
BlockSec × Bitget Year-End Joint Report | AI × Trading × Security: The Evolution of Risks in the Era of Intelligent Trading
TechFlow Selected TechFlow Selected

BlockSec × Bitget Year-End Joint Report | AI × Trading × Security: The Evolution of Risks in the Era of Intelligent Trading
This article will systematically examine the key changes occurring at the intersection of AI, trading, and security—and the industry’s response strategies—across three core dimensions: the emergence of new use cases, the amplification of new challenges, and the rise of new opportunities.
Preface
Over the past year, AI’s role in the Web3 world has undergone a fundamental transformation: it is no longer merely an auxiliary tool that helps humans understand information faster or generate analytical conclusions—it has become a core driver for enhancing trading efficiency and optimizing decision quality, deeply embedding itself into the entire practical chain of trade initiation, execution, and fund flow. As large language models (LLMs), AI Agents, and automated execution systems mature, trading paradigms are evolving from the traditional “human-initiated, machine-assisted” model toward a new paradigm of “machine-planned, machine-executed, human-supervised.”
At the same time, Web3’s three defining characteristics—public data, protocol composability, and irreversible settlement—give this automation trend a distinctly dual-edged nature: while offering unprecedented potential for efficiency gains, it also brings a steeply rising risk curve.

This transformation is concurrently shaping three entirely new real-world scenarios:
First, a disruptive shift in trading scenarios: AI is now independently assuming critical decision-making functions—including signal identification, strategy generation, and execution path selection—and can even directly complete inter-machine payments and invocations via innovative mechanisms like x402, accelerating the formation of a “machine-executable trading system”;
Second, an escalation in risk and attack patterns: once the entire trading and execution process becomes automated, vulnerability analysis, attack-path generation, and illicit fund laundering also become automated and scalable. For the first time, the speed at which risks propagate has consistently outpaced the limits of human intervention—that is, risks now spread faster than humans can react or intervene;
Third, emerging opportunities in security, risk control, and compliance: only by engineering, automating, and interface-izing security, risk control, and compliance capabilities can intelligent trading systems maintain controllability alongside efficiency gains—thus enabling sustainable development.
It is against this industry backdrop that BlockSec and Bitget jointly authored this report. Rather than debating the foundational question of “whether AI should be used,” we focus on a more pragmatic core issue: as trading, execution, and payment all move decisively toward machine executability, how is Web3’s risk architecture undergoing deep structural evolution—and how should the industry reconstruct its foundational security, risk control, and compliance capabilities to respond? This paper systematically outlines key developments and industry response directions at the intersection of AI × Trading × Security, organized around three core dimensions: the emergence of new scenarios, the amplification of new challenges, and the rise of new opportunities.
Chapter I: AI’s Capability Evolution and Integration Logic with Web3
AI is transitioning from a mere assistive judgment tool to an Agent system possessing planning capability, tool-calling ability, and closed-loop execution capability. Meanwhile, Web3 inherently features three core attributes—public data, composable protocols, and irreversible settlement—making automation highly rewarding, yet simultaneously magnifying the cost of operational errors and malicious attacks. This intrinsic characteristic dictates that when discussing offense-defense dynamics and compliance in Web3, we are not simply applying AI tools to existing workflows; rather, we are experiencing a comprehensive, system-wide paradigm shift—trading, risk control, and security are all simultaneously moving toward machine executability.
1. AI’s Capability Leap in Financial Trading and Risk Control: From “Assistive Tool” to “Autonomous Decision System”
If we view AI’s evolving role in financial trading and risk control as a clear evolutionary chain, the most critical inflection point lies in whether the system possesses closed-loop execution capability.
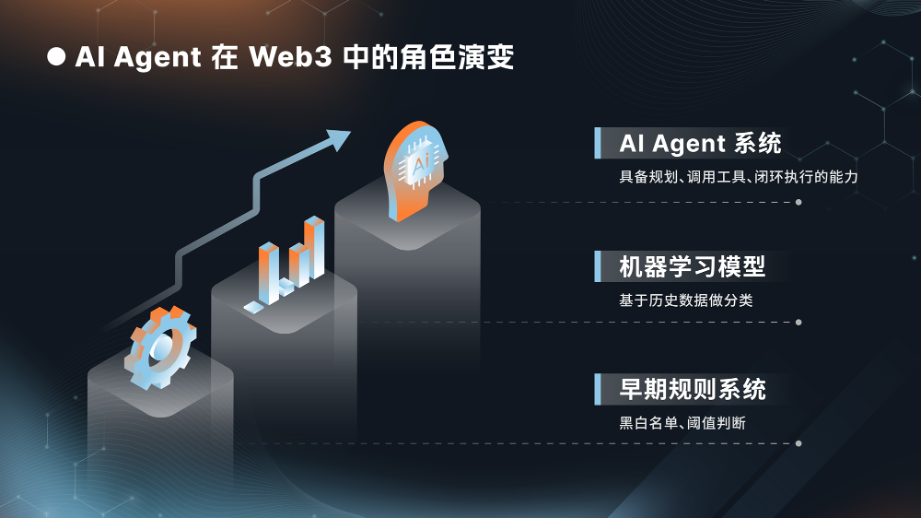
Early rule-based systems resembled “automated tools with brakes”: their core function was translating expert knowledge into explicit threshold judgments, black-and-white list management, and fixed risk-control policies. This approach offered advantages in logical interpretability and low governance costs—but its drawbacks were equally pronounced: extremely slow responses to novel business models and adversarial attack behaviors. As business complexity increased, rules piled up endlessly, eventually forming an unmaintainable “strategy debt” mountain—severely constraining system flexibility and responsiveness.
Subsequently, machine learning advanced risk control into a statistical pattern-recognition phase: through feature engineering and supervised learning algorithms, risk scoring and behavioral classification significantly improved coverage in risk identification. However, this approach heavily relies on historically labeled data and data-distribution stability, suffering from the classic “distribution shift problem”—i.e., patterns learned during model training become invalid in real-world applications due to market environment changes, upgraded attack methods, etc., causing sharp drops in model accuracy (essentially rendering historical experience obsolete). Once attackers alter attack paths, migrate cross-chain, or fragment funds more granularly, the model exhibits obvious judgment bias.
The emergence of large language models (LLMs) and AI Agents has brought revolutionary change to this domain. The core advantage of AI Agents lies not only in being “smarter”—possessing stronger cognition and reasoning—but more importantly, in being “more capable”—exhibiting full workflow orchestration and execution ability. It elevates risk mitigation from traditional single-point prediction to end-to-end closed-loop management, including identifying anomalous signals, supplementing associated evidence, linking related addresses, interpreting contract behavior logic, assessing risk exposure, generating targeted mitigation recommendations, triggering control actions, and producing auditable records—all in one seamless sequence. In other words, AI has evolved from “telling you something may be wrong” to “helping you bring the issue to an actionable state.”
This evolution is equally significant on the trading side: from traditional manual research report reading, indicator monitoring, and strategy writing, to AI automatically scraping multi-source data, auto-generating trading strategies, auto-executing orders, and auto-reviewing/optimizing performance—the system’s action chain increasingly resembles an “autonomous decision system.”
Yet caution is warranted: once entering the autonomous decision-system paradigm, risks escalate in tandem. Human operational errors tend to be low-frequency and inconsistent; machine errors, however, often manifest as high-frequency, replicable events—potentially triggered at scale, simultaneously. Hence, AI’s true challenge in financial systems isn’t “can it be done?” but “can it be done within controllable boundaries?” These boundaries include clearly defined permission scopes, fund-amount limits, callable-contract ranges, and automatic fallback or emergency braking upon risk detection. This issue is further amplified in Web3, primarily due to on-chain transaction irreversibility—once an error or attack occurs, fund losses are often unrecoverable.
2. Web3’s Technical Architecture and Its Amplification Effect on AI Applications: Public, Composable, Irreversible
As AI evolves from “assistive tool” to “autonomous decision system,” a key question arises: what chemical reaction does this evolution produce when combined with Web3? The answer is: Web3’s technical architecture simultaneously amplifies AI’s efficiency advantages and risk vulnerabilities—enabling exponential efficiency gains in automated trading, while significantly expanding the scope and severity of potential risks. This amplification effect stems from the convergence of Web3’s three structural features: public data, protocol composability, and irreversible settlement.
From an advantage perspective, Web3’s core appeal to AI lies first in the data layer. On-chain data is inherently transparent, verifiable, and traceable—providing transparency advantages for risk control and compliance unmatched in traditional finance. You can clearly observe fund movement trajectories, cross-protocol interaction paths, and fund splitting/convergence processes on a unified ledger.
However, on-chain data also presents significant interpretive difficulty: addresses suffer from “semantic sparsity” (i.e., on-chain addresses lack explicit identity identifiers, making direct association with real-world entities difficult); noise data volume is massive; and cross-chain data fragmentation is severe. When genuine business behavior intertwines with obfuscation tactics, simple rules struggle to effectively distinguish them. This makes understanding on-chain data itself a high-cost engineering task—requiring deep integration of transaction sequences, contract invocation logic, cross-chain message passing, and off-chain intelligence to yield explainable, trustworthy conclusions.
Even more critical is the impact of Web3’s composability and irreversibility. Protocol composability dramatically accelerates financial innovation—a trading strategy can be flexibly assembled like LEGO blocks, combining lending, decentralized exchanges (DEXs), derivatives, cross-chain bridges, and other modules to create innovative financial products and services. Yet this characteristic also accelerates risk propagation: a minor flaw in one component can rapidly amplify along the “supply chain,” even being swiftly repurposed by attackers as an attack template (we use “supply chain” instead of “dependency chain” here to make risk transmission relationships more intuitive to general audiences).
Irreversibility, meanwhile, drastically increases post-incident handling difficulty. In traditional finance, erroneous transactions or fraud may still be recoverable via transaction reversal, payment refusal, or inter-institutional compensation mechanisms. In Web3, however, once funds cross chains, enter mixing services, or rapidly disperse across numerous addresses, fund recovery difficulty rises geometrically. This forces the industry to shift security and risk-control focus from traditional “post-hoc explanation” to “pre-incident warning and real-time blocking”—only interventions before or during risk occurrence can effectively mitigate losses.
3. Divergent Integration Paths for CEXs and DeFi: Same AI, Different Control Surfaces
Having understood Web3’s amplification effect, we must confront a practical reality: although both centralized exchanges (CEXs) and decentralized finance (DeFi) protocols adopt AI, their application focal points differ fundamentally—due to inherent differences in their “control surfaces” (a network engineering term here referring specifically to intervention capability over funds and protocols).
When applying AI to trading and risk control, CEXs and DeFi naturally emphasize different aspects. CEXs possess complete account systems and strong control surfaces, enabling KYC (Know Your Customer)/KYB (Know Your Business), transaction limit setting, and proceduralized freeze/rollback mechanisms. Thus, AI’s value in CEX contexts often manifests as more efficient review processes, timelier suspicious-transaction identification, and more automated compliance documentation generation and audit-log retention.
In contrast, DeFi protocols—by virtue of decentralization—have relatively limited intervention capabilities (i.e., weaker control surfaces) and cannot directly freeze user accounts like CEXs. Instead, they resemble an “open environment with weak control surface + strong composability.” Most DeFi protocols lack fund-freezing capability; actual risk-control points are dispersed across frontend interfaces, API layers, wallet authorization steps, and compliance intermediaries (e.g., risk-control APIs, risk-address blacklists, on-chain monitoring/alert networks), among others.
This means AI applications in DeFi prioritize real-time understanding and alerting capabilities—including early detection of anomalous transaction paths, early identification of downstream risk exposure, and rapid dissemination of risk signals to nodes with actual control authority (e.g., trading platforms, stablecoin issuers, law-enforcement partners, or protocol governance bodies)—akin to Tokenlon’s KYA (Know Your Address) scanning of transaction-initiating addresses, outright rejecting service to known blacklist addresses to intercept and block funds before they enter uncontrollable zones.
From an engineering implementation perspective, this control-surface difference determines AI capability’s concrete form: in CEX contexts, AI functions more like a high-throughput decision-support and automated operations system, focusing on enhancing existing process efficiency and accuracy; in DeFi contexts, AI operates more like a continuously running on-chain situational awareness and intelligence distribution system, emphasizing early risk detection and rapid response. Though both converge toward Agent-ification, their constraint mechanisms differ markedly: CEX constraints stem primarily from internal rules and account-permission management, whereas DeFi constraints rely more heavily on programmable authorization, transaction simulation validation, and whitelisted management of callable-contract ranges.
4. AI Agents, x402, and the Emergence of Machine-Executable Trading Systems: From Bot to Agent Network
Past trading bots were simple combinations of fixed strategies and fixed interfaces, with relatively monolithic automation logic; AI Agents, by contrast, resemble generalized executors—they autonomously select tools, compose execution steps, and self-correct/optimize based on feedback according to specific goals. Yet for AI Agents to truly possess full economic agency, two core conditions are indispensable: first, explicit programmable authorization and risk-control boundaries; second, machine-native payment and settlement interfaces. The emergence of the x402 protocol satisfies the second condition: by embedding into standard HTTP semantics, it decouples the payment step from human interaction flows, enabling clients (AI Agents) and servers to conduct efficient inter-machine transactions without accounts, subscriptions, or API keys.
Once payment and invocation processes become standardized, machine economies will adopt entirely new organizational forms: AI Agents will no longer be confined to single-point task execution but will form continuous closed loops across multiple services—“pay-for-invocation → retrieve data → generate decisions → execute trades.” Yet this standardization also renders risks standardized: payment standardization breeds automated fraud and money-laundering service invocation; strategy-generation standardization leads to replicable attack-path proliferation.
Thus, the core logic emphasized here is: AI’s integration with Web3 is not merely about connecting AI models to on-chain data—it is a profound system-wide paradigm shift. Specifically, both trading and risk control are simultaneously moving toward machine-executability; and in a machine-executable world, we must establish complete infrastructure enabling machines to act, be constrained, be audited, and be blocked—otherwise, efficiency gains will be fully offset by losses from risk spillover.
Chapter II: How AI Reshapes Web3 Trading Efficiency and Decision Logic
1. Core Challenges in Web3 Trading Environments and AI’s Entry Points
One core structural challenge in Web3 trading environments is liquidity fragmentation caused by coexisting centralized exchanges (CEXs) and decentralized exchanges (DEXs)—liquidity is scattered across different trading venues and blockchain networks, causing frequent discrepancies between “visible prices” and “actually executable prices/sizes.” Here, AI plays a critical role as a dispatch layer, leveraging multidimensional factors—including market depth, slippage cost, transaction fees, routing paths, and latency—to provide users optimal trade-order distribution and execution-path recommendations, effectively improving execution efficiency.
High volatility, high risk, and information asymmetry have long plagued crypto markets—and intensify further during event-driven price movements. One core value of AI in mitigating this issue is expanding information coverage: structuring and analyzing project announcements, on-chain fund data, social-media sentiment, and professional research materials to help users rapidly build foundational understanding of project fundamentals and potential risk points—thereby reducing decision bias stemming from information asymmetry.
Using AI to assist trading is not new—but AI’s role is evolving from “assisting information reading” to the core stages of “signal identification → sentiment analysis → strategy generation.” Examples include real-time identification of anomalous fund flows and whale-address fund migrations; quantitative analysis of social-media sentiment and project-narrative热度; and automatic classification/tips for market states (trending/market-range/volatility-expansion regimes). In the high-frequency information-interaction environment of Web3 markets, these capabilities readily achieve scalable application value.
However, AI application boundaries must be emphasized simultaneously: current crypto-market price efficiency and information quality remain unstable. If upstream AI-input data contains noise interference, human manipulation, or erroneous attribution, classic “garbage in, garbage out” problems arise. Therefore, when evaluating AI-generated trading signals, source credibility, logical evidence-chain completeness, explicit confidence-expression, and counterfactual verification mechanisms (i.e., whether signals withstand multidimensional cross-validation) are more critical than “signal strength” itself.
2. Industry Forms and Evolutionary Directions of Web3 Trading AI Tools
Currently, exchange-integrated AI tools are evolving from traditional “market commentary” toward “full-trading-process assistance,” placing greater emphasis on unified information views and information-distribution efficiency. Take Bitget’s GetAgent as an example: its positioning leans more toward a general-purpose trading-information and investment-advisory assistance tool—presenting key market variables, potential risk points, and core information highlights in ways requiring lower comprehension thresholds, effectively alleviating user barriers in information acquisition and professional understanding.
On-chain bots and copy trading represent the diffusion trend of execution-side automation. Their core advantage lies in transforming professional trading strategies into replicable, standardized execution processes—lowering trading barriers for ordinary users. In the future, a key copy-trade target may originate from AI-powered quantitative trading teams or systematic strategy providers—yet this transforms the “strategy quality” issue into a more complex “strategy sustainability and explainability” problem: users need not only know past strategy performance but also understand underlying logic, applicable scenarios, and potential risks.
Market capacity and strategy congestion deserve special attention: when large amounts of capital simultaneously act on similar signals and execution logic, trading returns compress rapidly, and market-impact costs and fund drawdowns significantly amplify. Especially in on-chain trading environments, slippage fluctuations, MEV (Maximal Extractable Value) effects, routing-path uncertainty, and instantaneous liquidity changes further exacerbate the negative externalities of “congested trading,” causing actual returns to fall far short of expectations.
Therefore, a more neutral and rational conclusion is: the more automated AI trading tools become, the more essential it is to discuss capability descriptions alongside constraint mechanisms. These constraints include clearly defined strategy applicability conditions, strict risk upper limits, automatic shutdown rules under abnormal market conditions, and auditable capabilities for data sources and signal-generation processes—otherwise, “efficiency enhancement” itself may become a channel for risk amplification, causing unnecessary losses to users.
3. Bitget GetAgent’s Positioning Within the AI Trading Ecosystem
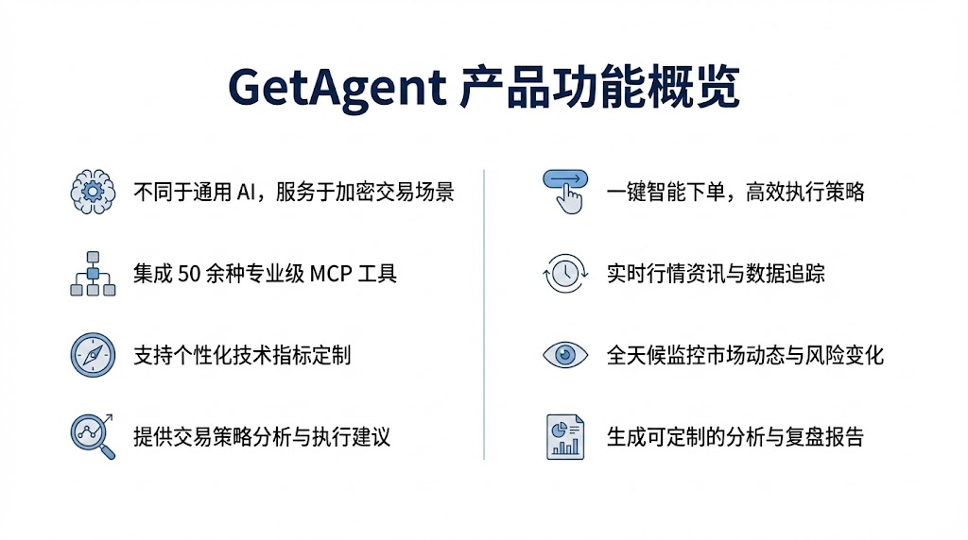
GetAgent’s positioning extends beyond that of a simple chatbot—it serves as traders’ “second brain” amid complex liquidity environments. Its core logic lies in constructing a complete closed loop connecting data, strategy, and execution through deep integration of AI algorithms and real-time multidimensional data. Its core value manifests across four key dimensions:
(1) Real-Time News and Data Tracking
Traditional news monitoring and data analysis require users to possess advanced web-scraping and retrieval-analysis skills—creating high entry barriers. GetAgent integrates over 50 professional-grade tools to achieve real-time “black-box penetration” of markets—not only monitoring mainstream financial media in real time but also deeply penetrating social-media sentiment, core project updates, and other information dimensions—ensuring users face no blind spots in information acquisition.
Simultaneously, GetAgent boasts powerful information filtering and distillation capabilities, effectively eliminating noise such as meme-coin marketing, precisely extracting core variables genuinely impacting price volatility—e.g., project security vulnerability warnings, large-token unlock schedules, etc. Finally, GetAgent integrates fragmented on-chain transaction flows with massive announcements, research reports, etc., transforming them into intuitive logical judgments—for instance, directly informing users “though social-media hype is high for this project, core developers’ funds are continuously flowing out,” making latent risks immediately apparent.
(2) Trading Strategy Generation and Execution Assistance
GetAgent generates customized trading strategies based on users’ personalized needs, significantly lowering trading-execution barriers and shifting trading decisions from “professional instruction-driven” to precise “intent-strategy-driven.” Leveraging users’ historical trading preferences, risk tolerance, and current holdings, GetAgent delivers not broad bull/bear-market advice but highly targeted guidance—for example, “for your current BTC holdings, set a grid-trading strategy within the X-Y range under current volatility.”
For complex cross-asset, cross-protocol operations, GetAgent simplifies them into natural-language interactions—users express trading intent in everyday language, and GetAgent automatically matches optimal strategy solutions in the background while optimizing market depth and slippage—greatly lowering the barrier for ordinary users to participate in complex Web3 trading.

(3) Synergistic Relationship with Automated Trading Systems
GetAgent is not an isolated tool but the core decision node within the broader automated trading ecosystem. Upstream, it receives multidimensional inputs—from on-chain data, real-time market行情, social-media sentiment, and professional research information; after structured processing, key-information summarization, and associative-logic analysis, it forms a systematic strategy-judgment framework; downstream, it provides precise decision references and parameter suggestions to automated trading systems, quantitative AI Agents, and copy-trading systems—achieving holistic ecosystem synergy.
(4) Risks and Constraint Conditions Behind Enhanced Trading Efficiency
While embracing AI-driven efficiency gains, maintaining heightened vigilance against latent risks remains essential. Regardless of how robust GetAgent’s trading signals appear, the core principle of “AI recommendation, human confirmation” must be consistently upheld. During ongoing R&D and continuous AI-capability enhancement, Bitget’s team not only strives to enable GetAgent to deliver precise trading recommendations but also persistently explores feasibility for GetAgent to provide complete logical evidence chains—e.g., why recommend this buy point? Is it due to technical-indicator resonance, or anomalous whale-address fund inflows?
In Bitget’s view, GetAgent’s long-term value lies not in delivering deterministic trading conclusions, but in helping traders and trading systems more clearly understand the types of risks they are bearing—and whether those risks align with current market phases—thus enabling more rational trading decisions.
4. Balancing Trading Efficiency and Risk: BlockSec’s Security Protection Support
Behind AI-driven trading-efficiency enhancements, risk control remains an indispensable core concern. Leveraging deep understanding of Web3 trading risks, BlockSec provides comprehensive security protection support—helping users enjoy AI trading convenience while effectively managing latent risks:
To address data-noise and erroneous-attribution risks, BlockSec’s Phalcon Explorer offers powerful transaction simulation and multi-source cross-verification capabilities, effectively filtering manipulative data and erroneous signals to help users identify genuine market trends;
For market risks arising from strategy congestion, MetaSleuth’s fund-flow tracking functionality enables real-time identification of fund concentration among similar strategies, providing early warnings of liquidity stampede risks to guide users’ trading-strategy adjustments;
Regarding execution-chain security, MetaSuites’ Approval Diagnosis functionality enables real-time detection of anomalous authorization behavior, supporting one-click revocation of high-risk authorizations to effectively prevent fund loss from privilege abuse or erroneous execution.
Chapter III: Web3 Offense-Defense Evolution and New Security Paradigms in the AI Era
While AI accelerates trading efficiency, it also makes attacks faster, stealthier, and more destructive. Web3’s decentralized architecture causes responsibility to be naturally diffused; smart-contract composability imbues risks with systemic spillover characteristics; and LLM proliferation further lowers technical barriers to vulnerability understanding and attack-path generation—driving attacks comprehensively toward automation and scalability.
Correspondingly, security defense must evolve from traditional “better detection” to “executable real-time response closed loops,” and—in machine-executed trading contexts—engineer governance for authorization management, erroneous-execution prevention, and systemic cascade risks, building a Web3 security paradigm adapted to the AI era.
1. AI’s Reshaping of Web3 Attack Methods and Risk Profiles
Web3’s security dilemma has never been merely about “whether vulnerabilities exist,” but more fundamentally about its decentralized architecture naturally dispersing responsibility. For example, protocol code is developed and released by project teams; frontend interfaces may be maintained by different teams; transactions are initiated via wallets and routing protocols; funds flow among DEXs, lending protocols, cross-chain bridges, and aggregators; and finally, on/off-ramps occur via centralized platforms. When security incidents occur, each link can claim only partial control-surface ownership—making full accountability difficult. Attackers exploit this structural dispersion, weaving threads across multiple weak links to create situations where no single entity maintains global control—thus achieving their objectives.
AI’s introduction makes this structural weakness even more pronounced. Attack paths become easier for AI systems to search, generate, and reuse systematically; risk-diffusion speed stabilizes above human-coordination speed limits for the first time—rendering traditional human emergency-response mechanisms obsolete. At the smart-contract level, systemic risks from vulnerabilities are no exaggeration. DeFi’s composability allows even minor code defects to rapidly amplify along dependency chains, culminating in ecosystem-level security incidents—while irreversible settlement compresses emergency-response windows to minutes.
According to BlockSec’s DeFi security incident data dashboard, in 2024 alone, over $2 billion in crypto assets were stolen via hacker attacks and vulnerability exploits—with DeFi protocols remaining primary targets. These figures clearly indicate that despite increasing industry investment in security, incidents continue occurring frequently with high per-incident losses and severe destructiveness. When smart contracts become core financial infrastructure, vulnerabilities cease being mere engineering flaws—they morph into systemic financial risks exploitable by malicious actors.
AI’s reshaping of the attack surface also manifests in automating previously manual, experience-dependent attack steps:
The first category is automated vulnerability discovery and comprehension. LLMs possess powerful code-reading, semantic-summarization, and logical-reasoning capabilities—enabling rapid extraction of potential weak points from complex contract logic and precise generation of vulnerability-trigger conditions, transaction-execution sequences, and contract-invocation combinations—significantly lowering technical barriers to vulnerability exploitation.
The second category is automated attack-path generation. Recent industry research has begun adapting large language models (LLMs) into end-to-end exploit-code generators—by integrating LLMs with specialized toolchains, one can start from specified contract addresses and block heights, automatically collect target information, interpret contract-behavior logic, generate compilable/executable attack smart contracts, and test-validate them on historical blockchain states. This means usable attack methods no longer depend solely on manual debugging by elite security researchers but may be engineered into scalable attack pipelines.
Broader security research corroborates this trend: given CVE (Common Vulnerabilities and Exposures) descriptions, GPT-4 achieves very high rates of generating usable exploit code in its test sets—revealing rapidly declining thresholds from natural-language descriptions to actual attack code. When generating attack code becomes increasingly like a conveniently callable capability, scalable attacks become more realistic.
The amplification effect of scalable attacks typically appears in Web3 through two typical modes:
The first is paradigmatic attacks—attackers employ identical attack strategies to batch-scan, screen, probe, and launch attacks against numerous contracts across the network sharing similar architectures and identical vulnerability types (using “paradigmatic attacks” instead of “same-template multi-target” better conforms to industry-standard terminology);
The second is supply-chain-ized fund laundering and fraud—eliminating attackers’ need to build full infrastructure themselves. For instance, Chinese-guaranteed black markets on Telegram and similar platforms have formed mature criminal-service markets. Since 2021, two major illegal markets—Huiwang Guarantee and Xinbi Guarantee—have facilitated over $35 billion in stablecoin transactions covering money laundering, stolen-data trading, and even more serious criminal services. Additionally, Telegram black markets now feature specialized fraud-tool trading—including deepfake tools. Such platformized criminal-service provision means attackers can not only generate vulnerability-exploitation schemes and attack paths faster but also rapidly acquire money-laundering toolkits for proceeds—escalating individual technical attacks into full-blown black-market industrial-chain events.
2. AI-Driven Security Defense Systems
Facing AI-driven attack-form evolution, AI’s core defensive value lies in transforming traditionally human-experience-dependent security capabilities into replicable, scalable engineering systems. This defense system’s core capabilities manifest across three levels:
(1) Smart Contract Code Analysis and Automated Auditing
AI’s core advantage in smart-contract auditing lies in structuring and systematizing fragmented audit knowledge. Traditional static analysis and formal verification tools excel at handling deterministic rules but easily fall into false-negative/false-positive dilemmas when facing complex business logic, multi-contract invocation combinations, and implicit assumptions. LLMs, however, demonstrate clear advantages in semantic interpretation, pattern induction, and cross-file logical reasoning—making them ideal for pre-audit stages, enabling rapid contract understanding and preliminary risk flagging.
Nonetheless, AI does not aim to replace traditional audit tools but rather acts like a higher-efficiency automated audit pipeline connecting them. Specifically, AI models first perform semantic summarization, suspicious-risk-point localization, and potential-attack-surface hypothesis generation for contracts; then pass this information to static analysis/dynamic verification tools for precise validation; finally, AI compiles validation results, evidence chains, vulnerability-trigger conditions, and remediation suggestions into standardized, auditable output reports. This division of labor—“AI for understanding, tools for verification, humans for decision-making”—will likely constitute a stable engineering paradigm for future smart-contract auditing.
(2) Anomalous Transaction and On-Chain Behavioral Pattern Recognition
AI’s work focus in this domain is transforming publicly available but chaotic on-chain data into actionable security signals. The core challenge in the on-chain world isn’t data scarcity but noise overload: high-frequency bot trading, fund-splitting transfers, cross-chain hops, and complex contract routing behaviors intermingle—rendering traditional simple-threshold strategies fragile and ineffective at identifying anomalies.
AI technologies suit such complex scenarios better—through sequence modeling and graph-association analysis, they precisely identify precursory behaviors of typical attacks (e.g., anomalous authorization operations, anomalous contract-call density, indirect associations with known-risk entities), continuously calculating downstream risk exposure—allowing security teams to clearly grasp fund movement directions, potentially affected scopes, and remaining time windows for interception/disposal.
(3) Real-Time Monitoring and Automated Response
In practical engineering environments, deploying these defensive capabilities requires continuously operating security platforms—not one-off analytical tools. Take BlockSec’s Phalcon Security Platform as an example: its design goal isn’t post-incident attack-detail retrospection but centers on three core functions—real-time on-chain and mempool monitoring, anomalous-behavior identification, and automated response—maximizing risk interception within still-actionable time windows.
In multiple real-world Web3 attack scenarios, Phalcon Security successfully identified latent attack signals early via continuous perception of transaction behaviors, contract interaction logic, and sensitive operations—and supported users configuring automated disposal strategies (e.g., automatic contract pausing, suspicious-transfer interception), effectively blocking risk diffusion before attacks completed. The core value of such capabilities doesn’t lie in “discovering more issues” but in enabling security defense—perhaps for the first time—to match automated-attack response speeds, propelling Web3 security from traditional passive-audit models toward proactive, real-time defense systems.
3. Security Challenges and Responses in Intelligent Trading and Machine-Execution Scenarios
As trading shifts from “human click confirmation” to “machine automatic closed-loop execution,” the core security risk migrates from traditional contract vulnerabilities toward permission management and execution-chain security.
First, wallet security, private-key management, and authorization risks become significantly amplified. Because AI Agents require frequent invocation of various tools and contracts, they inevitably necessitate more frequent transaction signing and more complex authorization configurations. Once private keys leak, authorization scopes become overly broad, or authorized parties are maliciously replaced, fund losses expand within seconds. Traditional safety advice like “users should be more cautious” becomes completely ineffective in machine-automatic-execution eras—because systems are designed explicitly to reduce human intervention, making real-time monitoring of every automated operation nearly impossible for users.
Second, AI Agents and machine-payment protocols (e.g., x402) introduce more covert, subtle permission-abuse and erroneous-execution risks. Protocols like x402—enabling APIs, applications, and AI Agents to instantly pay using stablecoins via HTTP—enhance trading efficiency but also grant machines autonomous payment and invocation capabilities across more stages. This opens new attack vectors: malicious behaviors like induced payments, induced invocations, and induced authorizations can be packaged to resemble normal business flows—evading defense mechanisms.
Meanwhile, AI models themselves may execute seemingly compliant but actually erroneous operations under prompt-injection attacks, data poisoning, or adversarial examples. The core issue here isn’t x402 protocol quality but rather that smoother, more automated machine-trading chains demand stricter permission boundaries, fund-limit policies, revocable-authorization mechanisms, and comprehensive audit-replay capabilities—otherwise, systems amplify minor errors into large-scale, automated cascade losses.
Finally, automated trading may trigger systemic cascade risks. When large numbers of AI Agents use similar signal sources and strategy templates, markets may exhibit severe “resonance phenomena”—i.e., identical triggers cause massive simultaneous buying/selling, order cancellations, and cross-chain migrations—significantly amplifying market volatility and triggering large-scale liquidations and liquidity stampedes. Attackers may also exploit this homogeneity by publishing misleading signals, manipulating local liquidity, or targeting key routing protocols—triggering cascading failures across on-chain and off-chain environments.
In other words, machine trading upgrades traditional individual-operation risks into more destructive group-behavior risks. Such risks don’t necessarily stem from malicious attacks but may arise from highly consistent automated “rational decisions”—when all machines make identical decisions based on the same logic, systemic risk emerges.
Therefore, a more sustainable security paradigm for the intelligent-trading era isn’t generic exhortations like “real-time monitoring is essential,” but engineering the above three risk-mitigation solutions:
First, strictly capping loss ceilings from authorization失控 via layered authorization and automatic downgrading mechanisms—ensuring single-permission leaks don’t cause global losses;
Second, effectively intercepting erroneous executions and induced malicious operations via pre-execution simulation and rationale-chain auditing—ensuring every automated transaction possesses clear logical grounding;
Third, suppressing systemic cascade reactions via de-homogenized strategy guidance, circuit-breaker mechanism design, and cross-entity collaborative coordination—ensuring single-market fluctuations don’t escalate into industry-wide crises.
Only thus can security defense truly align with machine-execution speeds—“braking” earlier, more stably, and more executably at critical risk nodes—ensuring safe and stable operation of intelligent trading systems.
Chapter IV: AI Applications in Web3 Risk Control, Anti-Money Laundering (AML), and Risk Identification
Web3’s compliance challenges stem not merely from anonymity but from intertwined complexities: the paradox of coexisting anonymity and traceability, path-explosion problems arising from cross-chain and multi-protocol interactions, and enforcement fragmentation resulting from differing control surfaces between DeFi and CEXs. AI’s core opportunity here lies in compressing massive on-chain noise data into actionable risk facts—linking address profiling, fund-path tracking, and contract/Agent risk assessment into complete closed loops, and productizing these capabilities as real-time alerts, disposition orchestration, and auditable evidence chains.
Upon entering the AI Agent and machine-payment era, compliance domains face new protocol-adaptation and responsibility-assignment challenges—making RegTech (Regulatory Technology) interface-ization and automation inevitable industry trends.
1. Structural Challenges in Web3 Risk Control and Compliance
(1) The Tug-of-War Between Anonymity and Traceability
The first core contradiction in Web3 compliance lies in the simultaneous existence of anonymity and traceability. On-chain transaction records are inherently transparent and immutable—meaning every fund flow is theoretically traceable. Yet on-chain addresses don’t inherently equate to real-world identities; market participants can transform “traceable” into “traceable but unattributable” via frequent address rotation, fund-splitting transfers, intermediate-contract introductions, and cross-chain operations—i.e., though fund flows can be tracked, determining the true controller proves difficult.
Thus, Web3 risk control and AML work cannot rely primarily on account real-name registration and centralized clearing—as in traditional finance—to pin responsibility. Instead, risk-judgment systems must be built on behavioral patterns and fund paths: how to cluster-identify address groups belonging to the same entity; where funds originate and where they flow; what interactions occur within which protocols; and what the true intent behind these interactions is—these details constitute the core elements of risk facts.
(2) Compliance Complexity from Cross-Chain and Multi-Protocol Interactions
Today, Web3 fund flows rarely complete closed loops within single chains or protocols—instead, they often undergo sequential complex actions: “cross-chain bridging → DEX swaps → lending operations → derivatives trading → re-cross-chain.” Once fund paths elongate, compliance challenges escalate from identifying isolated suspicious transactions to discerning the true intent and ultimate consequences of entire cross-domain paths. More challengingly, each individual step in such paths may appear perfectly normal (e.g., routine token swaps, liquidity-provision operations), yet collectively they may serve fund-source obfuscation and illicit cash-out purposes—posing immense difficulties for compliance identification.
(3) Scenario Fragmentation: Regulatory Differences Between DeFi and CEX
The third core challenge arises from significant regulatory and enforcement-capability differences between DeFi and CEXs. CEXs possess natural strong control surfaces, complete account systems, strict on/off-ramp gateways, relatively centralized risk-control strategies and fund-freezing capabilities—making regulatory requirements easier to implement within obligation-subject frameworks.
DeFi, by contrast, resembles a “public financial infrastructure with weak control surface + strong composability.” In many cases, protocols themselves lack fund-freezing capabilities; actual risk-control points are dispersed across frontend interfaces, routing protocols, wallet authorization steps, stablecoin issuers, and on-chain infrastructures.
This causes the same risk to manifest differently: in CEX contexts, it may appear as suspicious on/off-ramp behavior and abnormal account operations; in DeFi contexts, it more likely appears as anomalous fund paths, abnormal contract interaction logic, or abnormal authorization behavior. Achieving comprehensive compliance coverage across both scenarios requires building a technical system capable of cross-scenario understanding of fund intent and flexible mapping of control actions to diverse control surfaces.
2. AI-Driven AML Practices
Under these structural challenges, AI’s core value in Web3 AML lies not in “generating compliance reports” but in compressing complex on-chain fund flows and interaction logic into executable compliance closed loops: detecting anomalous risks earlier, explaining risk causes more clearly, triggering disposition actions faster, and leaving complete, auditable evidence chains.
On-chain address profiling and behavioral analysis constitute the foundational first step of AML work. This profiling goes beyond simple label-assigning to deep contextual analysis: which contracts/protocols does the address interact with frequently? Is fund sourcing excessively concentrated? Does transfer rhythm exhibit classic money-laundering traits—splitting → consolidation → re-splitting? Does it associate directly or indirectly with known high-risk entities (e.g., blacklist addresses, suspicious trading platforms)? Combining LLMs with graph-learning techniques commonly serves to aggregate seemingly fragmented, unconnected transaction records into structured objects more likely belonging to the same entity or criminal chain—upgrading subsequent compliance disposition from “monitoring individual addresses” to “monitoring actual controlling entities,” greatly enhancing compliance efficiency and accuracy.
Building upon this, fund-flow tracking and cross-chain tracing assume the critical task of linking risk intent with ultimate consequences. Cross-chain operations aren’t merely transferring tokens from Chain A to Chain B—they often involve asset-format conversion, fund-path obfuscation, and new intermediary risks. AI’s core role lies in automatically tracking and continuously updating downstream fund-flow paths—when suspicious source funds begin moving, the system must not only precisely follow every step but also instantly assess which key nodes (e.g., CEX deposit addresses, stablecoin issuer contracts) the funds are approaching—nodes where freezing, joint investigation, or interception remain possible. This explains why the industry increasingly emphasizes real-time alerts over post-hoc reviews: once funds enter irreversible diffusion phases, freezing/recovery costs surge while success rates plummet.
Further, smart-contract and AI-Agent behavioral risk assessment expands the risk-control perspective from mere fund flows to execution logic. Contract-risk assessment’s core difficulty lies in business-logic complexity and frequent compositional invocation—traditional rules and static-analysis tools easily miss implicit assumptions across functions, contracts, and protocols—causing risk-identification failures. AI technologies excel at semantic-level deep understanding and adversarial hypothesis generation: they first clarify core contract information—key state variables, permission boundaries, fund-flow rules, external dependencies—then conduct scenario hypotheses and simulation validations for anomalous invocation sequences—precisely identifying potential compliance risks at the contract level.
Agent behavioral risk assessment focuses more on “strategy and permission governance”: what operations did the AI Agent perform within what authorization scope? Did invocation frequency or scale exhibit anomalies? Did it persistently execute trades under adverse market conditions (e.g., abnormal slippage, low liquidity)? Do these operations conform to predefined compliance strategies? Such behaviors require real-time logging, quantitative scoring, and automatic downgrade or circuit-breaking upon triggering risk thresholds.
To truly convert these compliance capabilities into industry productivity, clear productization pathways are needed: the base layer integrates multi-chain data and security intelligence deeply; the middle layer builds entity-profiling and fund-path analysis engines; the top layer provides real-time risk-alert and disposition-process orchestration functions; the outermost layer outputs standardized audit reports and evidence-chain retention capabilities. Productization is essential because the challenge in compliance and risk control lies not in single-analysis accuracy but in sustained operational adaptability: compliance rules evolve with regulatory requirements, malicious tactics constantly upgrade, and on-chain ecosystems iterate continuously—only systematic, learnable, updatable, and traceable products can effectively address these dynamic changes.
For on-chain risk identification and AML capabilities to truly function, the key isn’t single-model accuracy but whether they’re productized into continuously operating, auditable, and collaborative engineering systems. Take BlockSec’s Phalcon Compliance product as an example: its core philosophy isn’t simply flagging high-risk addresses but linking risk detection, evidence retention, and subsequent disposition processes into a complete closed loop—via address-tagging systems, behavioral-profiling analysis, cross-chain fund-path tracking, and multidimensional risk-scoring mechanisms—providing Web3 compliance work with an all-in-one solution.
Against the industry backdrop of widespread AI and Agent participation in trading and execution, such compliance capabilities gain heightened importance: risks no longer stem solely from active attacks by “malicious accounts” but may also arise from passive violations caused by automated-strategy misexecution or permission abuse. Pre-positioning compliance logic into trading and execution chains—identifying and flagging risks before irreversible settlement completes—is becoming a critical component of intelligent-trading-era risk-control systems.
3. New Compliance Propositions in the Machine-Trading Era
As trading shifts from “human-operated interfaces” to “machine-called APIs,” compliance domains face new propositions: regulatory targets extend beyond transaction behaviors themselves to include the protocols and automation mechanisms enabling those transactions. Discussions around the x402 protocol matter not only because it enables smoother, more efficient inter-machine payments but also because it deeply embeds payment functionality into HTTP interaction flows—enabling “Agent economy” automatic-settlement models.
Once such mechanisms achieve scale adoption, compliance focus shifts toward “under what authorization and constraints do machines complete payments and transactions”: whose Agent, at what fund limits, under what strategy constraints, paying for what resources, and whether anomalous circular payments or induced invocation behaviors exist—all requiring complete recording and auditability.
Closely following is the challenge of responsibility assignment. AI Agents themselves aren’t legal entities, yet they can represent individuals or institutions in executing transactions—potentially causing substantial fund losses or compliance risks. When Agent decisions rely on external tools, external data, or even third-party payable capabilities (e.g., certain data APIs or transaction-execution services), responsibility becomes difficult to cleanly delineate among developers, operators, users, platforms, and service providers.
A more realistic, operationally feasible engineering direction is embedding responsibility traceability into system-design cores: all high-impact actions default-generate structured rationale chains—including trigger-signal sources, risk-assessment processes, simulation-validation results, authorization-scope boundaries, and final-execution transaction parameters—and version-manage key strategies and parameters with full replay support—enabling rapid root-cause identification upon incidents: was it flawed strategy logic, erroneous data input, misconfigured authorization, or compromised toolchain?
Finally, RegTech (Regulatory Technology) evolution will shift from traditional “post-hoc screening tools” to “continuous monitoring and executable-control infrastructure.” This means compliance ceases being merely an internal departmental process—it becomes a set of standardized platform capabilities: the policy layer encodes regulatory requirements and internal risk-control rules into executable code (“policy-as-code”); the runtime layer continuously monitors fund paths and behavioral patterns of market participants; the control layer implements core actions—transaction delays, fund limits, risk isolation, emergency freezes; the collaboration layer rapidly pushes verifiable evidence to all action-capable ecosystem participants (e.g., exchanges, stablecoin issuers, law-enforcement agencies).
As machine payments and machine trading become standardized, they remind us: compliance capabilities must undergo identical interface-ization and automation upgrades—otherwise, the structural gap between high-speed machine trading and low-speed human compliance becomes unbridgeable. AI technology offers risk control and AML the opportunity to become front-loaded infrastructure for the intelligent-trading era: through earlier warnings, faster collaboration, and more executable technical means, compressing risks into minimal-impact windows—providing core support for Web3 industry compliance development.
Conclusion
Reviewing the full text reveals clearly that AI’s integration with Web3 isn’t a simple point-technology upgrade but a comprehensive, unfolding system-wide paradigm shift: trading is moving toward machine executability; attacks are simultaneously becoming machine-driven and scalable; and security, risk control, and compliance are compelled to evolve from traditional “support functions” into indispensable front-loaded infrastructure for intelligent trading systems. Efficiency and risk are no longer sequential phases but are simultaneously amplified and accelerated—exhibiting a positive correlation: “the higher the efficiency, the higher the risk-control requirements.”
On the trading side, AI and Agent systems significantly lower information-acquisition and transaction-execution barriers—reshaping market participation methods and enabling more users to engage in Web3 trading—yet introduce new risks like strategy congestion and erroneous execution; on the security side, automation of vulnerability discovery, attack generation, and fund laundering concentrates and accelerates risk outbreaks—raising higher demands on defense systems’ response speed and disposition capability; on the risk-control and compliance side, address profiling, path tracking, and behavioral analysis technologies evolve from pure analytical tools into engineering systems with real-time disposition capability—while machine-payment mechanisms like x402 further push compliance issues toward deeper directions: “how are machines authorized, constrained, and audited?”
All this points to a clear conclusion: what’s truly scarce in the intelligent-trading era isn’t faster decision speed or more aggressive automation—but security, risk-control, and compliance capabilities aligned with machine-execution speeds. These capabilities must be designed as executable, composable, and auditable complete systems—not passive, post-hoc processes.
For trading platforms, this means embedding risk boundaries, logical evidence chains, and human oversight mechanisms deeply into AI systems while enhancing trading efficiency—achieving “efficiency and security in tandem”; for security and compliance infrastructure providers, this means shifting monitoring, alerting, and blocking capabilities ahead of funds losing control—building “proactive defense, real-time response” protection systems.
BlockSec and Bitget jointly judge that, for the foreseeable future, the key determinant of whether intelligent trading systems achieve sustainable development won’t be who embraces AI technology faster—but who earlier implements both “machine-executable” and “machine-constrainable” capabilities. Only under parallel evolution of efficiency enhancement and risk constraint can AI truly become Web3’s long-term incremental force—not an amplifier of systemic risk.
The fusion of Web3 and AI is an inevitable industry trend, while security, risk control, and compliance constitute the core guarantee for this trend’s steady, long-term progress. BlockSec will continue deepening its expertise in Web3 security—delivering stronger, more reliable security protection and compliance support through technological innovation and product iteration—and collaborating with industry partners like Bitget to drive healthy, sustainable development in the intelligent-trading era.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News














