The biggest cryptocurrency scams of 2024
TechFlow Selected TechFlow Selected

The biggest cryptocurrency scams of 2024
2024 has been a brutal year for Web3 retail investors, with far too many investors robbed by scammers and hackers.
Author: NEFTURE SECURITY
Translation: Baihua Blockchain
2024 has been an exceptionally brutal year for Web3 retail investors. Countless investors have been robbed by scammers and hackers.
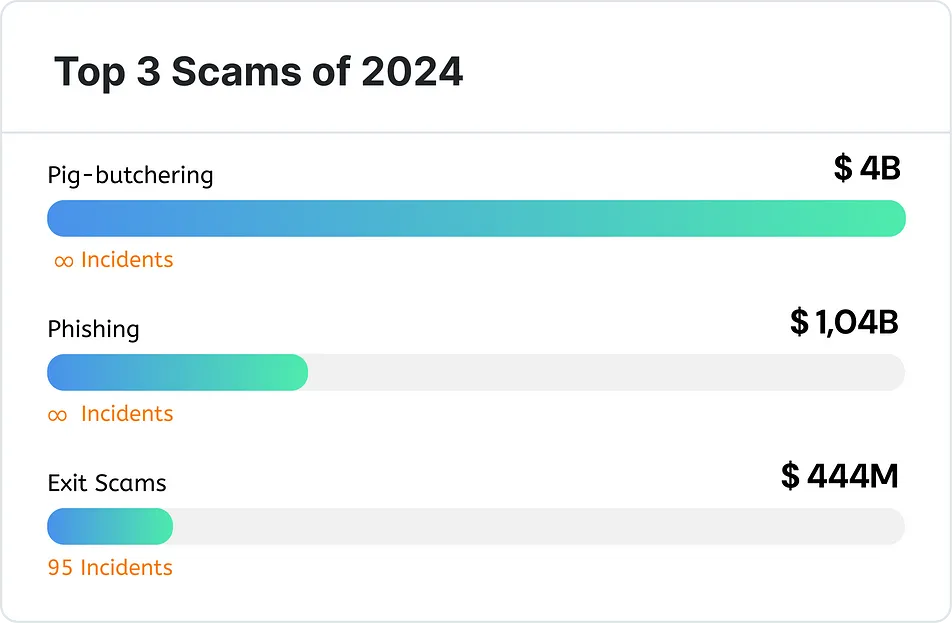
While obtaining precise figures on retail investor losses remains extremely difficult, crime reports indicate that at least $5.84 billion was wiped out from their wallets. Of this, at least $4 billion was lost to "pig-butchering" scams, over $1 billion to phishing attacks (including wallet theft and address poisoning), and $444 million attributed to exit scams.
It must be noted that the cryptocurrency market conditions in 2024 indeed provided tremendous opportunities for these fraudsters.
The bull run beginning at the end of 2023 peaked on March 14, 2024, when Bitcoin reached a new all-time high of $73,738, drawing massive liquidity not only from seasoned crypto enthusiasts but also a large influx of eager retail newcomers. 2024 was widely seen as the year Bitcoin would break the $100,000 barrier (and it did!), combined with explosive meme coin activity, transforming the ghost-town crypto markets of 2023 into vibrant trading hubs!
Source: Dune
Many newcomers were completely unaware of the treacherous waters of cryptocurrency, making them highly vulnerable and ideal targets for scammers. Meanwhile, experienced traders, emerging from a long and painful bear market, were equally or even more susceptible to FOMO (fear of missing out), creating the perfect environment for fraudsters to prey on retail investors.
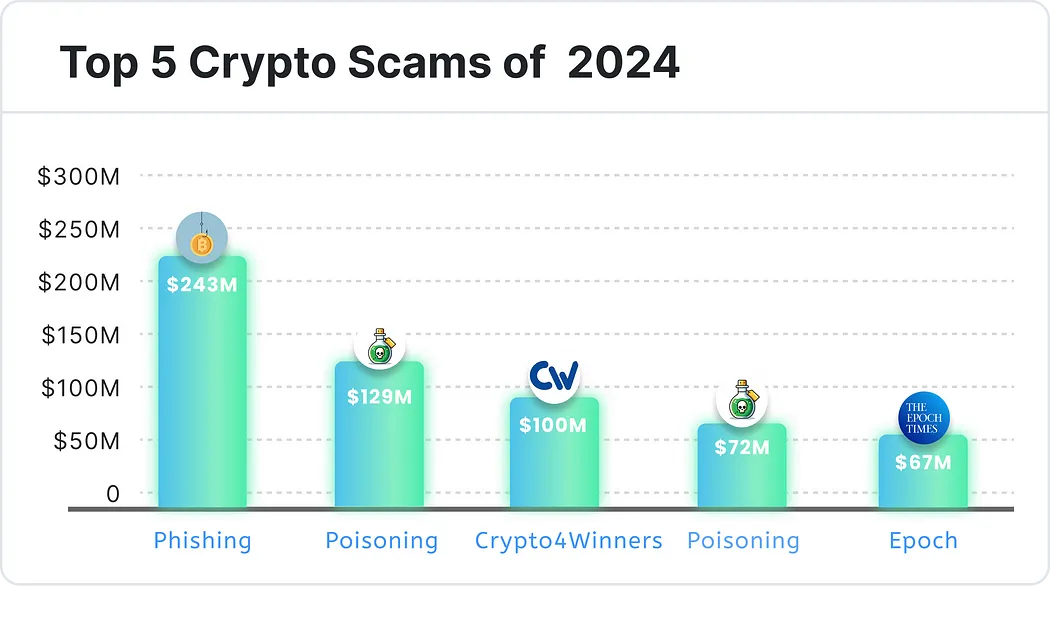
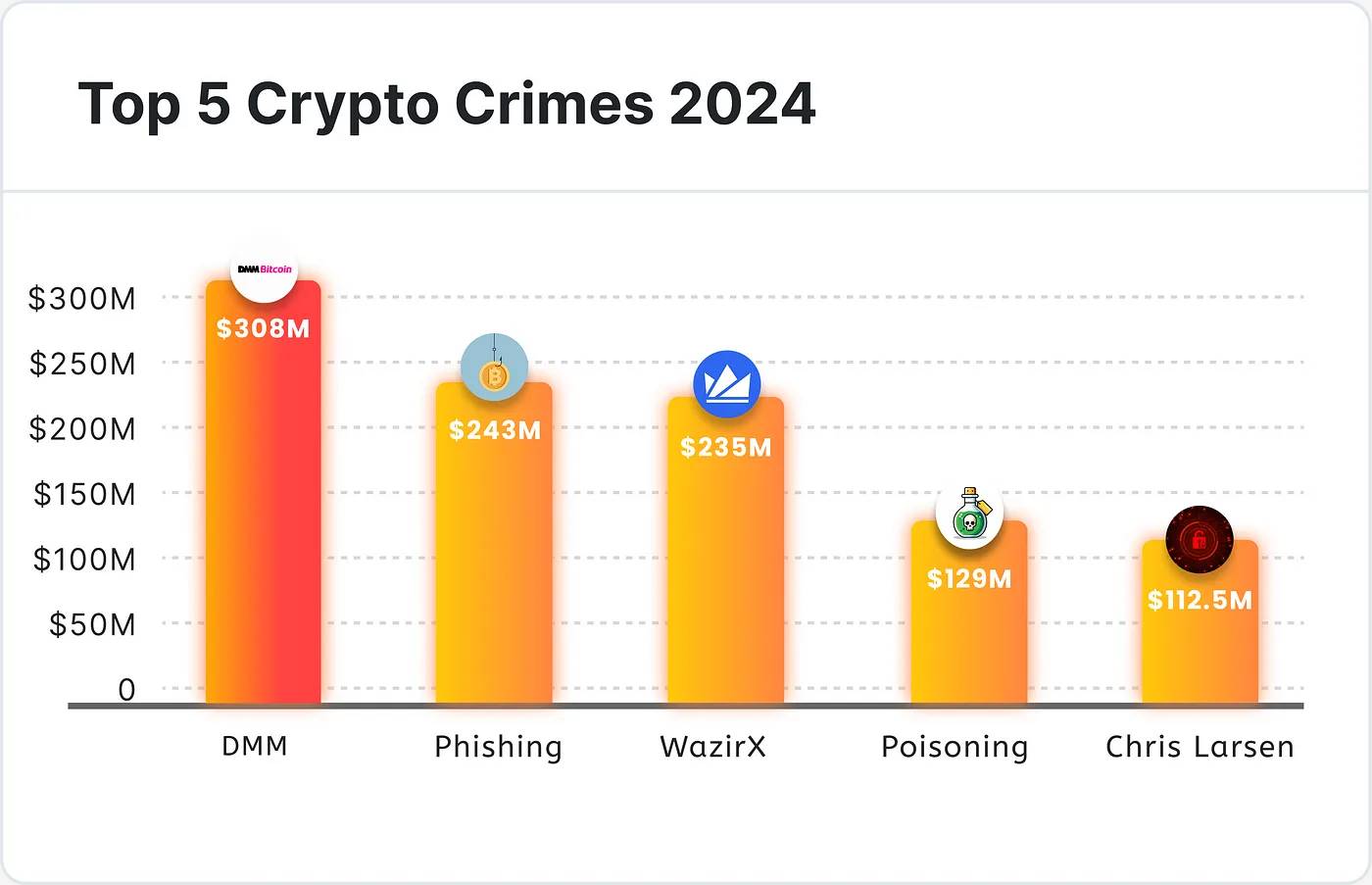
Shockingly, excluding pig-butchering scams, the top five fraudulent projects in 2024 caused staggering losses totaling $611 million.
Below are the most successful cryptocurrency scams of 2024!
1. $243 Million Stolen: The Largest Social Engineering Phishing Heist to Date — Second-Largest Robbery of the Year
The most jaw-dropping cryptocurrency scam of 2024 was a simple social engineering phishing attack, ranking as the second most financially destructive crime of the year, surpassed only by the North Korean threat group’s $308 million private key attack on DMM Bitcoin.
To date, this also appears to be the largest single loss suffered by an individual in a single crypto phishing attack.
On August 19, 2024, crypto investigator ZachXBT revealed on Twitter a suspicious $238 million transfer, with funds laundered and cashed out through multiple centralized exchanges (CEXs). Rumors quickly circulated about the victim's identity—was it an individual, a hedge fund, or an exchange? How was the heist executed: via private key compromise, phishing, or both?
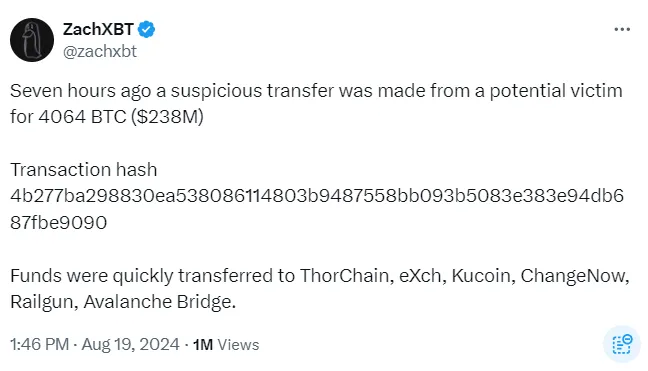
For a long time, little detail emerged beyond two updates from ZachXBT, reporting that Firn Protocol and NonKYC successfully froze approximately $500,000 in stolen funds—a mere drop in the bucket.
A month later, exactly one month after the $238 million attack, ZachXBT returned to Twitter to reveal the full story behind the incident.
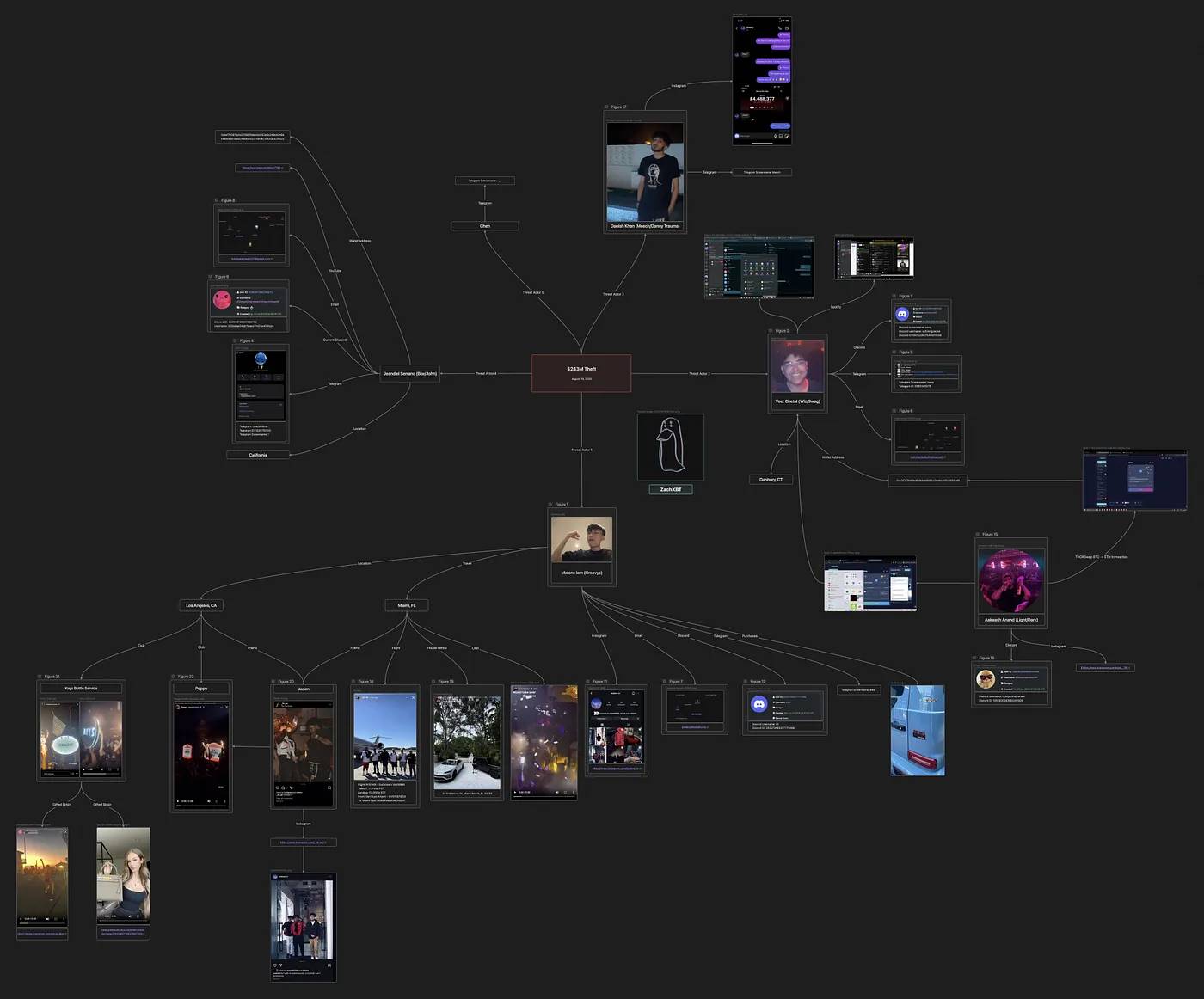
ZachXBT’s investigation map — Source: ZachXBT
The robbery was a "highly sophisticated social engineering attack," a phishing scam targeting a single individual. The victim was a creditor of the now-bankrupt crypto trading firm Genesis.
On the day of the attack, he received a fraudulent call impersonating Google Support, which allowed the attackers to breach his personal account. According to ZachXBT’s investigation, the victim then received another call, this time from someone pretending to be Gemini Support, claiming his Gemini account had been hacked and instructing him to reset his two-factor authentication (2FA) and move funds from his Gemini account.
After repeated persuasion, the victim shared his screen using AnyDesk, enabling the scammers to access and leak the private key of his Bitcoin Core wallet.
The attackers successfully stole $243 million and immediately attempted to disperse the funds across multiple wallets before transferring them to over 15 exchanges. According to ZachXBT’s research, the stolen assets were rapidly converted between Bitcoin, Litecoin, Ethereum, and Monero to obscure the trail.
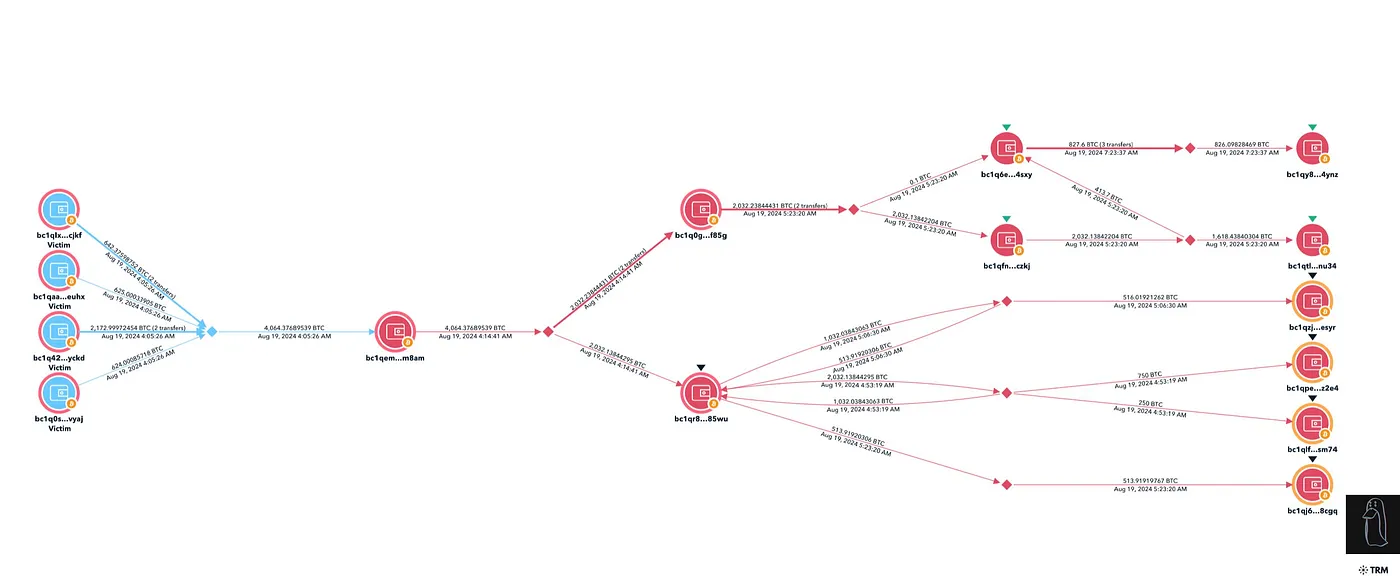
ZachXBT’s initial vulnerability tracking — Source: ZachXBT
Unfortunately for them, fortunately for the victim, they were not cautious enough during the attack and escape. This negligence allowed ZachXBT to trace the phishing attack back to three main suspects and their accomplices.
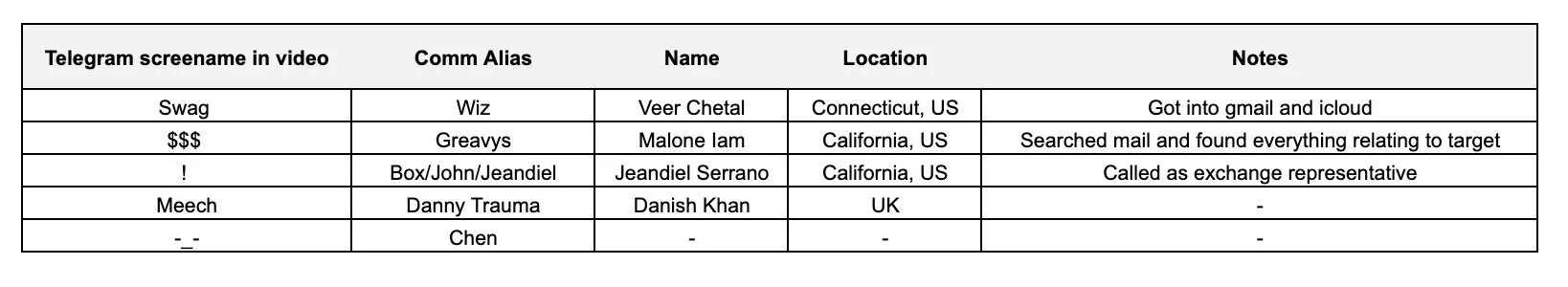
Suspect list compiled by ZachXBT — Source: ZachXBT
One of their many mistakes was revealing the names of two individuals during the screen-sharing session.
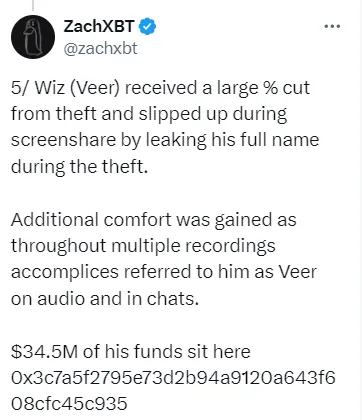
Source: ZachXBT Twitter
Other errors related to their money laundering techniques. Although the attackers converted most of the stolen funds into Monero, ZachXBT found that two of them accidentally mixed stolen and clean funds by reusing deposit addresses. One attacker also exposed an address used to purchase luxury clothing during the screen share, which was linked to millions of dollars in stolen funds.
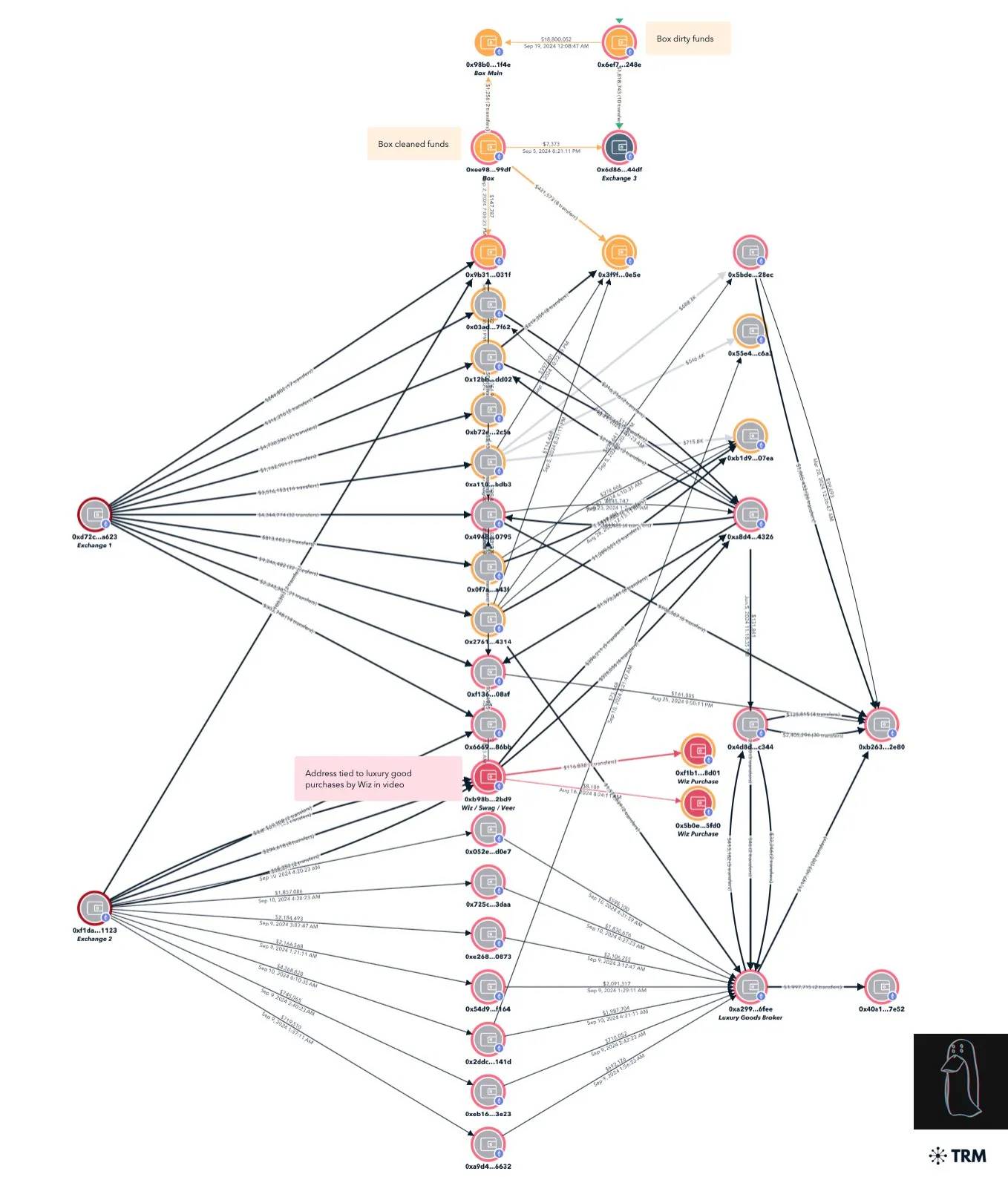
Source: ZachXBT Twitter
Most of them left sufficient traces on social media—or their former associates did—ultimately exposing their full identities during ZachXBT’s investigation. Collaborating with BN Security Team, Zero Shadow, and CryptoForensic Investigators, ZachXBT further froze $9 million.
The day before ZachXBT published his findings, Box (Jeandiel Serrano, 21 years old) and Greavys (Malone Lam, 20 years old) were arrested by the FBI and formally charged on September 19.

Malone Lam — Source: ZachXBT
Phishing attacks conducted through social engineering have long been central to many high-yield crypto heists, including one particularly complex attempt that nearly succeeded in stealing $125 million from a single individual.
2. $129 Million Address Poisoning Attack in November 2024

On November 20, 2024, a victim decided to transfer approximately $129.7 million from address TGrS7QNCf85X2B6ddvGZY2MF9VwvFn6XAE to TMStAjRQHDZ8b3dyXPjBv9CNR3ce6q1bu8.
They first sent 100 USDT as a test transaction to address TMStaj…6q1bu8. After the transaction completed successfully, the victim almost immediately decided to transfer the full $129.7 million.
What they didn’t know was that shortly after the test transaction, the scammer had “dusted” their wallet (sent 1 USDT) via an address mimicking the test address. When the victim copied and pasted the destination address, they inadvertently selected this fake address. The spoofed address was poorly forged—only the last six digits matched, while the beginning was completely different, starting with THcTxQ instead of TMStaj.
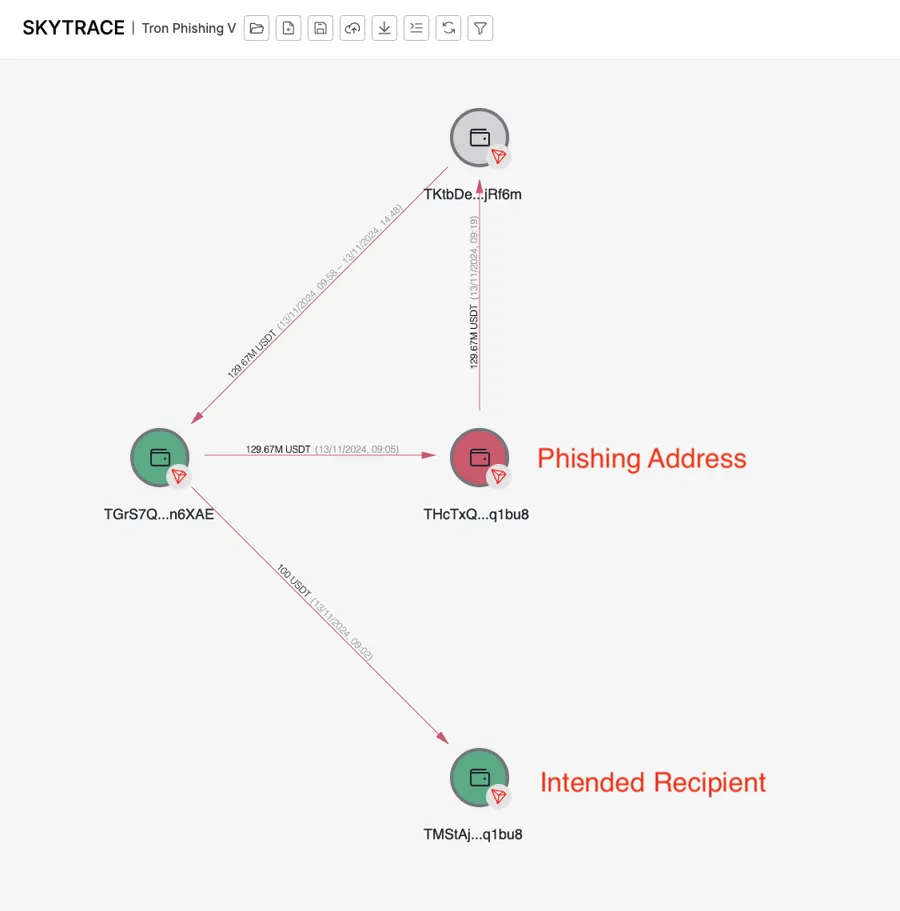
Source: Certik
Luckily, the address poisoner returned $116.7 million within one hour and the remaining $12.97 million four hours later.
The two transfers—and the amount of the second transfer ($12.97 million)—suggest that the attacker initially considered taking a 10% “bug bounty” but later changed their mind.
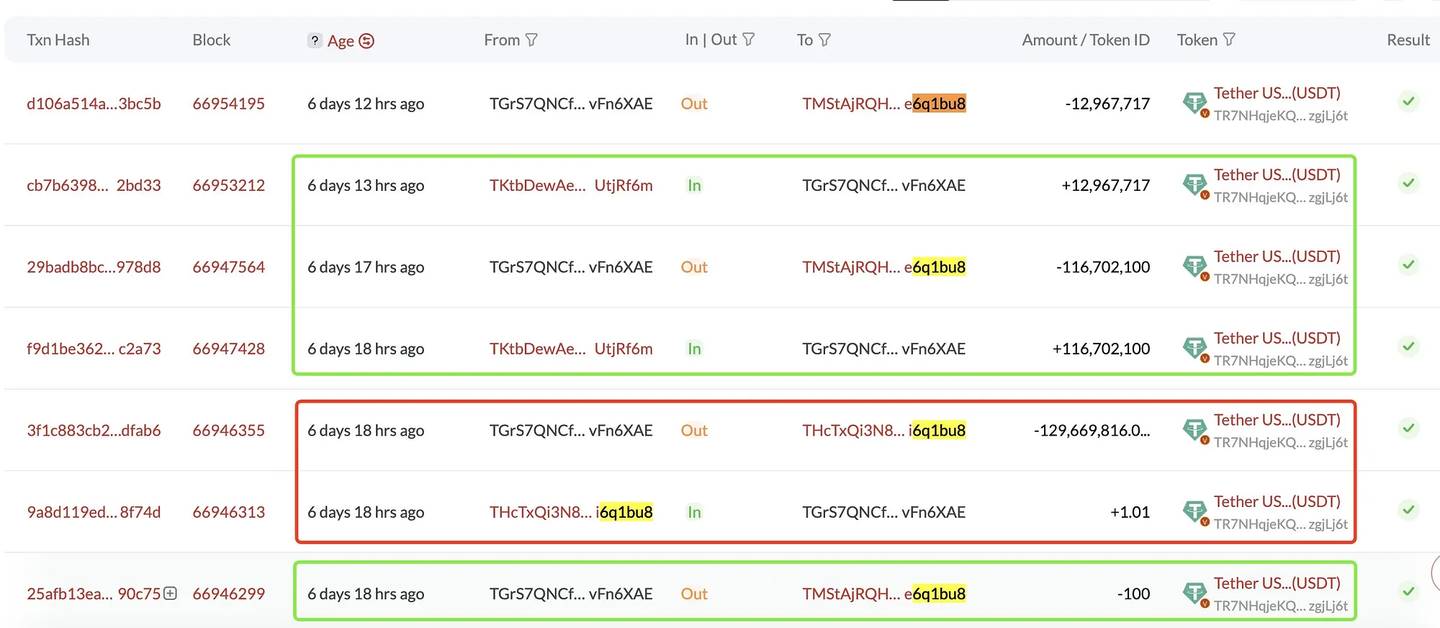
Source: SlowMist via ScamSniffer
The most likely reason they returned all funds was fear—fear of being tracked down by a well-resourced victim, the blockchain forensics community, and law enforcement, especially given the enormous sum involved, which made them a huge target.
3. Crypto4winners: $100 Million Ponzi Scheme

On March 9, 2024, investment firm Crypto4winners—which promised monthly returns of 3–20%—announced they had suffered a security breach.
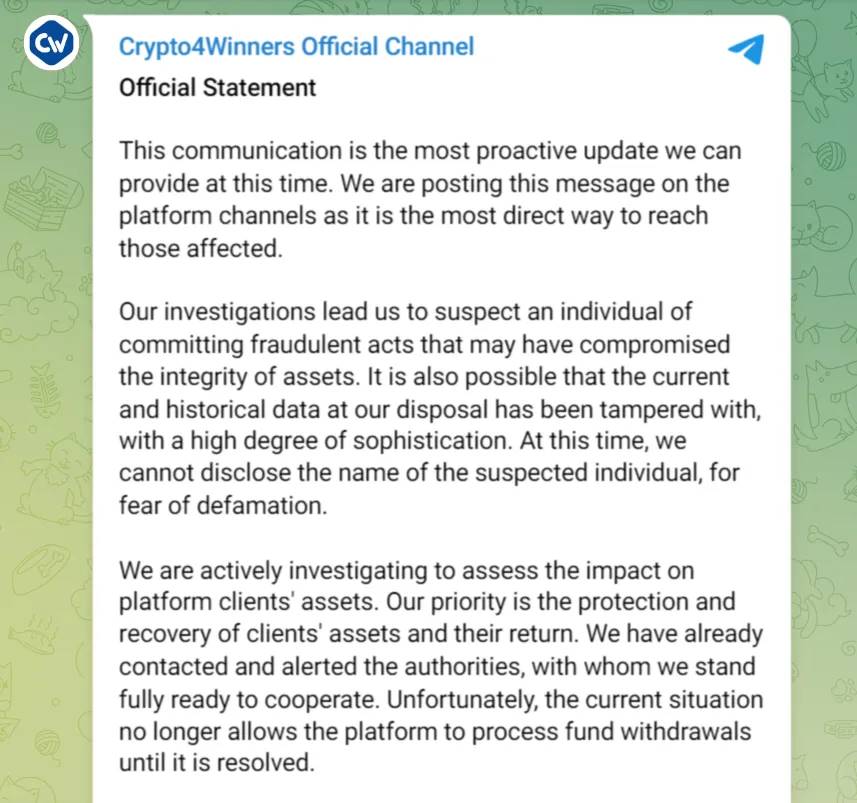
Source: Crypto4winners Telegram Channel
Due to this “breach,” Crypto4winners claimed they could not process withdrawals until the issue was resolved.
The problem was that two months earlier, crypto news outlet DL News had already revealed that one of Crypto4winners’ co-owners was Luc Schiltz, a Luxembourg national who had served two years of a six-year sentence for defrauding over $1.5 million in 2017. Shortly after his release, he co-founded the Crypto4winners project.
Thus, suspicion arose immediately upon announcement of the “hack.” After the initial announcement, Crypto4winners fell completely silent. By March 12 or earlier, its customers had contacted lawyers and police.
In the following days, Crypto4winners was exposed as having all the hallmarks of a Ponzi scheme, resulting in thousands of victims and losses of at least $100 million.
According to DL News, Luc Schiltz was a co-founder of Crypto4winners but had consistently hidden his involvement. The publicly named CEO and founder was another Luxembourg national, Adrien Castellani, though in reality, Castellani merely co-founded the company with Luc Schiltz.
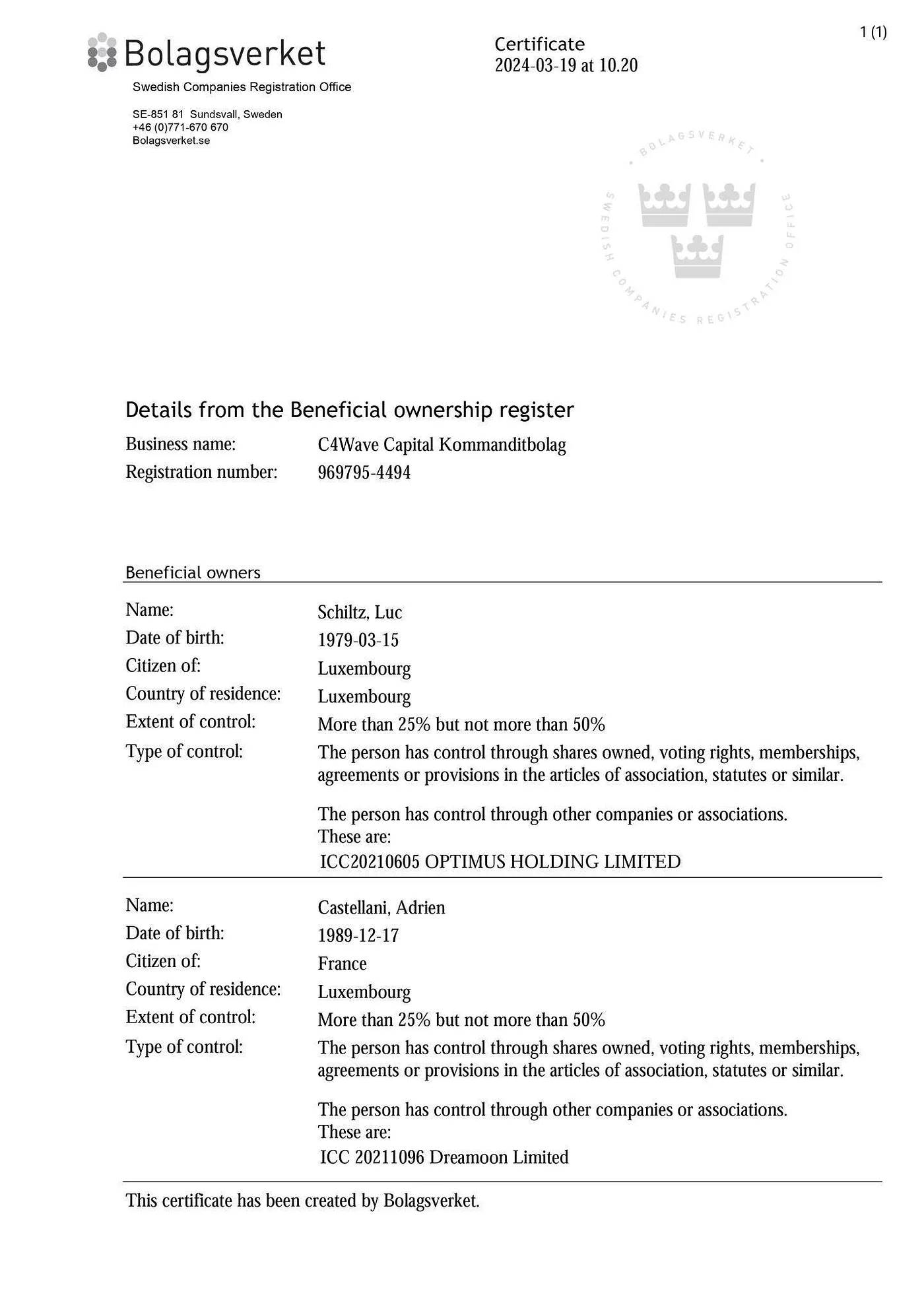
Source: Virgule
Despite ongoing questions over the years about Luc Schiltz’s role in Crypto4winners, he never acknowledged being a co-founder or partner, referring to himself only as an advisor. In 2023, he pledged to fully sever ties with Crypto4winners by year-end—a promise clearly unfulfilled.

Source: DL News
The lies were endless.
Take their promised outrageous returns. They claimed customer Bitcoin deposits had yielded a 377% return since 2019 and average monthly returns of 7% to 20%, regardless of market movements—classic signs of a crypto Ponzi scheme.
They also falsely claimed partnerships with Chainalysis and Ledger, prompting both companies to publicly deny these claims in 2022.
Crypto4winners was registered in Sweden. In 2023, when the Swedish Companies Registration Office requested annual reports for 2021 and 2022, they falsely claimed exemption as a trust management firm. Despite facing liquidation or invalidation risks, they failed to submit the reports by the deadline.
Further investigation revealed that although Crypto4winners appeared to be a Luxembourg-Swedish entity, it operated through a complex structure involving Dubai, Lithuania, Ireland, Sweden, and Luxembourg.
Worse still, Crypto4winners was essentially a shell company; all investor funds were transferred to an Irish company called Big Wave Developments Limited.
According to Luxembourg newspaper Virgule, of the estimated $100 million in customer funds, less than $200,000 remained in Big Wave Developments Limited’s accounts.
The most astonishing aspect of this entire case is how it unraveled: a bizarre car accident allegedly causing Luc Schiltz to lose his memory.
In the early hours of March 5, Luc Schiltz crashed into a roadside barrier and his car went up a slope. According to Luxembourg police, he sustained no injuries in the crash but then inexplicably walked onto the highway, where he was struck by a bus.
He survived without fatal injuries and was hospitalized for orthopedic treatment.
However, he claimed the accident caused memory loss. The problem was that Luc Schiltz had sole control over customer funds, meaning he could no longer access the cryptocurrency wallets and exchange accounts containing the money.
Notably, according to investigations by Virgule and people who visited Luc Schiltz shortly after the accident, his amnesia appeared questionable.
Mario, a friend of Adrien Castellani who uses a pseudonym, recalled to Virgule:
"He initially pretended to have amnesia, then told us he would retrieve the USB key from his parents and everything would return to normal..." (translated from French)
That very day, Mario discovered the shell nature of Crypto4winners and Big Wave Developments Limited. Later, during a March 12 phone call with Shiltz, Mario asked about the mere $200,000 remaining in the Big Wave Developments Limited account, and Shiltz reassured him this was normal because it was just funds in a hot wallet.
Despite claiming memory loss, Luc Shiltz seemed fully aware of his identity and how the company operated. So what exactly did he forget that prevented him from accessing the funds? Clearly not the seed phrase; in crypto history, it’s almost unheard of for someone to manage $100 million solely from memory.
He himself said everything was with his parents and promised things would soon return to normal. So where was the problem?
Hopefully, this incident and all the questions it raises will be answered in court.
On March 15, the Luxembourg Public Prosecutor’s Office announced an investigation into Crypto4winners for fraud and money laundering, with two individuals detained and charged.
One of them is believed to be Luc Shiltz.
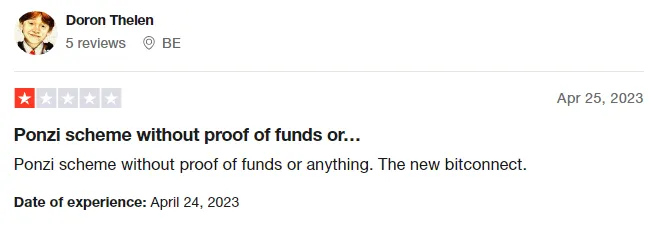
Source: TrustPilot
4. $72 Million Address Poisoning Attack in May 2024

On May 3, 2024, an individual fell victim to an address poisoning attack, which became the largest such heist in history at the time, losing 1,155 wrapped Bitcoins worth $72.7 million.
The incident boiled down to extreme bad luck. The victim first successfully completed a $149 test transaction to a legitimate address (starting with 0xd9A1b). Afterwards, they mistakenly copied and pasted a fake address—a poisoned address mimicking 0xd9A1b.
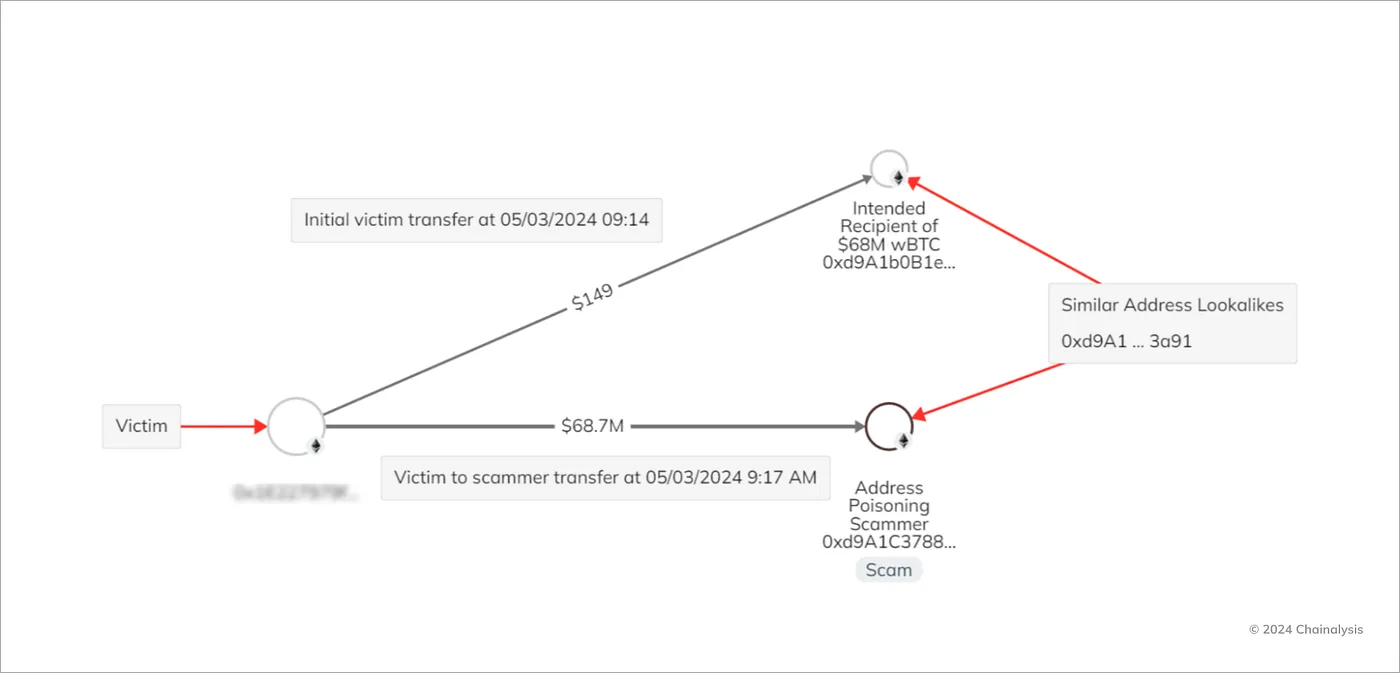
Breakdown of address poisoning — Source: Chainalysis
The victim attempted to negotiate the return of funds with a 10% “bug bounty,” but failed. The attacker, blinded by greed, thought they could get away with it—but they were dead wrong.
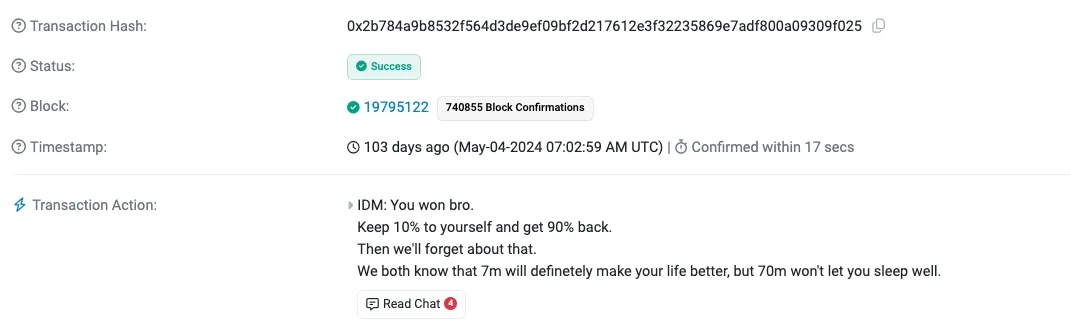
Message from victim to attacker — Source: Chainalysis
The entire blockchain security community launched an investigation, and news soon emerged that the attacker had returned the funds, keeping only $7.2 million as a “bug bounty.” On May 10, the attacker returned nearly all stolen funds, walking away with only $3 million due to token appreciation.
Two weeks later, it was discovered that the swift return wasn’t due to conscience—but because despite their best efforts to cover tracks, their “device fingerprint” partially exposed their identity, according to Match Systems CEO Andrey Kutin.
5. Epoch Times CFO’s $67 Million Crypto Fraud and Money Laundering Heist

In June 2024, Bill Guan, Chief Financial Officer of Epoch Times, was arrested over a major crypto fraud scheme.
The U.S. Department of Justice (DOJ) charged Guan with conspiring to launder at least $67 million in illicit proceeds, including funds obtained through unemployment insurance fraud. The scheme allegedly involved purchasing illegal funds at a discount using cryptocurrency, then routing them through multiple accounts—including those of Epoch Times—to conceal the source.
The fraud came to light when banks reported its revenue surged 410% from $15 million to over $62 million in a single year.
The DOJ emphasized that the charges are unrelated to Epoch Times’ journalistic activities. Guan faces serious charges including conspiracy to commit money laundering and bank fraud, potentially leading to up to 80 years in prison.
6 Summary
In 2024, the Web3 space proved perilous for retail investors. Fraud and hacking ran rampant, resulting in investor losses totaling $5.84 billion, with pig-butchering scams, phishing attacks, and exit scams being the primary forms of crime. From Bitcoin’s bull market to the meme coin supercycle, market exuberance attracted vast numbers of new and experienced investors alike—yet also made them prime targets for scammers. Nevertheless, there were some positive signals, such as partial recovery of stolen funds and vigorous pursuit of criminals by law enforcement and the blockchain security community.
Yet these events also serve as stark reminders: risks in the cryptocurrency market are ever-present. While pursuing high returns, investors must remain vigilant, strengthen their security awareness, and carefully consider every investment decision to avoid becoming the next victim.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News