
How XT.COM Protects User Security: Comprehensive Defense Against Cyber Threats
TechFlow Selected TechFlow Selected

How XT.COM Protects User Security: Comprehensive Defense Against Cyber Threats
An in-depth analysis of XT.COM's security mechanisms, the November 2024 security incident, and future user fund protection strategies, along with a comparative perspective from historical hacking incidents.
Key Takeaways
-
Enhanced security measures: XT.COM employs two-factor authentication (2FA), cold wallet storage, reserve funds mechanisms, and penetration testing to comprehensively protect user assets from cyberattacks.
-
Response to the November 2024 security incident: Despite a $1.7 million security breach, XT.COM quickly suspended withdrawals, ensured user asset safety, and launched an investigation to prevent future incidents.
-
Industry context comparison: Compared to hacks at Mt. Gox, Coincheck, and KuCoin, the XT.COM incident was relatively small in scale, highlighting the effectiveness of its security mechanisms.
-
Future security upgrades: XT.COM plans to introduce Merkle Tree proof-of-reserves, enhance wallet security, and deepen collaboration with cybersecurity agencies to further safeguard user assets.

The cryptocurrency trading market is rapidly evolving, attracting numerous investors while also becoming a target for cybercriminals. For exchanges, a robust security system not only protects user funds but also maintains market trust and meets regulatory requirements. Founded in 2018 and registered in Seychelles, XT.COM has listed over 1,000 digital assets and continues to strengthen its security defenses.
This article provides an in-depth analysis of XT.COM's security mechanisms, the November 2024 security incident, and future strategies for protecting user funds, along with comparative insights from historical hacking events.
Why Exchange Security Is Crucial
Cryptocurrency exchanges typically manage large amounts of funds, making them prime targets for hackers. A security breach can lead to massive financial losses, severely damage user confidence, and even destabilize the entire crypto market. Additionally, global regulators are imposing increasingly strict requirements on exchanges, with more countries enforcing anti-money laundering (AML) and Know Your Customer (KYC) regulations to build a safer trading environment.
As a fast-growing trading platform, XT.COM has invested heavily in security audits and real-time defense systems to counter potential cyber threats. In an era of rapid technological advancement, new vulnerabilities constantly emerge, requiring constant vigilance and continuous reinforcement of security measures to stay ahead of cybercriminals.

Image Credit: Token Metrics
About XT.COM
Founded in 2018 and based in Seychelles, XT.COM quickly attracted global traders. The platform offers over 1,000 digital assets, including major cryptocurrencies such as Bitcoin (BTC) and Ethereum (ETH), as well as emerging tokens, catering to diverse investor needs.
Core features:
-
User-friendly interface: Suitable for both beginners and professional traders, providing an intuitive experience.
-
Diverse trading options: Offers a wide range of trading pairs, enabling users to flexibly participate in market activities.
-
Competitive trading fees: Supports retail and institutional traders by reducing transaction costs.
-
Professional customer support: Provides an online help center and live customer service to ensure timely assistance.
Despite its many advantages, XT.COM’s core competitiveness lies in its strong security framework, including multi-layered authentication and strict fund storage management, ensuring the safety of user assets.
XT.COM's Core Security Measures
Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a simple yet powerful security measure that significantly reduces the risk of account theft. XT.COM supports multiple 2FA options, including:
-
Google Authenticator: App-based dynamic verification codes generate unique passwords for each login, greatly reducing the likelihood of account hijacking.
-
SMS and email verification: Sends one-time codes via SMS or email, adding an extra layer of protection.
Compared to SMS verification, Google Authenticator better protects against phishing attacks and SIM-swap risks. Regardless of the chosen method, enabling 2FA is fundamental to securing accounts. XT.COM strongly recommends all users enable 2FA immediately after registration and regularly review and update their security settings to minimize risks from lost or compromised devices.
Cold Wallet Storage
XT.COM stores the majority of user assets in cold wallets—fully offline wallet systems that prevent hackers from accessing funds through network attacks. Only a minimal amount of funds is kept in hot wallets for daily trading and withdrawals, minimizing the risk of large-scale theft.
Effective implementation of cold wallets relies on several key factors:
-
Secure storage environment: Offline devices are stored in encrypted data centers or isolated computers.
-
Strict access control: Only a limited number of highly authorized personnel have access to private keys.
-
Regular audits: Ensures that funds in cold wallets match recorded balances.
While cold wallets may slightly slow withdrawal speeds, they remain one of the industry’s most widely recognized best practices for security.
Reserve Insurance Fund
XT.COM has established a reserve insurance fund to protect user assets and provide liquidity support during emergencies. The platform ensures its reserves reach 1.5 times the total user deposit value to handle unexpected situations.
The fund serves several key functions:
-
Emergency compensation: In the event of a hack or market anomaly, XT.COM can use the fund to cover losses.
-
Risk mitigation: Maintains market stability and prevents financial crises triggered by unforeseen events.
While reserves cannot directly prevent security breaches, they offer additional protection when incidents occur, reflecting XT.COM’s commitment to user security.
Anti-Money Laundering (AML) and Know Your Customer (KYC) Mechanisms
To comply with global regulations and combat illegal activities, XT.COM strictly enforces Anti-Money Laundering (AML) and Know Your Customer (KYC) policies. Users are typically required to complete the following steps:
-
Submit personal identification documents (e.g., passport, driver’s license, or national ID).
-
Provide proof of address or other necessary documents (e.g., bank statements, utility bills).
-
Undergo ongoing monitoring, as the platform automatically detects and reviews suspicious transactions.
These measures aim to identify and prevent fraudulent activities such as money laundering and terrorist financing. Although AML and KYC procedures add steps during account registration and trading, they are essential for enhancing overall security and creating a safer environment for compliant traders.
Penetration Testing and Bug Bounty Programs
According to CER.live, a specialized agency evaluating cryptocurrency exchange security, XT.COM scores 76 out of 100. This score reflects the exchange’s ongoing investment in penetration testing and bug bounty programs:
-
Penetration Testing: Professional security teams simulate hacker attacks to proactively identify exploitable vulnerabilities and patch them promptly.
-
Bug Bounty: XT.COM offers rewards to independent security researchers who report system vulnerabilities, allowing the exchange to fix issues before exploitation.
These initiatives enable XT.COM to maintain constant awareness of emerging cybersecurity threats and ensure its defenses consistently stay ahead of potential attackers, continuously strengthening its protective capabilities.
Review of the November 2024 Security Incident
Despite multiple security safeguards, XT.COM experienced a significant security incident in November 2024, during which hackers unauthorizedly transferred approximately $1.7 million worth of crypto assets. These stolen funds were eventually converted into 461.58 ETH (Ethereum) and transferred to an external wallet.
Incident Response and Risk Control
Upon detecting the anomaly, XT.COM immediately suspended all withdrawals to prevent further losses. This swift action successfully minimized the potential impact of the attack.
Simultaneously, XT.COM assured the community that the compromised funds came from its reserve pool rather than individual user wallets, confirming that user assets were not directly affected. The exchange also pledged to conduct a full investigation and emphasized that its reserves still stood at 1.5 times the total user deposits, ensuring financial stability.
Investigation and Lessons Learned
After containing the attack, XT.COM collaborated with cybersecurity experts and possibly law enforcement agencies to launch a thorough investigation, aiming to:
-
Identify the vulnerability: Determine how hackers breached XT.COM’s defenses and extracted funds.
-
Prevent recurrence: Patch security flaws and reinforce internal security protocols.
-
Maintain transparency: Regularly publish investigation updates to the public, fostering trust through open communication.
This incident highlighted the complexity of securing crypto assets—even with multi-layered protections, exchanges may still fall victim to sophisticated hackers. It serves as a reminder that security systems must be continuously optimized and upgraded to keep pace with evolving cyber threats.
Historical Security Incidents in Cryptocurrency Exchanges: A Comparative Analysis with XT.COM
While any security breach warrants attention, placing XT.COM’s November 2024 incident within a broader historical context helps assess its severity. Over the past decade, several major crypto exchanges have suffered severe hacks resulting in massive losses, including:
-
Mt. Gox (2014): Considered the most infamous hack in cryptocurrency history. Mt. Gox lost 850,000 BTC, valued at hundreds of millions of dollars at the time and worth tens of billions today.
-
Coincheck (2018): The Tokyo-based exchange lost approximately $530 million worth of NEM (XEM) tokens, making it one of the largest monetary losses in hacking history.
-
KuCoin (2020): Hackers stole around $275 million in various cryptocurrencies. Although KuCoin recovered part of the funds, it remained a serious security incident.
-
Poly Network (2021): As a cross-chain protocol, Poly Network lost over $600 million in digital assets during the attack. While most funds were later returned through negotiations, the event underscored the high risks associated with DeFi platforms.
The losses from these incidents ranged from hundreds of millions to tens of billions of dollars, illustrating the immense security challenges facing crypto exchanges. In contrast, XT.COM’s $1.7 million loss, while significant, was relatively minor in scale, indicating that its security infrastructure still possesses a certain level of resilience. Moreover, XT.COM's prompt response—including freezing withdrawals, deploying reserve funds to cover losses, and launching a comprehensive investigation—demonstrated effective risk control and crisis management capabilities.

Image Credit: Bitcoin.com
Future Security Upgrade Plans
Merkle Tree Proof-of-Reserves
XT.COM plans to implement a Merkle Tree proof-of-reserves mechanism, allowing users to independently verify the exchange’s on-chain assets without exposing sensitive information. This increased transparency will enhance user confidence in the exchange’s solvency.
Ongoing Infrastructure Optimization
XT.COM is implementing a series of security enhancements to further strengthen platform defenses, including:
-
Enhanced hot wallet security: Introducing multi-signature mechanisms to require multi-party authorization for large withdrawals, reducing the risk of single-point attacks.
-
Real-time threat detection: Deploying advanced firewalls and intrusion detection systems to monitor and block suspicious activities, preventing cyberattacks.
-
Access control and employee training: Restricting access to critical systems and conducting regular security training to defend against social engineering attacks (e.g., phishing scams).
Strengthening Collaboration with Cybersecurity and Law Enforcement Agencies
Besides internal upgrades, XT.COM will deepen cooperation with cybersecurity firms and law enforcement to improve threat monitoring and asset recovery capabilities.
-
Threat intelligence sharing: Collaborating with leading global security teams to obtain the latest hacking trends, enabling proactive identification and prevention of emerging threats.
-
Enhanced fund tracking and recovery: Partnering with law enforcement to increase success rates in tracing and recovering stolen funds.
-
Continued expansion of bug bounty programs: Encouraging global security researchers to proactively discover and report vulnerabilities, allowing XT.COM to fix issues preemptively rather than reactively.
These measures will help XT.COM maintain a leadership position in security, ensuring the platform continuously adapts to evolving threats and delivers a safer trading environment for users.
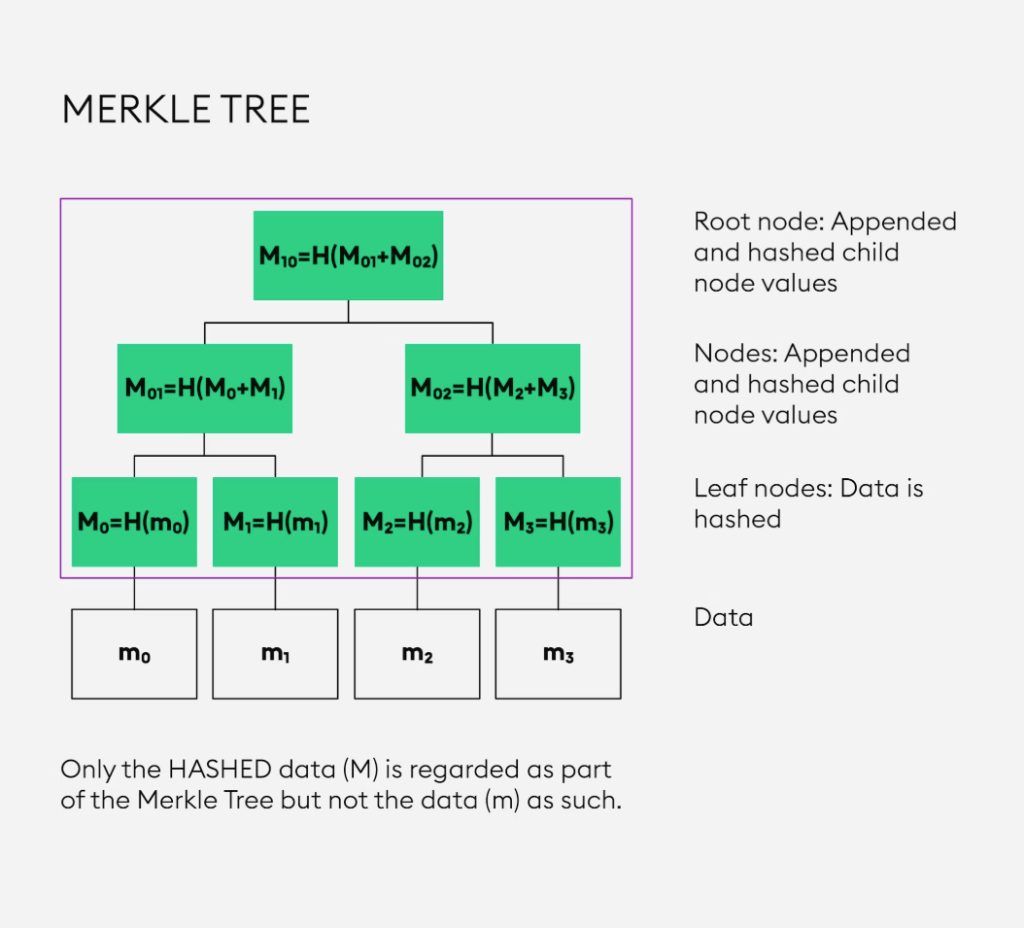
Image Credit: BitPanda
User Guide: How to Enhance Personal Account Security
Even with robust exchange-level security, user habits play a vital role. Below are key recommendations to effectively enhance account security:
-
Enable Two-Factor Authentication (2FA): Prefer Google Authenticator over SMS, as it better protects against phishing and SIM-swap attacks.
-
Use strong, unique passwords: Ensure passwords include uppercase and lowercase letters, numbers, and special characters, and avoid reusing passwords across sites or apps.
-
Beware of phishing attempts: Avoid clicking suspicious links and always verify URLs before entering account credentials.
-
Regularly monitor account activity: Check login logs, transaction history, and withdrawal records; if anomalies are detected, change your password immediately and contact official support.
-
Stay informed: Follow XT.COM’s official announcements for the latest security tips and risk alerts.
Balancing Innovation and Risk Management
The November 2024 hacking incident proved that even exchanges with multi-layered defenses can fall victim to advanced attacks. However, XT.COM’s rapid response—freezing withdrawals, using reserve funds to compensate losses, and launching a comprehensive investigation—demonstrated its transparency and commitment to user protection.
Going forward, XT.COM will continue upgrading its security systems, including implementing Merkle Tree proof-of-reserves and optimizing infrastructure, signaling its recognition that security is not static but requires continuous evolution. In the fast-changing crypto market, XT.COM must continuously assess new risks, test security defenses, and adapt operational strategies to ensure user asset safety and maintain competitiveness.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















