Particle Network V2: The first intent-centric Web3 modular access layer, a groundbreaking leap prioritizing both privacy and efficiency
TechFlow Selected TechFlow Selected

Particle Network V2: The first intent-centric Web3 modular access layer, a groundbreaking leap prioritizing both privacy and efficiency
How to enhance privacy protection and interaction efficiency for users in Web3?

Bear market build, bull market breakout—this is the general consensus among most Web3 practitioners.
But the question remains: in a market environment marked by apathy, capital outflows, and lack of fundamental innovation in application models, what should one build to achieve sustained success in the next cycle? And which trends and narratives are worth paying attention to?
Perhaps insights can be drawn from several recently discussed cutting-edge topics:
-
At the beginning of the year, ERC-4337 was deployed on mainnet, bringing breakthroughs for account abstraction (AA) wallets;
-
A few months ago, Paradigm listed "intent-centric" systems as one of the ten key industry trends to watch;
-
Just days ago, Vitalik Buterin co-published a new paper with the University of Basel introducing Privacy Pool, a proposal aiming to balance user privacy and regulatory compliance through technical means...
These explorations may appear unrelated at first glance. Yet when viewed collectively, they reveal a shared underlying challenge: how to enhance both user privacy and interaction efficiency within Web3.
Currently,底层 blockchain protocols are striving to improve transaction performance; infrastructure layers are creating more stable conditions for specific application scenarios; and application layers are refining UI/UX to enhance product experiences.
But as L2s multiply, L1s accelerate, infrastructure matures, and applications proliferate—has there truly been a qualitative leap in user experience regarding comprehension cost, operational convenience, and privacy security when accessing Web3 today?
The answer is no.
Each layer independently addresses certain usability and interaction issues within their respective domains, resulting in fragmented and decentralized efforts.
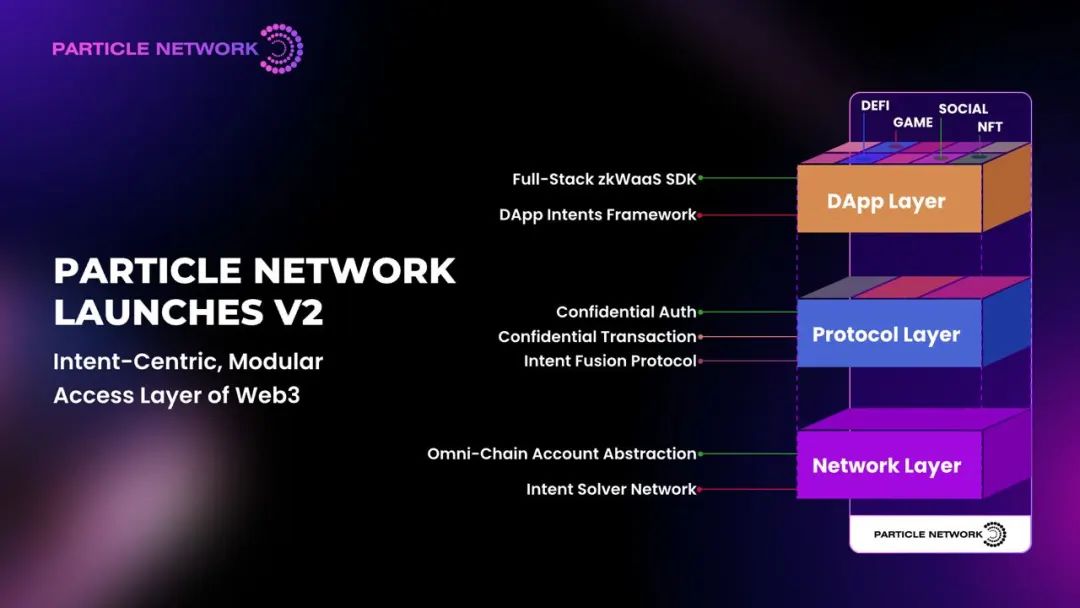
Therefore, at the InfraCon @Token 2049 developer conference held on September 12, Particle Network launched V2—an intent-centric, modular Web3 access layer. It aims to enhance the efficiency of user-chain interactions across the entire user journey, focusing on ease of onboarding, interaction efficiency, data autonomy, and modular adaptability.
In this article, we provide an in-depth analysis of Particle Network V2, examining its product evolution motivations, design logic, and potential impact, offering valuable insights for industry participants.
Particle Network V1: The WaaS-Centric Access Layer, Building the Foundation for Efficient User-Chain Interaction
Particle Network officially launched its V1 product at the end of October last year—a Wallet-as-a-Service (WaaS) solution based on MPC-TSS. When ERC-4337 went live, it also introduced an MPC+AA (Multi-Party Computation + Account Abstraction) wallet service model.
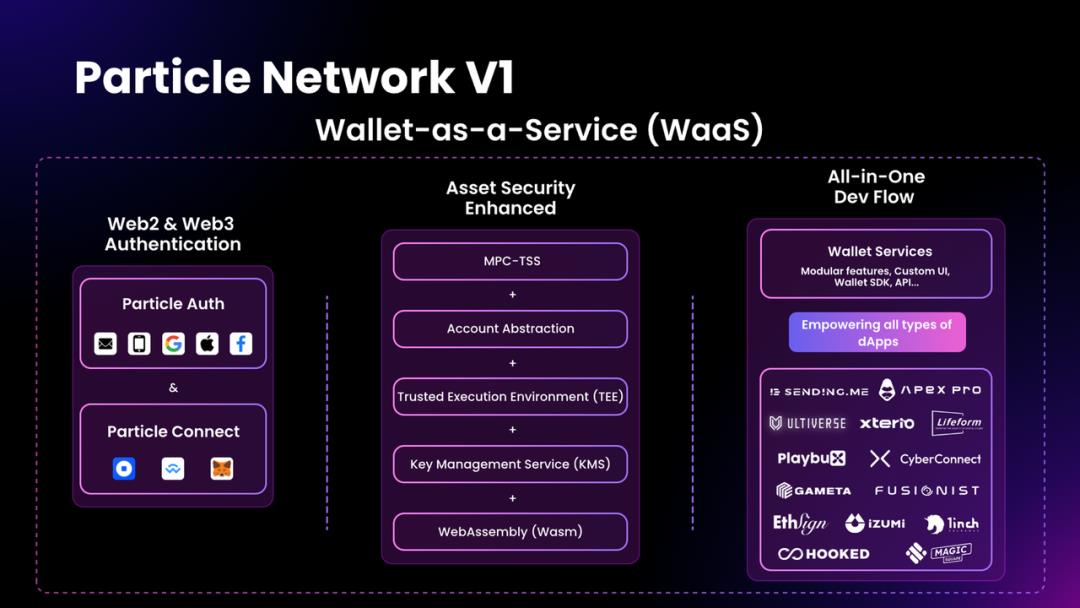
This approach brings clear benefits: users can log in using familiar Web2 methods, eliminating concerns about understanding or managing private keys and seed phrases. Leveraging MPC for secure key fragment management and execution environments, along with AA features such as unified gas payments and batch operations, significantly improves wallet usability.
From the end-user perspective, Wallet-as-a-Service (hereafter WaaS) enhances chain interaction efficiency. After social login, all blockchain signatures occur seamlessly within partner applications that have integrated WaaS, avoiding disruptive external redirects and shielding users from underlying technical complexities.
Simultaneously, from the viewpoint of Web3 projects, the WaaS model has gained widespread favor.
Within 10 months of its launch, hundreds of dApps across various categories—including Xter.io, Hooked Protocol, ApeX, 1inch, and CyberConnect—have integrated Particle Network’s products and services, covering leading projects across multiple sectors.

This represents a classic B2B2C collaboration model: Particle Network provides the WaaS solution, which project partners integrate to jointly enhance end-user experience.
Under this model, open collaboration with partners and developers becomes even more critical.
Throughout its development, Particle Network has maintained strong openness, collaborating closely with ecosystem partners like Linea and BNB Chain. Moreover, by organizing developer conferences such as InfraCon, it has connected over 500 prominent builders in the industry.
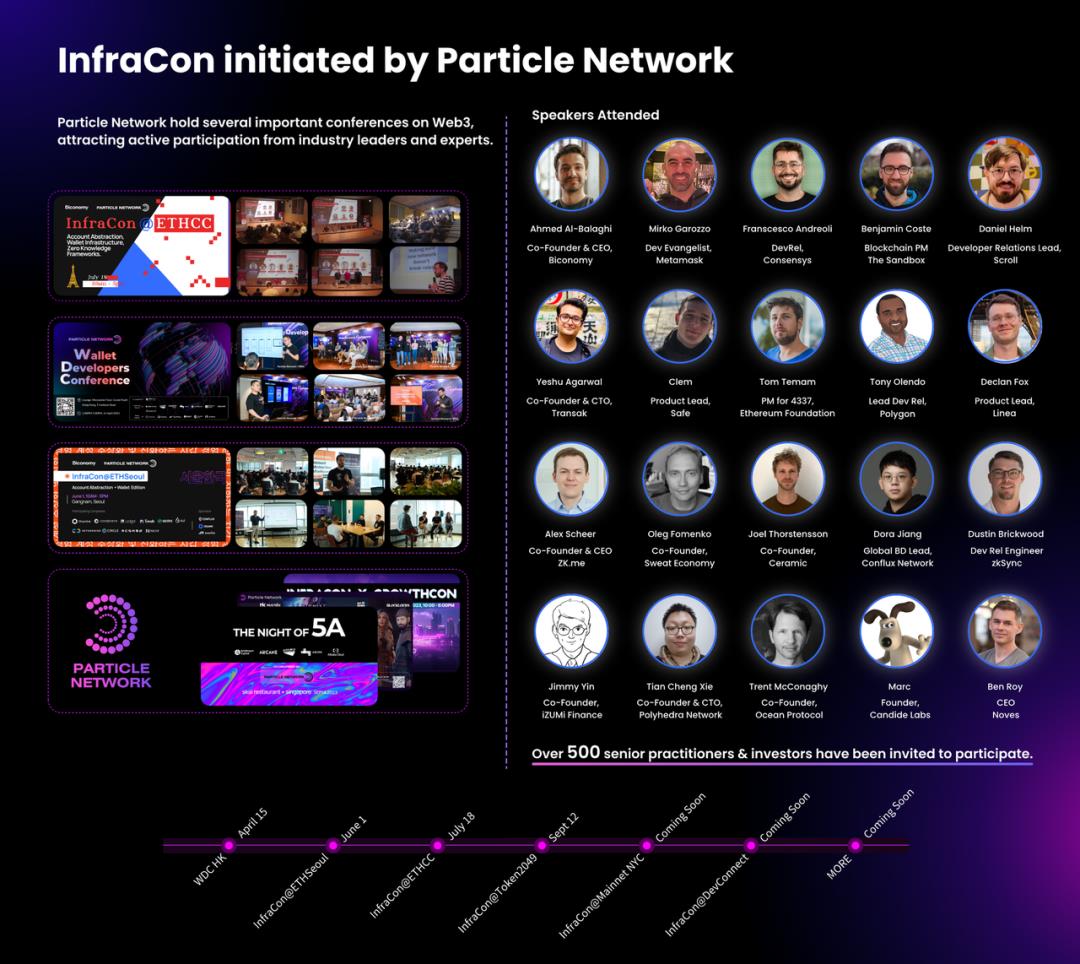
Overall, Particle Network's V1 product has effectively addressed the high barrier to entry for Web3 access and has already achieved considerable scale and industry influence.
Upholding Core Web3 Principles, Building Infrastructure for the Future
The WaaS (Wallet-as-a-Service) solution greatly simplifies user access and interaction while steadfastly adhering to core principles: preserving users' autonomy over their data and privacy.
Users retain full control over their assets, data, and privacy. Under the self-custody design of MPC-TSS, neither service providers, dApps, nor third parties can bypass the user to gain account control.
However, challenges around privacy and interaction efficiency still persist in the current WaaS landscape, including:
-
First, the mapping between Web2 social logins and Web3 on-chain wallet addresses constitutes a privacy risk and presents storage and management challenges.
-
Second, all on-chain transaction records are publicly visible. While transparency offers benefits, it also raises privacy concerns—many users do not want their transaction history freely accessible without consent.
Indeed, autonomy extends beyond just control over private keys—it encompasses users’ ability to manage their own privacy across the entire Web3 ecosystem.
With autonomy taking on broader meaning, how should future-oriented Web3 infrastructure evolve?
Considerations around these questions may differ drastically between scaling from 0 to 10 million users versus beyond that threshold.
Thus, these reflections became central to Particle Network’s product evolution: How can we lower barriers while ensuring complete user privacy and data sovereignty? And how can we increase the efficiency of fulfilling real user needs during chain interactions?
Particle Network V2: A Modular, Cross-Chain Web3 Access Layer Powered by zk and Intent Computing
The newly released Particle Network V2, unveiled on September 12, directly addresses these challenges.
First, to tackle data privacy, V2 introduces zkWaaS (Zero-Knowledge Wallet-as-a-Service).
zkWaaS builds upon V1’s MPC and AA foundations by integrating zero-knowledge proof technology stacks, enabling Confidential Login and Confidential Transaction capabilities.
The former hides the link between Web2 accounts and on-chain wallet addresses; the latter resolves the privacy issue of fully public on-chain transaction histories. Detailed implementation will be explained later.
Additionally, to address interaction inefficiency, V2 introduces the Intent Fusion Protocol.
This protocol transforms the complex series of steps currently required in Web3 interactions—such as signing, cross-chain transfers, gas conversion—into a single simplified action that directly fulfills the user’s original intent, eliminating the need for manual step-by-step execution.
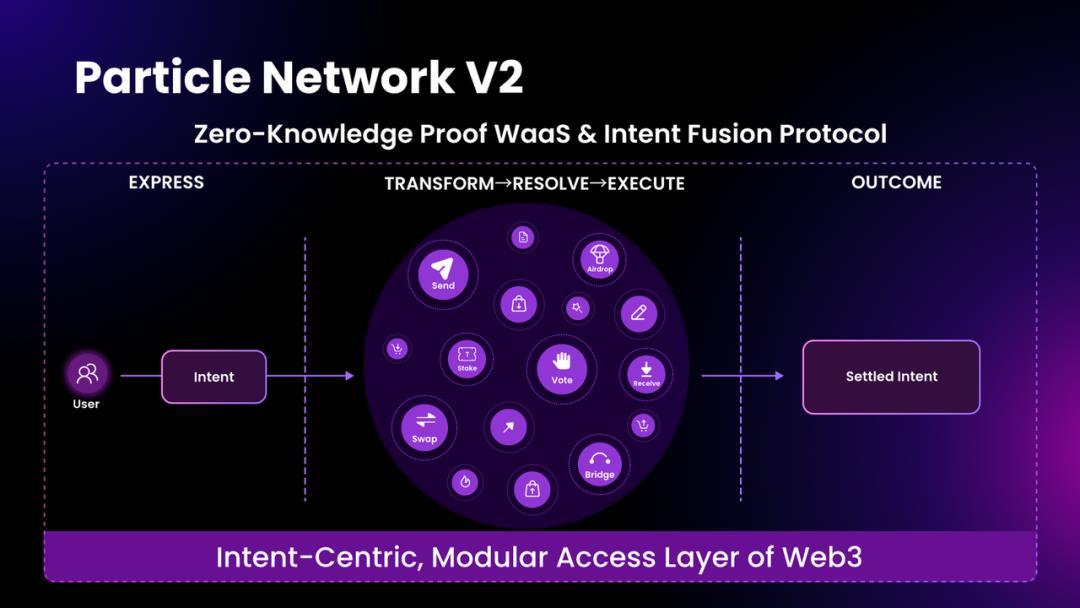
Particle Network collectively refers to this architecture as an “intent-centric, modular Web3 access layer.”
To better understand this concept, let’s break down its key characteristics:
-
Supports All Access Scenarios: Current Web3 user access scenarios include wallets, decentralized applications, and AI tools like GPT. V2 supports all these use cases.
-
No Compromise on Privacy Autonomy: Ensures full privacy and security across all scenarios, including protection of the link between accounts and addresses, and transaction history tied to addresses.
-
Minimal User Actions: Achieves any genuine user intent through the simplest and most efficient means, replacing today’s multi-step signing, layered authorizations, and manual planning of complex workflows.
-
Cross-Chain Compatibility: Fully supports both EVM and non-EVM chains.
-
Modular Design: Enhances decoupling and interoperability, significantly improving composability between dApps, protocols, and Particle Network itself.
If these technical concepts still feel abstract, consider the following example illustrating the user experience of an app integrated with Particle Network V2:

-
A user logs into a yield aggregator dApp on Ethereum using their Google account and automatically creates a wallet address—no private key or seed phrase involved;
-
No one else can detect the connection between their Google account and wallet address;
-
The user wants to invest their ETH into the best-yielding products across any L1/L2, automatically redeem once returns hit a threshold, then stake the proceeds in Lido for risk-free yield;
-
They simply type this requirement—the dApp automatically understands, breaks down, and executes the intent;
-
All transactions generated during deposit, redemption, and staking remain invisible to the outside world.
This scenario demonstrates a level of privacy and efficiency far surpassing current mainstream Web3 experiences—enabled precisely by zkWaaS (zero-knowledge WaaS) and the Intent Fusion Protocol in V2.
Yet this example remains simplified. How exactly are zkWaaS and the Intent Fusion Protocol designed and implemented?
Confidential Auth: Pioneering Seamless Hiding of Web2 Account-to-Address Mappings
Recent incidents involving SocialFi app Friend.Tech offer useful insights into hiding the link between Web2 social accounts and on-chain addresses.
It was recently revealed that Twitter IDs and corresponding Friend.tech wallet addresses were leaked due to publicly exposed query APIs, allowing anyone to retrieve associations between Twitter handles and wallet addresses.
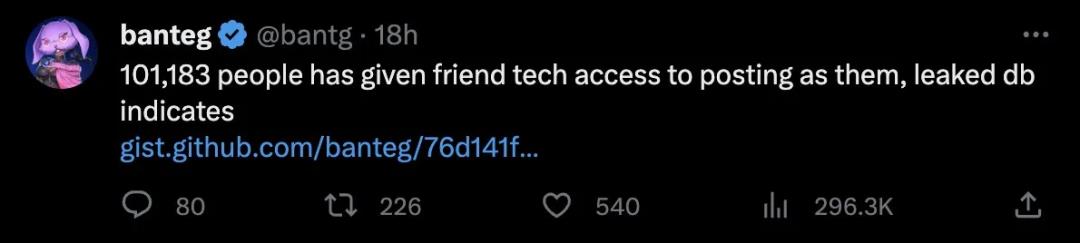
While some high-profile individuals may not mind exposing their off-chain identities, many others do care.
More critically, due to flawed product designs, such exposure can happen without user consent.
Hence, the Web3 industry needs a method to conceal the link between wallet addresses and Web2 accounts—without sacrificing the convenience of Web2 logins.
Common industry solutions involve generating a Web3 version of Web2 login credentials and verifying them via zero-knowledge proofs. Examples include Holonym, Polygon ID, and Chainlink’s CanDID.
However, these approaches require users to actively manage their Web3 credentials, imposing cognitive and operational burdens.
Therefore, Particle Network’s zkWaaS introduces Confidential Login—a novel approach enabling users to hide the link between their address and Web2 account effortlessly, without compromising login experience.
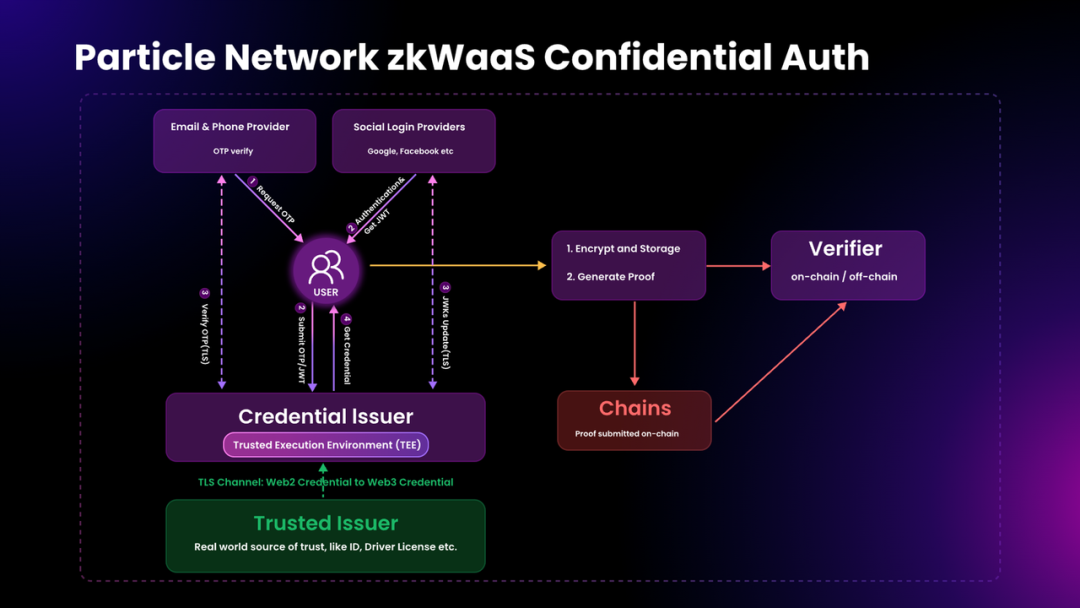
This “zero burden” means users remain unaware of backend complexity. Implementation steps:
1. Users log in via familiar email/phone verification or existing social accounts. Upon verification, a corresponding wallet is created;
2. Verification codes (for phone/email) or tokens (for social login) are submitted by zkWaaS to a credential issuer inside a Trusted Execution Environment (TEE);
3. The credential issuer verifies authenticity of the submitted code/token;
4. If valid, a Web3 token/certificate is issued, proving successful identity verification via Web2 method;
5. zkWaaS encrypts and stores this Web3 token/certificate by default;
6. This establishes a link between the wallet and Web2 login method, but since the Web3 token is encrypted, the relationship remains undetectable externally;
7. Only during verification is the token retrieved via zero-knowledge proof—otherwise, the link stays hidden due to encryption.
Beyond step one, the entire process is seamless—requiring no additional user effort or awareness.
Confidential Transaction: Ending the Era of Fully Exposed On-Chain Records
While Confidential Login hides the link between addresses and off-chain Web2 accounts, on-chain privacy remains unresolved: public blockchains inherently expose all transactions to view, query, and trace.
Transparency can be a double-edged sword.
Public transparency enables on-chain analytics, helping track whale movements for investment decisions. But for consumer or non-financial use cases, having every transaction exposed amounts to “running naked”—raising serious privacy and emotional concerns.
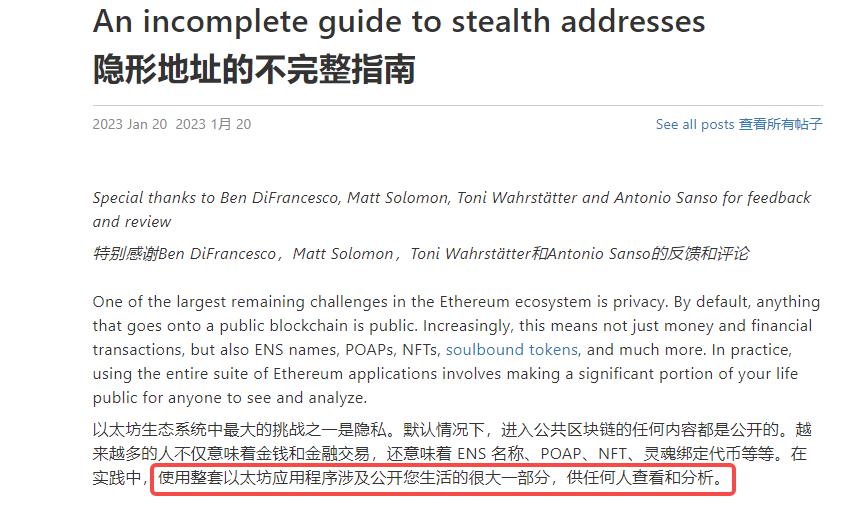
Vitalik expressed similar concerns in his January research piece, “An incomplete guide to stealth addresses,” noting that using Ethereum apps might inadvertently expose much of one’s personal life.
Current solutions for such privacy issues fall into two categories: asset-level privacy and address-level privacy.
Asset-level privacy, exemplified by mixers like Tornado Cash, obfuscates fund flows by mixing users’ funds together, making tracking difficult.
However, such tools are vulnerable to misuse by bad actors for money laundering, often provoking regulatory backlash—as seen in the U.S. Treasury sanctioning Tornado Cash.
Address-level privacy traditionally involves users maintaining multiple addresses to isolate transactions—an approach that increases management overhead and fails to fully prevent address linkage detection.
Another method, explored in Vitalik’s earlier work, is establishing a Stealth Address system: generating one-time temporary addresses for transactions.
However, these temporary addresses start with zero balance, making it impossible to pay gas fees—leading to a chicken-and-egg problem.
To overcome this, Particle Network’s zkWaaS advances beyond Vitalik’s Stealth Address concept by introducing Smart Stealth Address, supporting Confidential Transactions: leveraging stealth addresses combined with a gas station mechanism to resolve initial gas funding, ensuring external observers cannot determine which specific address received assets.
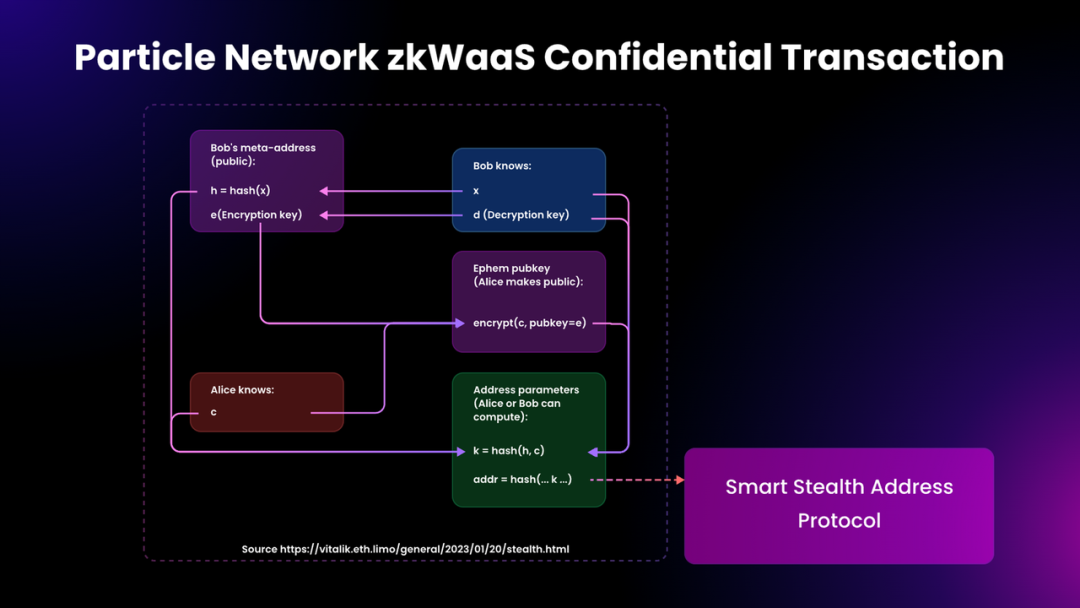
Implementation flow:
1. When Alice wants to send assets to Bob, Bob does not want everyone to know he received them. The recipient’s identity can be hidden, though the fact of transfer cannot.
2. Confidential transactions enable this. Bob generates a stealth address from his public-private key pair and shares it with Alice. She sends assets to this address, verifiably linked to Bob, yet only Bob controls them.
3. Via a Gas Station, another account can sponsor gas fees for the stealth address’s transaction, enabling execution.
From a design and integration standpoint, address-level privacy is superior: it requires no additional work, new contracts, or consensus changes—only wallet-layer support for stealth addresses is needed.
With Particle Network V2, dApps gain built-in on-chain privacy protection without custom adaptation—boosting efficiency while drastically reducing costs.
Intent Fusion Protocol: Focusing Interaction on Outcomes, Not Processes
In July, Paradigm outlined its top 10 focus areas, with “intent-centric” protocols and infrastructure ranked first.
Since then, the concept of “intent” has gradually entered mainstream discourse.
Yet behind this new term lies an old problem: low interaction efficiency in Web3. Instead of executing a sequence of commands, users should be able to declare their desired outcome directly.
Put simply, Web3 interaction should embody “what you think is what you get”.
Most current Web3 apps center around processes—achieving a final goal requires navigating multiple steps, repeated authorizations, and signatures.
More importantly, users must themselves decompose these processes and plan the path to their goal. For instance, buying an NFT on a new L2 may require downloading a wallet, switching chains, bridging assets, depositing gas, and authorizing transactions—an arduous, knowledge-intensive journey.
Thus, we need a way to automatically understand, decompose, and execute any final user intent—abstracting away the complexity of interaction.
Some DeFi protocols have led this charge—for example, limit orders in DEXs represent a classic “what you think is what you get” design. When price conditions are met, tokens swap at preferred rates, achieving the user’s ultimate goal.
But such innovations remain confined to financial use cases and lack generality. A universal intent-processing framework is needed across diverse application domains.
This is precisely the direction explored in Particle Network V2: through the Intent Fusion Protocol, integrating possible intent patterns across applications to automatically structure, decompose, and execute user intents.
Notably, this integration of intent patterns is permissionless and universally applicable.
Any on-chain or off-chain intent can be handled by the Intent Fusion Protocol without restrictive permissions or context limitations. Whether in DeFi, gaming, or social, it forms a unified intent processing framework.
Breaking down this intent-processing framework reveals three core stages:
1. User Expresses Intent: Users communicate their goals through supported interfaces—such as dApps or wallets powered by zkWaaS. To facilitate recognition, Particle Network provides tools for both users and developers.
-
Intent DSL (Domain-Specific Language): A structured format designed to make expressing intents intuitive.
-
DApp Intent Framework: A developer toolkit enabling easy interpretation and structuring of user intents.
2. Intent Decomposition: Structured user intents are sent to the “Intent Bidder Network,” combining on- and off-chain bidders to optimally break down the intent into a Confidential Intent Object—a detailed, encrypted instruction set guiding system execution.
3. Intent Execution: The user signs the encrypted object. The Intent Solver Network ensures correct and efficient execution. Solvers—on or off-chain—compete to fulfill the intent and earn rewards. Greater competition drives higher efficiency. Finally, the intended result is delivered.
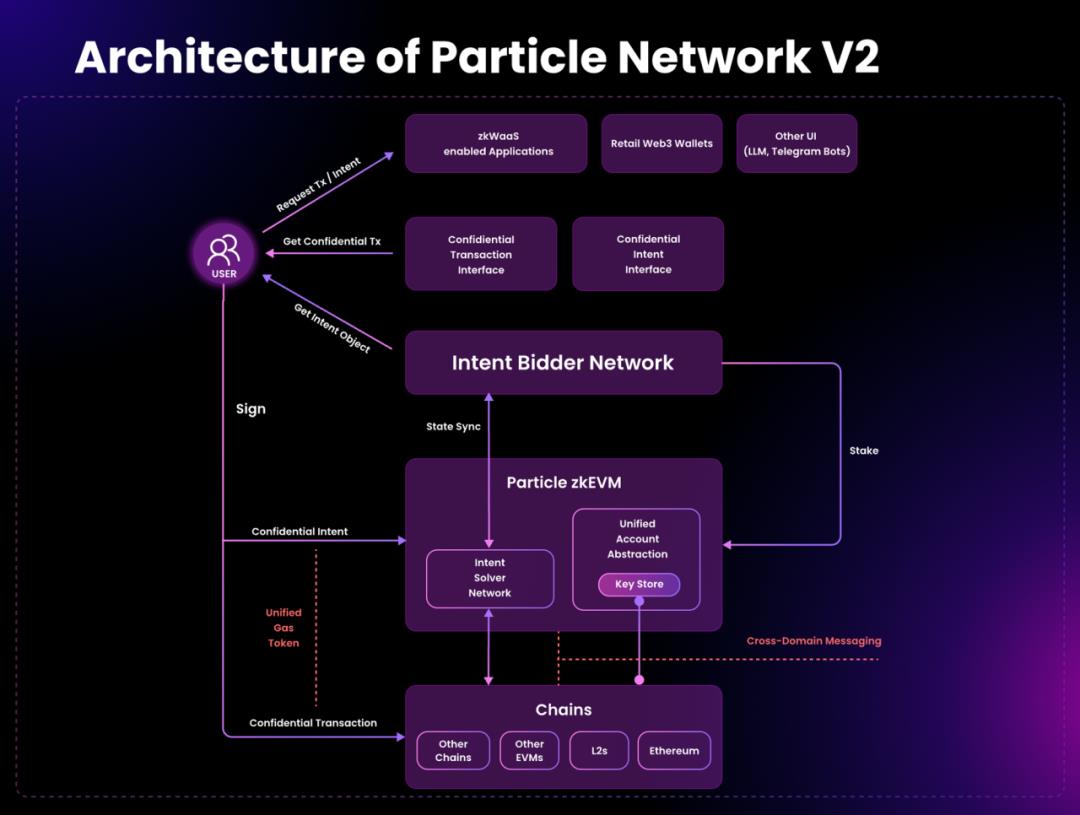
However, the Intent Fusion Protocol alone isn’t sufficient—the execution environment must also provide supporting infrastructure:
-
Particle zkEVM: A core component providing multi-chain account abstraction. This allows a single signature to execute actions across multiple chains. Additionally, zkEVM hosts a unified Intent Mempool, which uses IntentVM to pass structured Confidential Intent Objects to solvers for transaction construction and execution.
-
Intent Mempool: Transmits structured “Confidential Intent Objects” to solvers via IntentVM, enabling transaction building and execution.
-
Staking Manager and Intent Registry: These form the foundation for security and on/off-chain consensus, governing reward mechanisms to ensure smooth system operation and collaboration.
Overall, Particle Network V2 delivers a comprehensive intent protocol plus execution environment. Users only need to express their intention—the rest (structuring, decomposition, execution) is automated.
Ultimately, users can interact like chatting with ChatGPT—typing a request (e.g., “buy an NFT on Base”), and the app directly produces the desired outcome, abstracting away all underlying complexity.
The Web3 Access Layer: A New Engine Steering Toward Blue Ocean Opportunities
Returning to the opening question: how can we improve the Web3 user experience?
While users naturally become more proficient through repeated interactions, we cannot expect every individual to be a technically savvy expert or hyper-vigilant about privacy.
Web3 access and interaction should serve ordinary people. Embracing this philosophy is key to unlocking the next wave of user growth.
Finally, let’s summarize how Particle Network V2—the pioneering modular access layer—adapts to diverse users and scenarios:
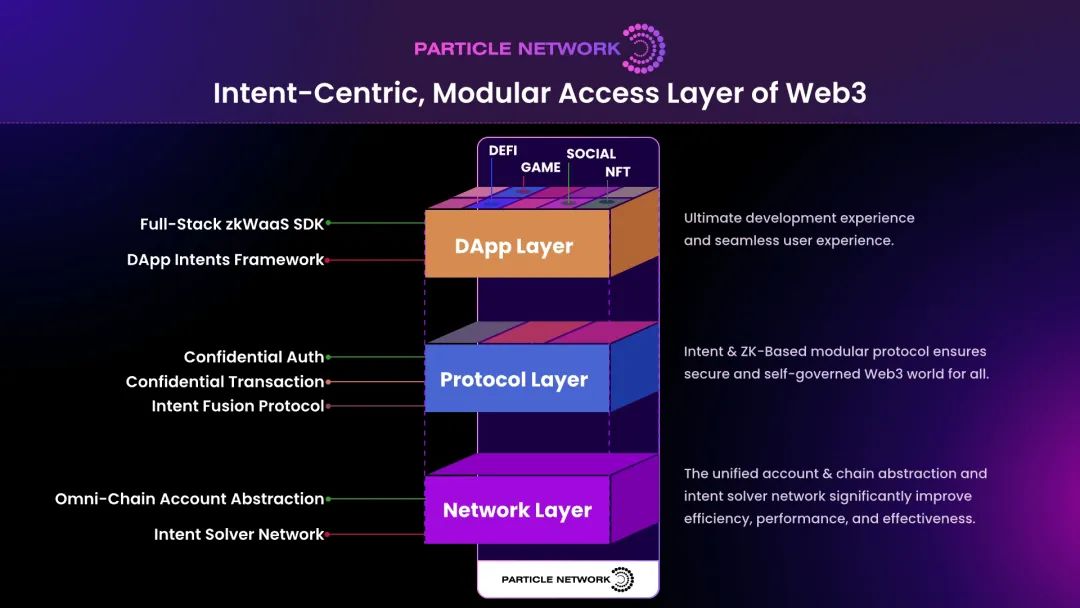
-
Base Layer (Network): Particle Network provides account abstraction and intent resolution networks, laying the groundwork for efficient transactions and interactions;
-
Middle Layer (Protocols): Includes privacy authentication, confidential transactions, and intent fusion protocols, designed modularly so projects can integrate partial or full components;
-
Top Layer (Applications): Various dApps leverage protocol integration and infrastructure capabilities via SDKs and frameworks to directly utilize WaaS, zk, and intent functionalities—delivering极致 user access and interaction experiences.
With this architecture, the access layer functions like an engine—driving alignment across different layers of applications and protocols, transforming Web3 from an engineer-friendly financial niche into a user-friendly consumer industry.
Eventually, when the entire industry is fully prepared to onboard new users, Web3 will unlock unprecedented possibilities.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News