Q3 Security Report Reveals | $740 Million Lost Across Blockchain Networks, Nearly Half Due to Phishing Scams
TechFlow Selected TechFlow Selected

Q3 Security Report Reveals | $740 Million Lost Across Blockchain Networks, Nearly Half Due to Phishing Scams
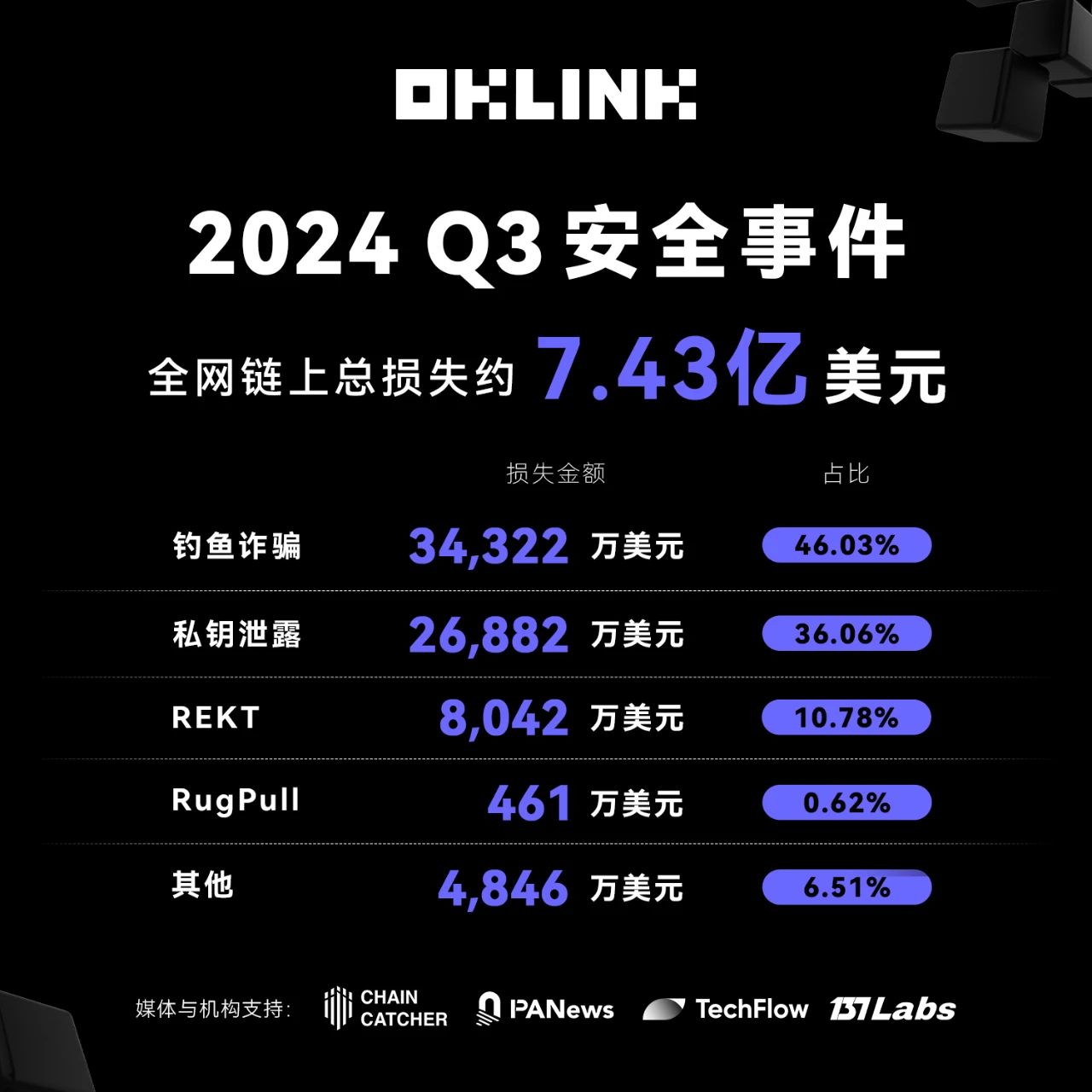
In Q3 2024, the total on-chain losses across the entire network amounted to approximately $743 million, an increase of 58% compared to the previous quarter. A total of 110 major security incidents occurred, including 61 fraud and phishing events, which resulted in losses of $340 million, accounting for 46.03% of the total losses.
In Q3 2024, the total on-chain losses across the entire network amounted to approximately $743 million, a 58% increase quarter-on-quarter. A total of 110 major security incidents occurred, including 61 scams and phishing attacks resulting in losses of $340 million, accounting for 46.03% of total losses.
According to data from OKLink, losses due to private key leaks reached about $270 million, representing 36.06% of total losses. REKT incidents caused losses of around $80.42 million, or 10.78%, while RugPull events led to losses of approximately $4.61 million, accounting for 0.62%.
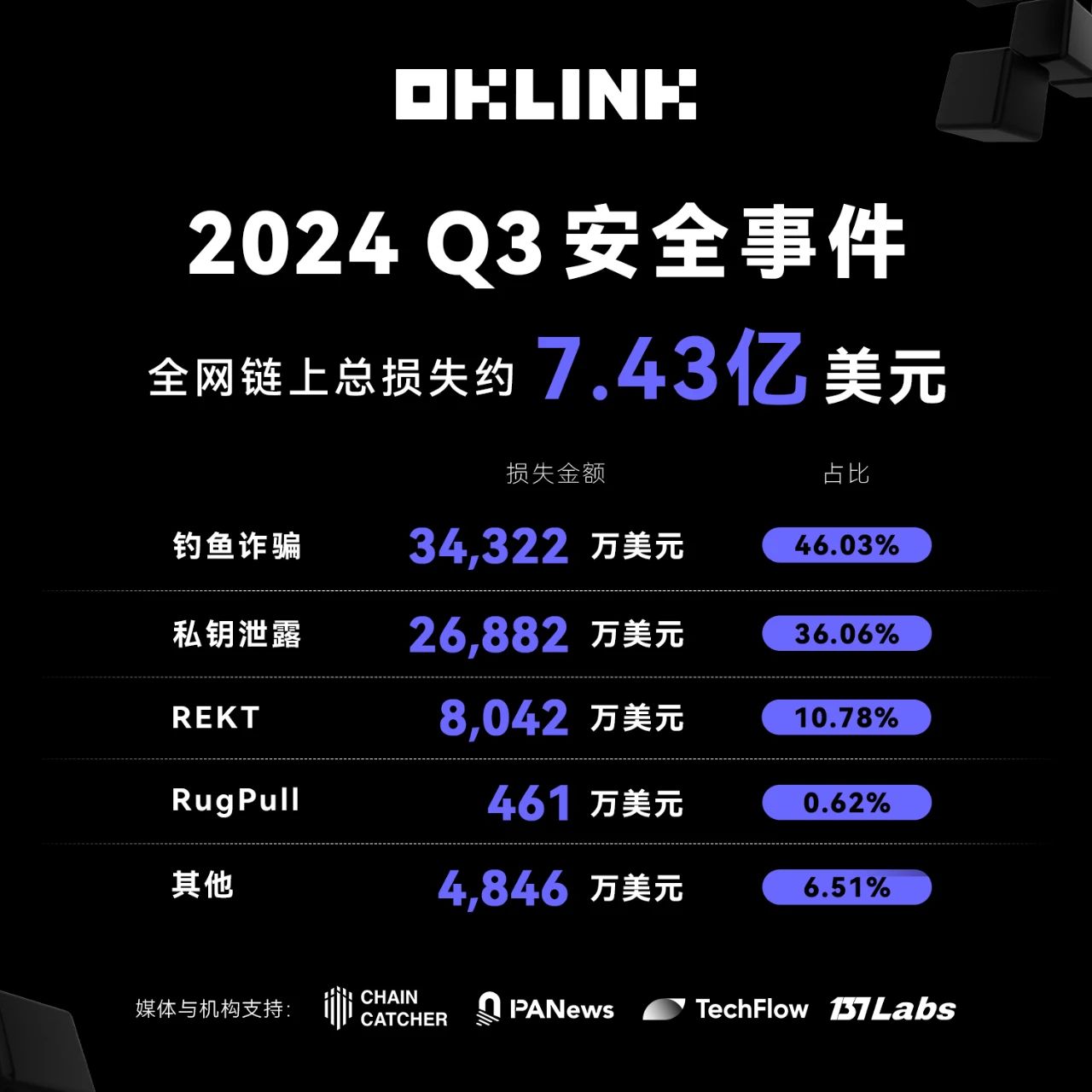
During July and August, each month saw roughly $300 million in significant losses. In September, however, total losses dropped sharply by 57%. Despite this decline, threats such as phishing attacks and private key leaks remain prevalent. These security incidents are highly unpredictable and continue to pose serious risks. OKLink urges users to enhance their security awareness and never trust unverified signature requests—especially when authorizing "Permit" functions or transferring funds—always verify the authenticity of signatures.
Additionally, securely store your private keys and recovery phrases. Never disclose them to anyone, nor save them via screenshots or on insecure devices.
Largest Security Incident - Phishing Scam
On August 19, a potential victim reportedly lost 4,064 BTC, worth approximately $238 million, likely due to a phishing attack. After the theft, the stolen funds were quickly transferred through multiple platforms including ThorChain, eXch, Kucoin, ChangeNow, Railgun, and Avalanche Bridge in complex transactions.
Largest Security Incident - Private Key Leak
On July 18, WazirX exchange suffered a loss of approximately $235 million due to a multi-signature wallet private key leak.
Largest Security Incident - REKT
On September 3, Penpie was attacked due to a reentrancy vulnerability in its reward protocol, resulting in losses of approximately $27.34 million.
Largest Security Incident - RugPull
On July 21, ETHTrustFund executed a RugPull, stealing approximately $2 million worth of cryptocurrency on Base.
Case Analysis
On September 3, Penpie's contract was exploited via a reentrancy attack. During the reentrant call, the attacker added liquidity to inflate the perceived reward amount, thereby withdrawing legitimate reward tokens from the contract. The total asset loss reached $27.34 million.
1. The attacker deployed a malicious SY_1 token contract and created a fraudulent SY_1_PENDLE-LPT market on Pendle. They then used this malicious market to create a new staking pool on Penpie and deposited a large quantity of SY_1_PENDLE-LPT tokens into it;
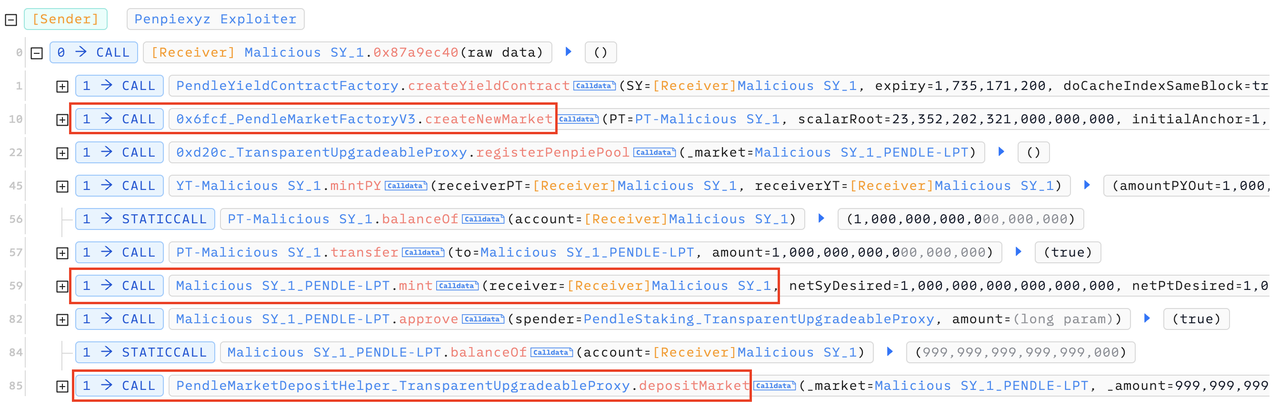
2. The attacker took out flash loans of substantial amounts of wstETH, sUSDe, egETH, and rswETH tokens, deposited them into the SY_1 token contract as if they were rewards generated by the contract. Then, they called the Penpie.batchHarvestMarketRewards function, which triggered the claimRewards function in the SY_1 token contract, expecting to receive actual reward tokens;
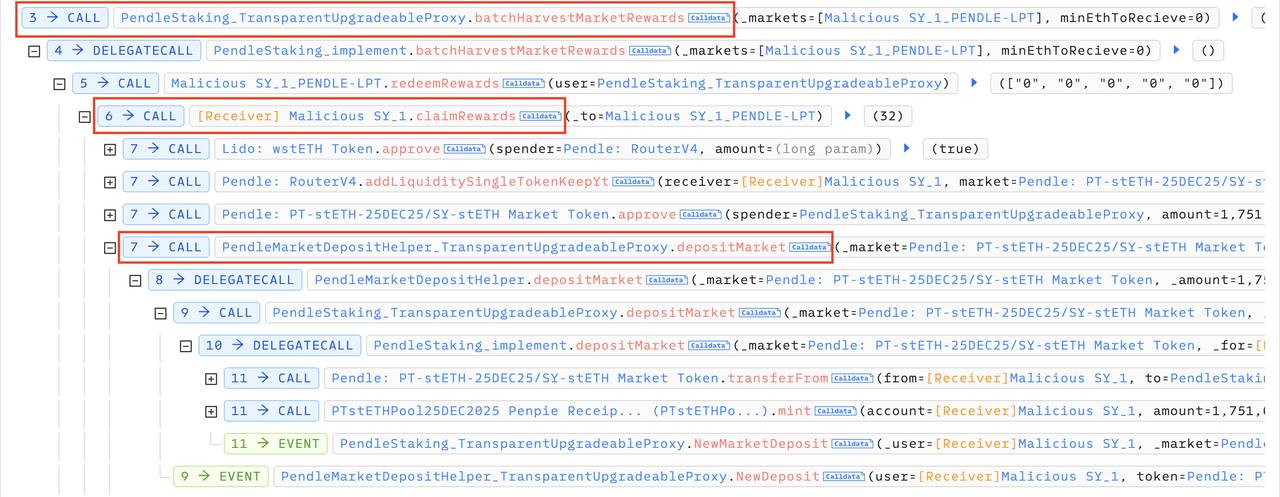
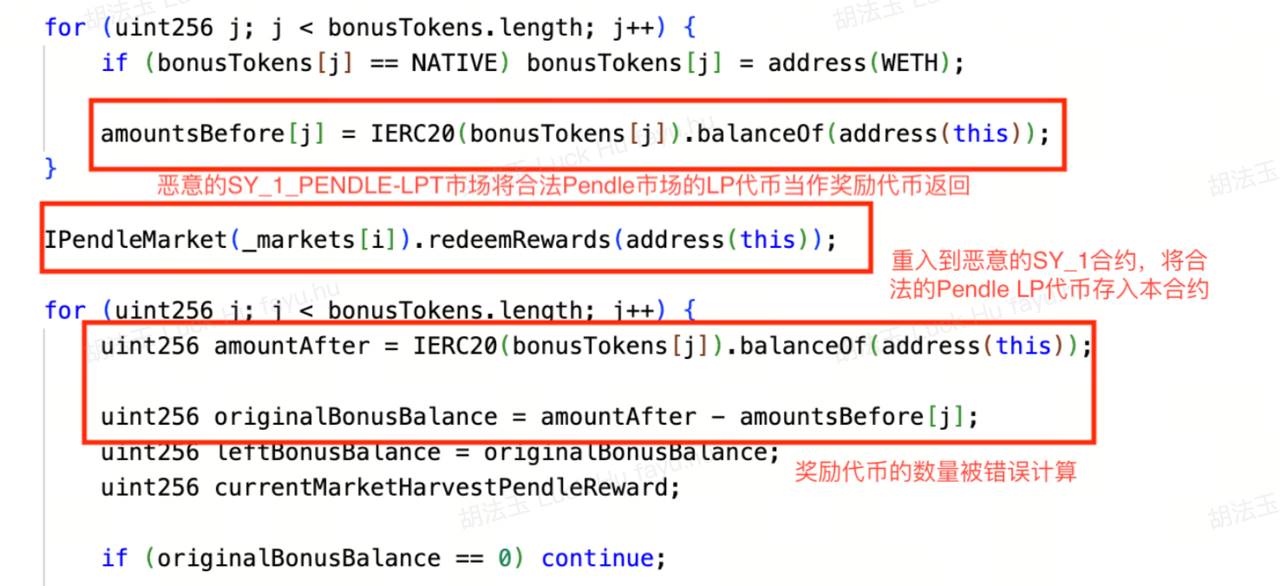
3. However, within the claimRewards function of the SY_1 token, the attacker exploited Penpie’s reentrancy vulnerability to deposit the flash-loaned wstETH, sUSDe, egETH, and rswETH tokens into corresponding Pendle markets, then deposited the received LP tokens back into the Penpie protocol.
Since this action occurred during the execution of Penpie.batchHarvestMarketRewards, Penpie incorrectly recognized these newly deposited tokens as reward tokens and sent an inflated amount of reward tokens to the RewardDistributor contract. As the sole depositor in this malicious Pendle market, the attacker was able to claim all the distributed rewards;
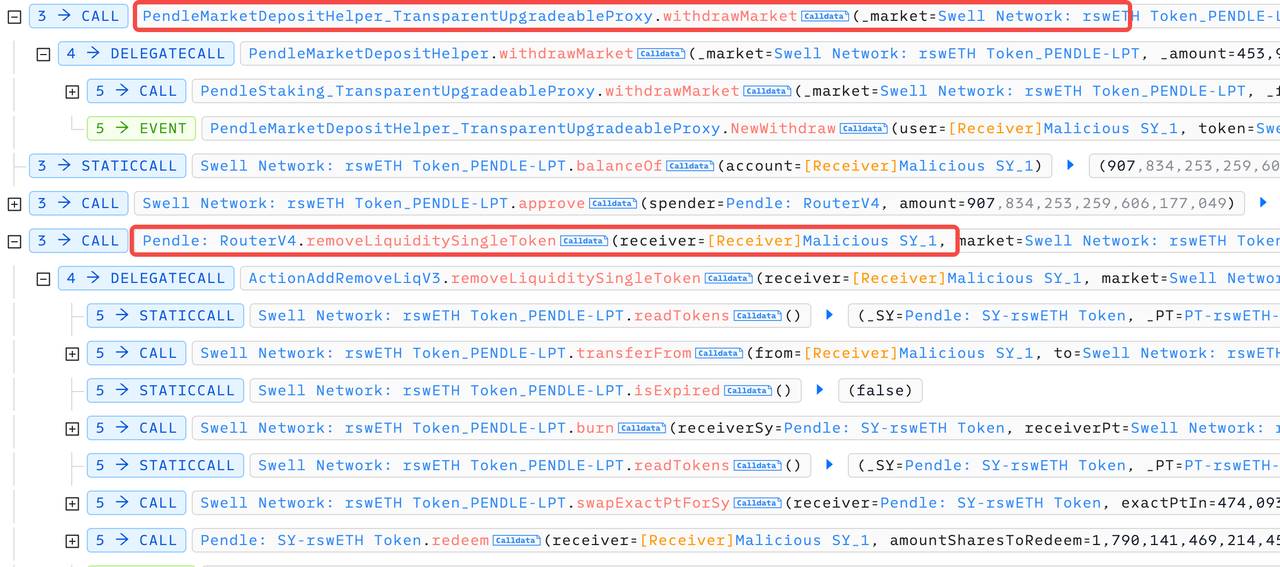
4. Finally, the attacker redeemed all Pendle-LP tokens from Penpie, then withdrew wstETH, sUSDe, egETH, and rswETH from Pendle and repaid the flash loans.
OKLink Tips
OKLink reminds users to carefully verify blockchain addresses when performing on-chain operations to avoid losses from address tampering. It is recommended to regularly review and revoke unused contract approvals to prevent abuse by malicious contracts. Use on-chain tools wisely for enhanced protection. OKLink offers features such as token approval checking, address monitoring, and contract comparison, enabling easy management of token permissions and full control over contract risks. Click the bottom-left "Read More" link at the end of this article to try it now.
Remain rational when faced with high-yield projects, especially those lacking transparency or audit reports, and be cautious of falling into RugPull and REKT traps.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News












