
Not making money yet but already scammed? Here's your guide to avoiding inscription phishing
TechFlow Selected TechFlow Selected

Not making money yet but already scammed? Here's your guide to avoiding inscription phishing
Analyze three typical NFT security cases: scam project risks, risks of mistaken transfers or accidental burns, and centralized tool risks.
Author: BlockSec
As the concept of inscriptions reaches unprecedented popularity, top-tier inscription prices have surged by as much as tens of thousands of times. In this context, many actors are already seizing opportunities to exploit the complexity and novelty of inscriptions through various fraudulent activities—an issue that is becoming increasingly rampant. These malicious behaviors not only pose serious threats to users' asset security but also negatively impact the healthy development of the entire inscription ecosystem.
To address this, we have summarized three typical inscription security cases, including Scam project risks, mistaken transfer or burn risks, and centralized tool risks, along with corresponding preventive measures users can take in these scenarios.
Scam Project Risk
In the current Bitcoin protocol, project identification primarily relies on the project name specified during the deployment (deploy) operation, with unique IDs used for indexing. However, ordinary users often remember only the project name and use it as the basis for transactions. This name-dependent transaction method carries certain risks because ASCII codes contain numerous visually similar yet distinct strings, creating opportunities for visual spoofing. Malicious actors can exploit these subtle differences to deceive users into believing they are interacting with well-known projects, while issuing counterfeit tokens that mimic legitimate ones.
Such fraud frequently occurs during the minting process. Attackers may guide users to pay fees to obtain tokens or other digital assets that are actually worthless. This type of scam not only harms individual users but could also destabilize the broader ecosystem.
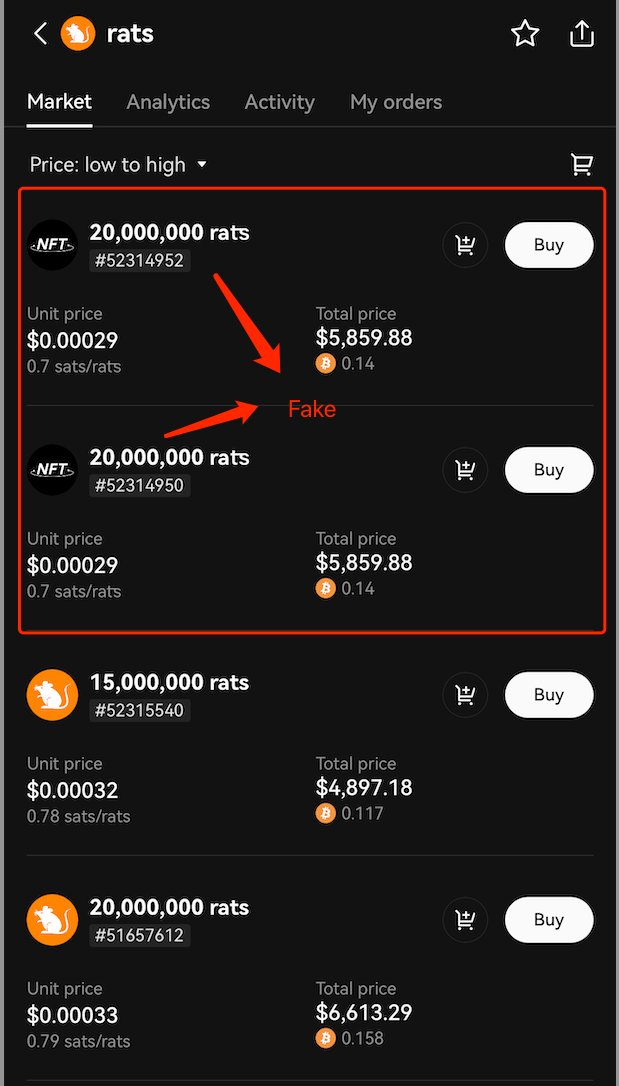
Here we present a fake "rats" example—this counterfeit version closely resembles the genuine one due to nearly identical ASCII characters. If users fail to carefully inspect the name (note the letter "t" inside "rats"), they may be misled into purchasing fake rats tokens, resulting in financial loss.
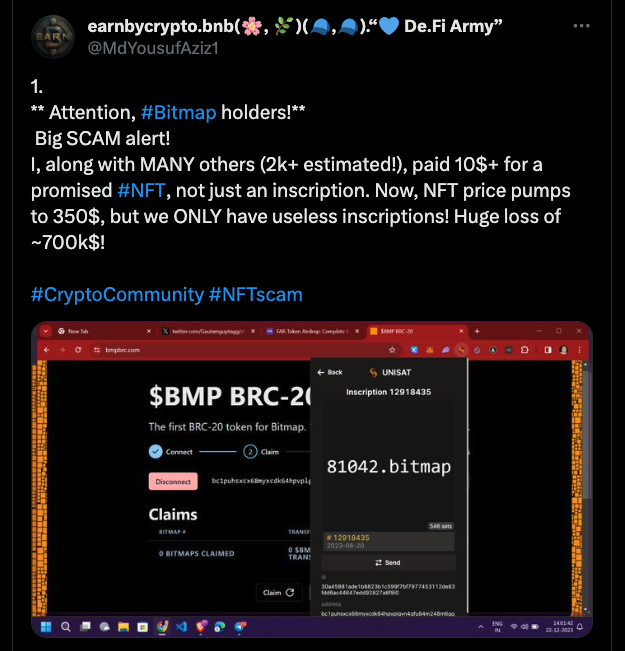
Beyond fake inscriptions, some scam inscriptions even trick users into sending additional funds during the minting process.
For instance, as shown in the image below, when minting an inscription on Bitmap, a phishing website demands extra payment to a specific address. Users who do not scrutinize the requested amount may suffer significant losses.
💡 Mitigation: Avoid minting inscriptions from untrusted sources
Currently, there are diverse channels available for minting inscriptions, including:
-
Official websites provided by project teams
-
Wallet-integrated tools like Unisat
-
Third-party auxiliary tools
The variety of inscription minting channels can confuse users, making it difficult to assess their legitimacy and safety, thus increasing vulnerability to scams. We recommend that users primarily rely on official wallets and project team websites for minting inscriptions. Always verify the correctness of URLs before minting and carefully review the required minting fee. For large-scale batch mints, we advise using trusted wallet tools to further enhance fund security.
Mistaken Transfer and Burn Risks
First, mistaken transfers refer to treating inscription-carrying UTXOs as regular Bitcoin during transfers. Since inscriptions are embedded within Bitcoin transactions, traditional BTC wallets typically ignore their added value and display only the satoshi amount locked in the UTXO model. Some users may perform standard transfer operations without fully understanding inscriptions, causing the wallet to treat the inscription as ordinary Bitcoin, merging or splitting it with other UTXOs and sending it to an incorrect address—resulting in irreversible loss.
Second, mistaken burning refers to intentionally or unintentionally destroying inscriptions under the false assumption that they carry no value or significance. Because inscriptions don't directly affect Bitcoin ownership or base value in the UTXO model, some users might mistakenly believe that Bitcoin containing inscriptions has lower paper value, deeming them unimportant or invalid, and choose to merge such UTXOs with others. This action could lead to permanent loss of valuable inscription-related data or assets.
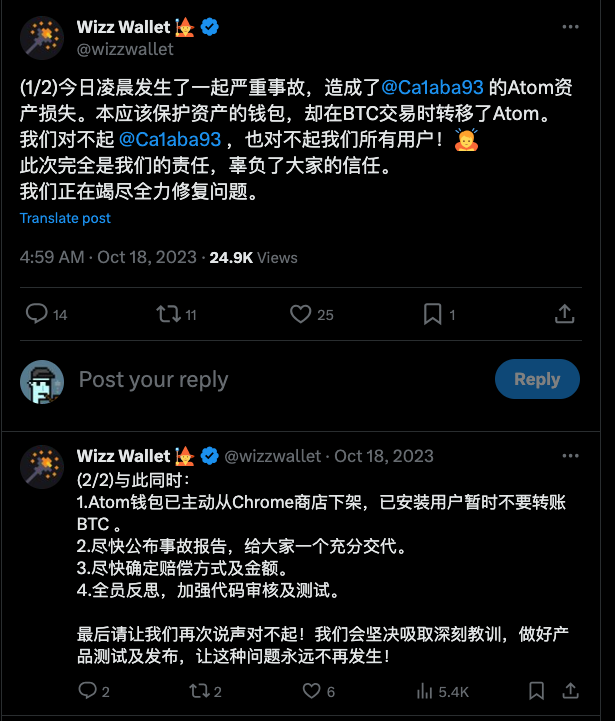
For example, as shown in the figure below, during what should have been a protective BTC transaction for an inscription, the wallet failed to recognize the inscription and incorrectly treated it as dust, transferring it away and causing loss. https://twitter.com/wizzwallet/status/1714385677985661245?s=20
💡 Mitigation: Use dedicated inscription addresses and wallets
Within the UTXO model, to prevent accidental transfer or destruction of high-value inscription assets, we recommend setting up dedicated inscription addresses and wallets. This practice effectively reduces the risk of human error and ensures better protection of inscription assets. These addresses should be clearly separated from regular transaction addresses to avoid confusion. By isolating inscription-related transactions from everyday Bitcoin usage, users can gain greater control and visibility over their inscription holdings.
Centralized Tool Risk
Blockchain’s decentralized design allows direct user participation in its ecosystem. However, directly interacting via complex RPC protocols is too technical for most people. As a result, the majority of users depend on third-party tools to participate in inscription minting and trading.
Given that inscriptions are a relatively new concept, their ecosystem remains in early stages compared to mature systems like ERC20. While auxiliary tools are rapidly emerging, most focus heavily on functionality while lacking sufficient security safeguards. Examples include tools requiring users to import private keys for signature delegation or entrust assets to platforms for trading. These practices expose users’ private keys, effectively giving centralized tools full control over user assets and introducing centralization risks such as rug pulls. Such risks resemble incidents where wallet companies, after gaining access to users’ private keys, abscond with all funds and declare bankruptcy.
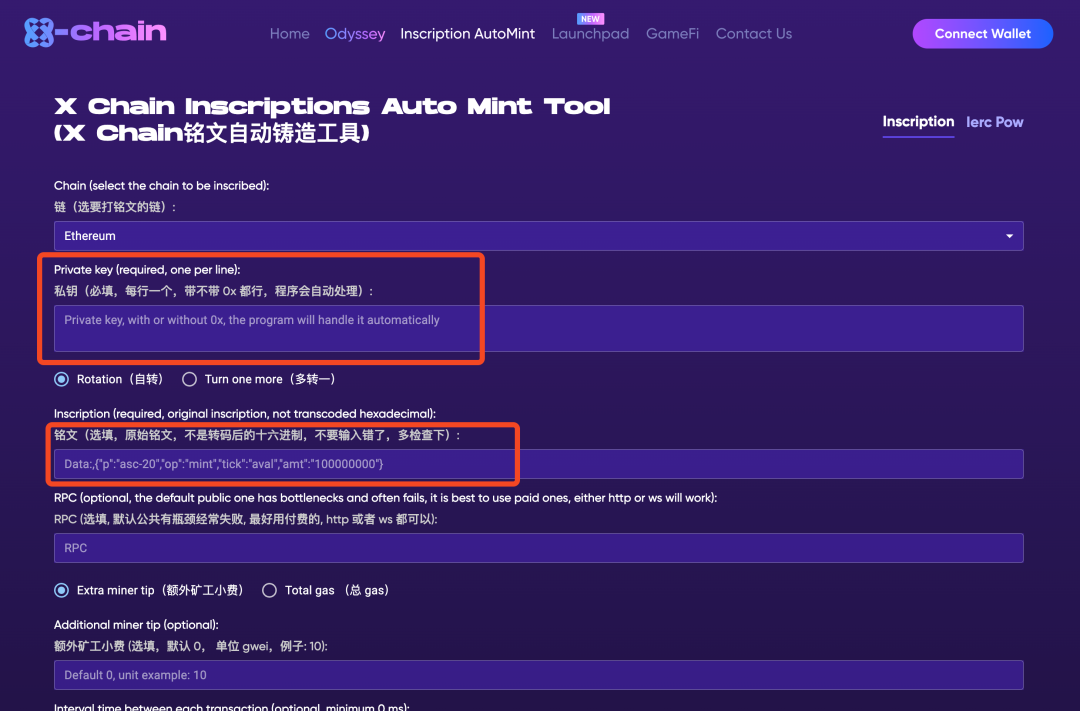
For example, the following inscription service stole users’ funds by directly accessing their private keys.
💡 Mitigation: Use secure inscription tools
To improve inscription asset security, users should conduct transactions and operations on reputable inscription marketplaces.
Examples include:
Geniidata: https://geniidata.com/Ordinals/index/brc20
Ordiscan: https://ordiscan.com/
Etch Market: https://www.etch.market/market
These widely recognized exploration and marketplace platforms provide secure trading environments and reliable inscription data. Conducting inscription minting, trading, and other activities on such trusted platforms significantly enhances user security. Additionally, users must remain vigilant and avoid blindly trusting unknown websites offering inscription minting or trading services. Before performing any action, thoroughly research and confirm the site's reputation and security. Furthermore, never disclose your private key or other sensitive information to untrusted third parties to protect against phishing or theft.
Conclusion
After examining common risks—including scam inscriptions, mistaken transfers or burns, and dangers associated with centralized tools—it becomes clear that while the inscription ecosystem holds great promise, it also presents significant risks and challenges. Users must exercise extreme caution when transacting and storing inscriptions. By using official minting channels, maintaining dedicated inscription wallets and addresses, and choosing secure auxiliary tools, users can greatly reduce exposure to threats and better safeguard their assets. Ultimately, we urge all participants to proceed with caution—when navigating the world of digital assets, security always comes first.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News












