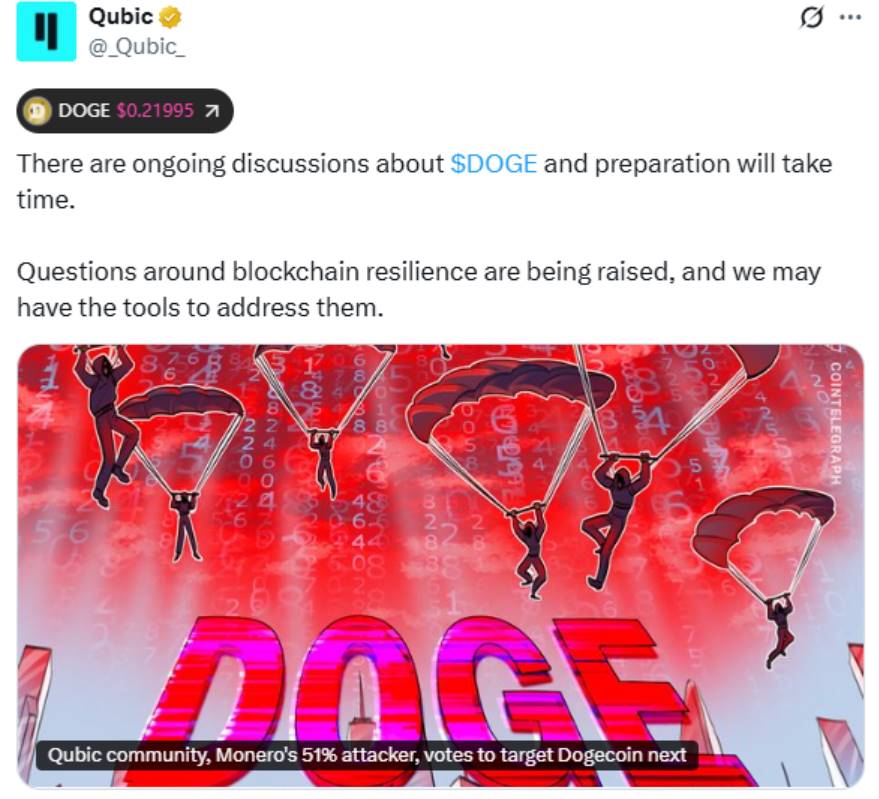
Source: @_Qubic_
2.2 Can Qubic Successfully Attack Dogecoin?
It should be noted that Qubic initially mined Monero before launching what was termed an "attack." Therefore, the community speculates that Qubic might adopt a similar approach toward Dogecoin in the future. Is this feasible? To understand the risk, one must first examine Dogecoin’s mining power scale. According to CoinWarz, Dogecoin’s current global network hash rate is approximately 2.69 PH/s, with historical highs reaching 7.68 PH/s, reflecting significant miner investment in hardware and electricity. Under its protocol, Dogecoin produces a block roughly every minute, with a fixed reward of 10,000 DOGE per block, resulting in approximately 14.4 million new DOGE entering circulation daily. At the current price of about $0.21, Dogecoin’s daily security budget totals around $3 million. By comparison, Monero in its tail emission phase adds only 432 XMR daily, corresponding to a security budget of about $110,000—far below Dogecoin’s level. This gap suggests that launching a 51% attack on Dogecoin would require substantially higher financial and technical resources than attacking Monero.
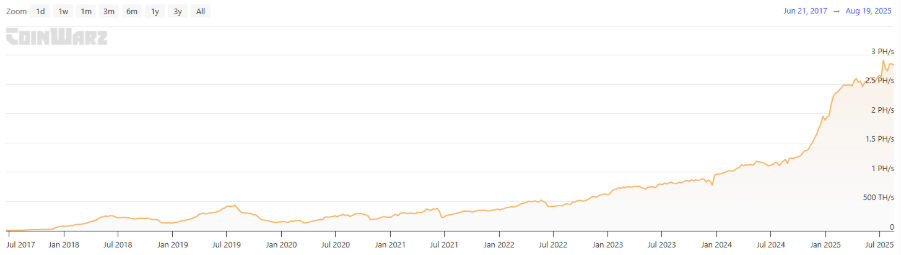
Source: coinwarz
Qubic’s strategy does not rely on massive direct funding but instead uses subsidy models to attract temporary mining power migration. If, in the short term, enough miners are incentivized by QUBIC to leave other chains and redirect toward Dogecoin, it could still disrupt block production stability. Even if double-spending cannot be truly achieved, such activity might increase block latency and orphan rates, interfering with normal network operations. It could be said that Qubic’s attack does not need to "succeed"—merely creating chaos may be sufficient to undermine market confidence.
3. Qubic Incident and the New Game Theory of PoW in the Age of AI Computing Power
3.1 Miner Liquidity and the Loyalty Dilemma
Traditional PoW consensus relies on the logic that mining power equals security—the higher the mining power, the greater the cost to attack the network, forming a solid moat. However, the Qubic incident exposes a new reality: mining power is not permanently locked to any single chain but is a resource that can quickly shift, be rented, or even speculated upon. When mining power becomes highly liquid, it behaves more like mobile capital in financial markets, flowing instantly toward higher-return opportunities.
This liquidity fundamentally alters the relationship between miners and networks. Historically, miner incentives came primarily from block rewards and fees, creating long-term alignment with a specific chain. Under the Qubic model, however, miner revenue streams are redefined, gradually transforming miners into arbitrageurs of computing power rather than long-term guardians of any particular chain.
A deeper implication is that the security of PoW networks will no longer depend solely on the scale of mining power, but on its stability. Once mining power can be lured away by higher bidders, the cost of attacking a network ceases to be a static figure and instead becomes highly sensitive to fluctuations in external markets. Consequently, PoW is no longer a robust security foundation but evolves into a temporary defense subject to dynamic market forces, with security boundaries potentially breached at any moment.
3.2 The New Game Theory of PoW in the Era of AI Computing Power
Amid surging demand for AI computing power, the security of PoW networks is being redefined. In traditional models, mining power circulates only within the chain, with security budgets entirely dependent on block rewards and transaction fees. The Qubic model demonstrates that mining power can also be directed outside the chain. For miners, computing power naturally flows toward the most profitable markets. This means that a PoW network’s security budget is no longer a static internal cost but is linked to the global computing power market—and could even collapse suddenly when AI computing prices spike.
Under these conditions, PoW may serve only as a transitional solution for AI blockchains in the short term. Relying solely on PoW for security becomes unsustainable amid long-term mining power outflows. More projects may eventually shift toward PoS or hybrid consensus mechanisms. The ability to smoothly transition consensus mechanisms could become a key factor in assessing the long-term competitiveness of AI+PoW blockchains.
Meanwhile, external security bonding is emerging as a more viable path for PoW-AI integrated blockchains. For instance, through security leasing markets similar to EigenLayer’s restaking mechanism, staked capital from Ethereum could be outsourced to AI blockchains, providing them with more stable and attack-resistant security budgets. In this model, security no longer depends on native mining power scale but leverages the long-term security of established networks to hedge against mining power liquidity risks—a promising direction for AI blockchains to overcome PoW limitations.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News















