SharkTeam: Web3 Security Report Q1 2024
TechFlow Selected TechFlow Selected

SharkTeam: Web3 Security Report Q1 2024
In the first quarter of 2024, malicious activities such as hacking attacks, rug pulls, and phishing scams caused total losses of $462 million, representing a year-on-year increase of approximately 20.63% compared to the first quarter of 2023 (about $383 million).
Author: SharkTeam
1. Overview
In the first quarter of 2024, malicious activities such as hacking attacks, Rugpull scams, and phishing attacks resulted in total losses of $462 million, representing a year-on-year increase of approximately 20.63% compared to the first quarter of 2023 (around $383 million). This report aims to compile and analyze the global Web3 industry's security landscape, major incidents, and security trends in Q1 2024, providing readers with valuable insights and new perspectives, and contributing to the safe and healthy development of Web3.
2. Security Incident Analysis
According to data from SharkTeam’s on-chain security analysis platform ChainAegis, there were 280 security incidents in the Web3 sector during the first quarter of 2024 (Figure 1), resulting in cumulative losses exceeding $462 million (Figure 2). Compared to the same period last year, the frequency of security incidents increased by approximately 32.70%, while financial losses rose by about 20.63%.
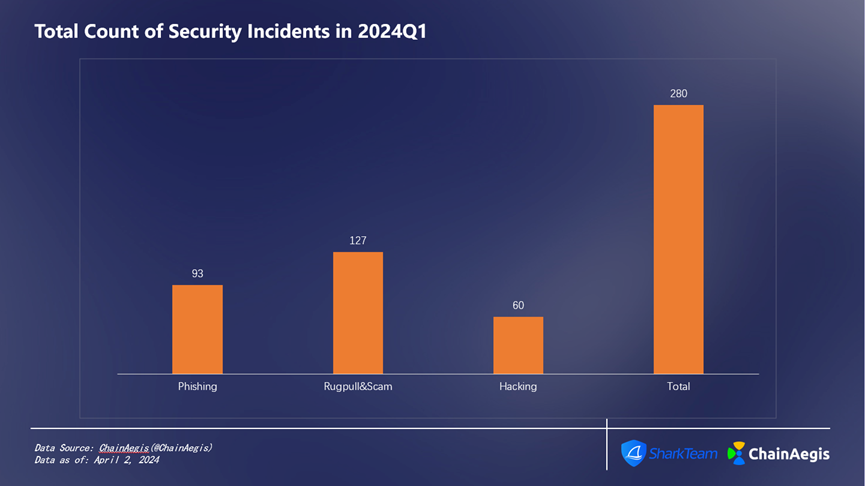
Figure 1: Total Count of Security Incidents in 2024Q1
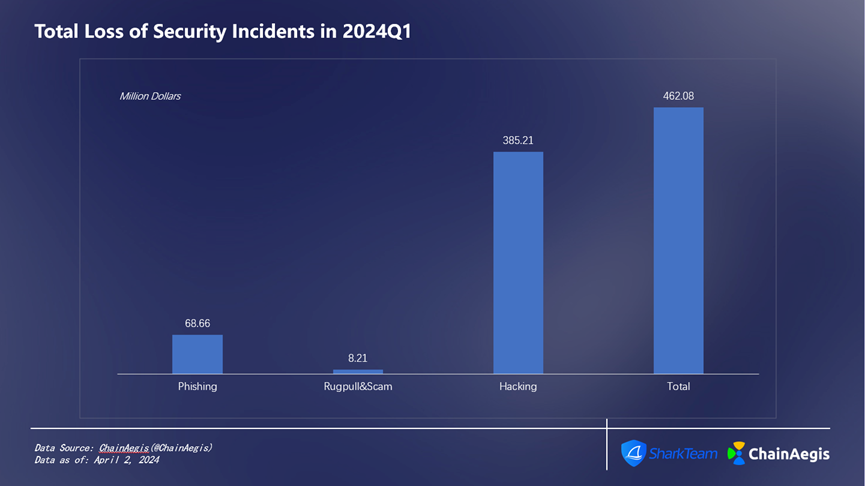
Figure 2: Total Loss of Security Incidents in 2024Q1
In Q1 2024, there were 60 hacking attacks, an increase of 140% compared to Q1 2023, causing losses amounting to $385 million, accounting for 83% of total losses (Figure 3), which represents a 6.35% increase compared to $362 million in Q1 2023.
Rug Pulls occurred 127 times, surging 323.33% compared to 30 incidents in Q1 2023, but the financial loss decreased by 59.44%, totaling $8.21 million, or 2% of the total quarterly losses.
Phishing attacks totaled 93 incidents in Q1, showing a year-on-year increase, with losses amounting to approximately $68.66 million, accounting for about 15% of total losses.
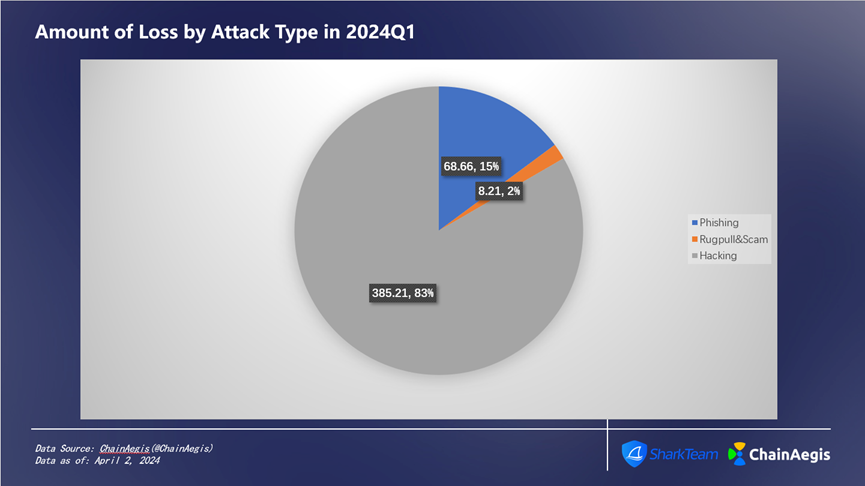
Figure 3: Amount of Loss by Attack Type in 2024Q1
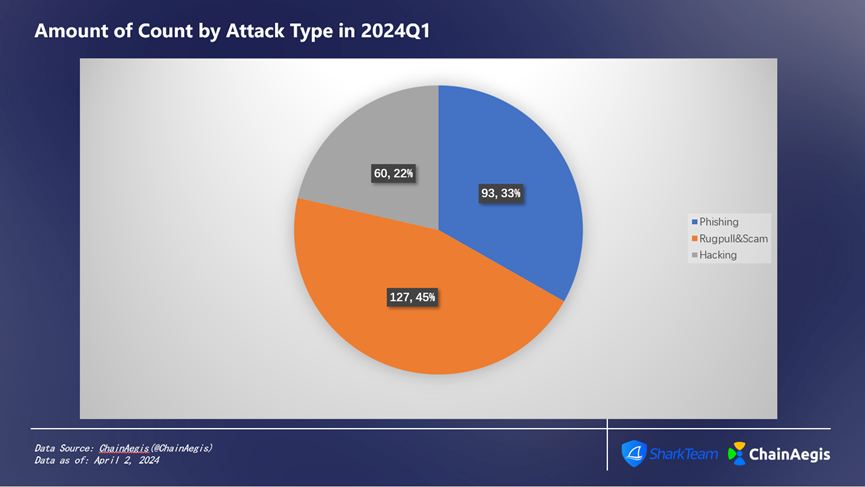
Figure 4: Number of Incidents by Attack Type in 2024Q1
When analyzing Q1 month-by-month (Figure 5), January saw the highest losses, exceeding $250 million, far surpassing February ($71.42 million) and March ($140 million). There were 88 security incidents in January, slightly higher than 72 in February and slightly lower than 120 in March, indicating that individual incidents in January had the highest average loss. The primary cause of January's severe losses was hacking attacks, with 20 incidents causing $217 million in damages. At the same time, phishing attacks were also prevalent in January, with 39 incidents reported, although their total loss was relatively low at $29.15 million. February experienced relatively fewer incidents and lower losses compared to January and March.
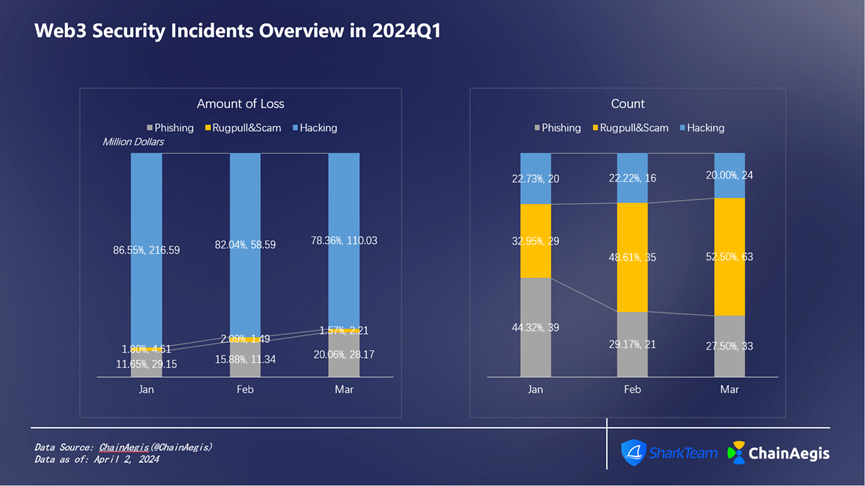
Figure 5: Web3 Security Incidents Overview in 2024Q1
2.1 Hacking Attacks
There were 60 hacking attacks in the first quarter, resulting in total losses of up to $385 million. January suffered the most significant losses at $217 million, primarily due to two major fund theft incidents.
(1) On January 1, 2024, cross-chain bridge project Orbit Chain was compromised in a cyberattack, leading to the theft of approximately $81.5 million worth of cryptocurrency. The incident involved five separate transactions, each directed to different wallet addresses. Unauthorized fund transfers included $50 million in stablecoins (comprising $30 million USDT, $10 million DAI, and $10 million USDC), around $10 million worth of 231 wBTC, and approximately $21.5 million worth of 9,500 ETH.
(2) On January 31, 2024, four wallets belonging to Ripple co-founder Chris Larsen were attacked, resulting in the theft of 237 million XRP tokens, valued at approximately $112.5 million. ChainAegis on-chain analysis revealed that stolen funds were transferred through exchanges including MEXC, Gate, Binance, Kraken, OKX, HTX, and HitBTC. This marks the largest cryptocurrency heist of 2024 so far and ranks as the 20th-largest crypto theft in history. XRP's price dropped approximately 4.4% within 24 hours of the incident.
2.2 Rug Pull & Scams
As shown in the figure below (Figure 6), Rugpull & Scam incidents occurred 29 times in January, increasing monthly to about 63 incidents in March; losses amounted to approximately $4.51 million in January and $1.49 million in February. According to ChainAegis analysis, these incidents were concentrated mainly on the Ethereum and BNB Chain networks, with Rug Pull events occurring much more frequently on BNB Chain than on Ethereum.
Additionally, on February 25, the GameFi project RiskOnBlast within the Blast ecosystem suffered a Rugpull. According to ChainAegis analysis, the RiskOnBlast address 0x1EeB963133f657Ed3228d04b8CD9a13280EFC558 raised 420 ETH, worth approximately $1.25 million, between February 22 and 24, before converting it into DAI and transferring it to deposit addresses on exchanges such as ChangeNOW, MEXC, and Bybit for cash-out.
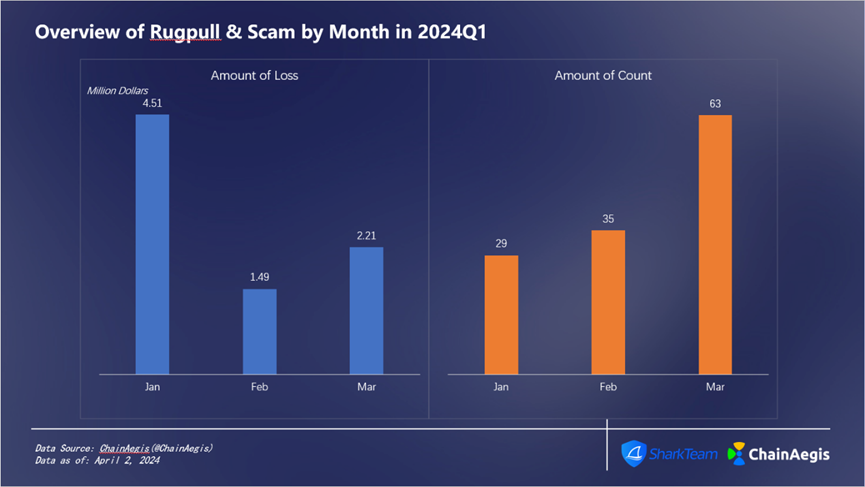
Figure 6: Overview of Rugpull & Scam by Month in 2024Q1
2.3 Phishing Attacks
As shown in the figure below (Figure 7), phishing attacks occurred most frequently in January, totaling 39 incidents and causing losses of approximately $29.15 million; February had the fewest incidents at 21, with losses of about $11.34 million. SharkTeam reminds everyone that during bull markets, when market activity increases and airdrop opportunities abound, users must remain vigilant to avoid attacks from active phishing groups like Angel Drainer and Pink Drainer. Always carefully verify transaction details before signing transfers or authorizations.
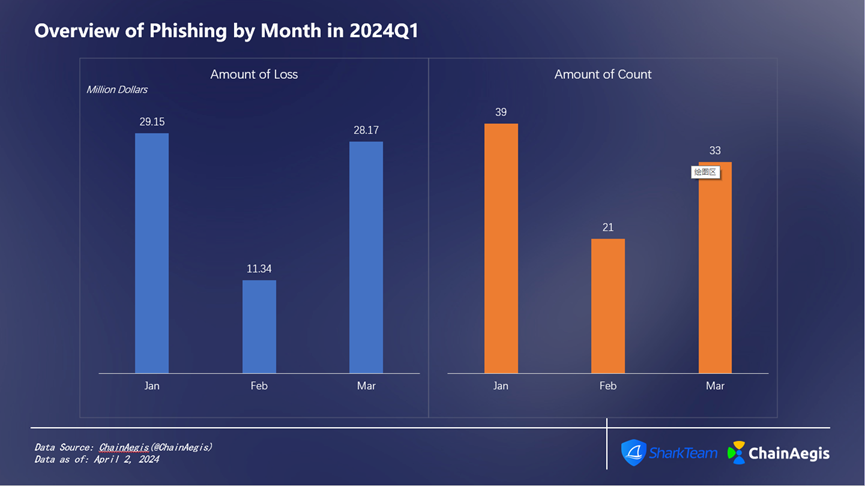
Figure 7: Overview of Phishing by Month in 2024Q1
3. Case Studies
3.1 Contract Precision Calculation Vulnerability
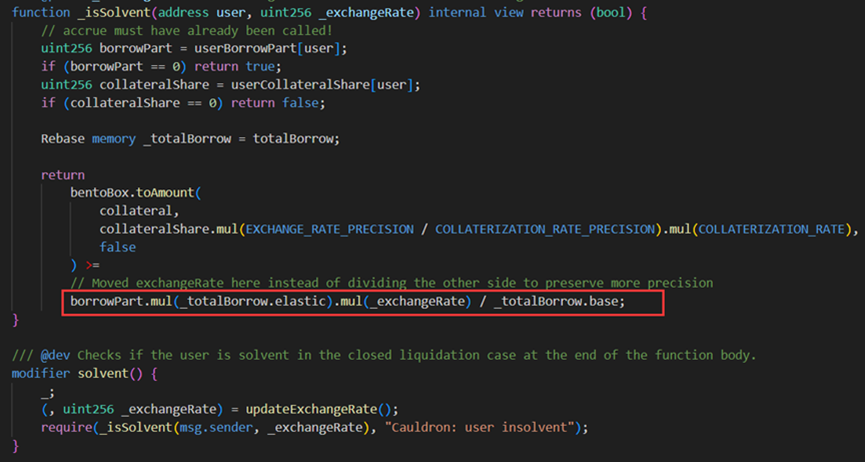
On January 30, 2024, MIM_SPELL suffered a flash loan attack due to a precision calculation vulnerability, resulting in a loss of $6.5 million. The root cause was a flaw in the project’s smart contract when calculating lending variables, allowing attackers to manipulate the key variables "elastic" and "base," causing an imbalance in their ratio. This led to incorrect calculations of collateral and loan amounts, ultimately enabling excessive borrowing of MIM tokens.
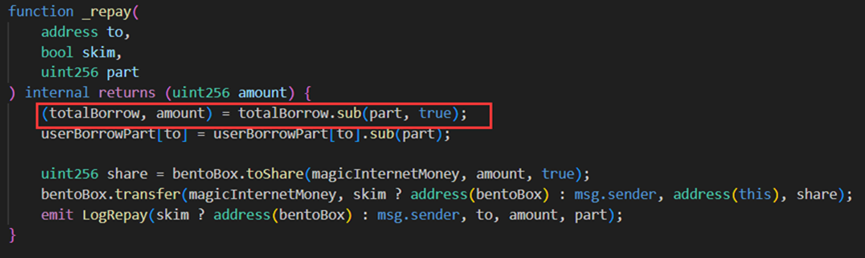
In the vulnerable contract (0x7259e1520), both the borrow and repay functions used ceiling rounding when computing the elastic and base variables.
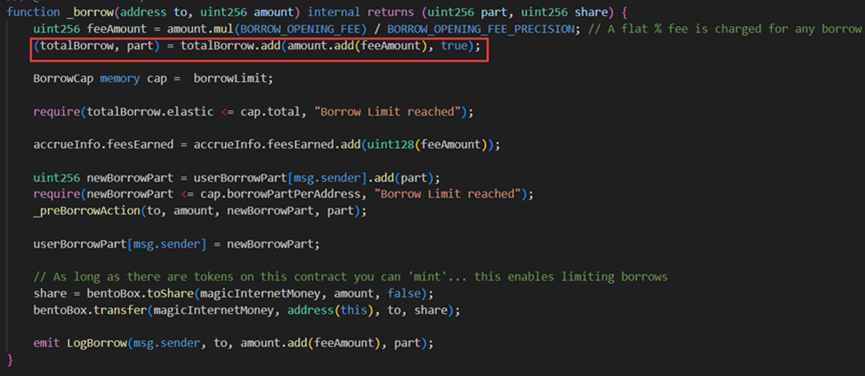
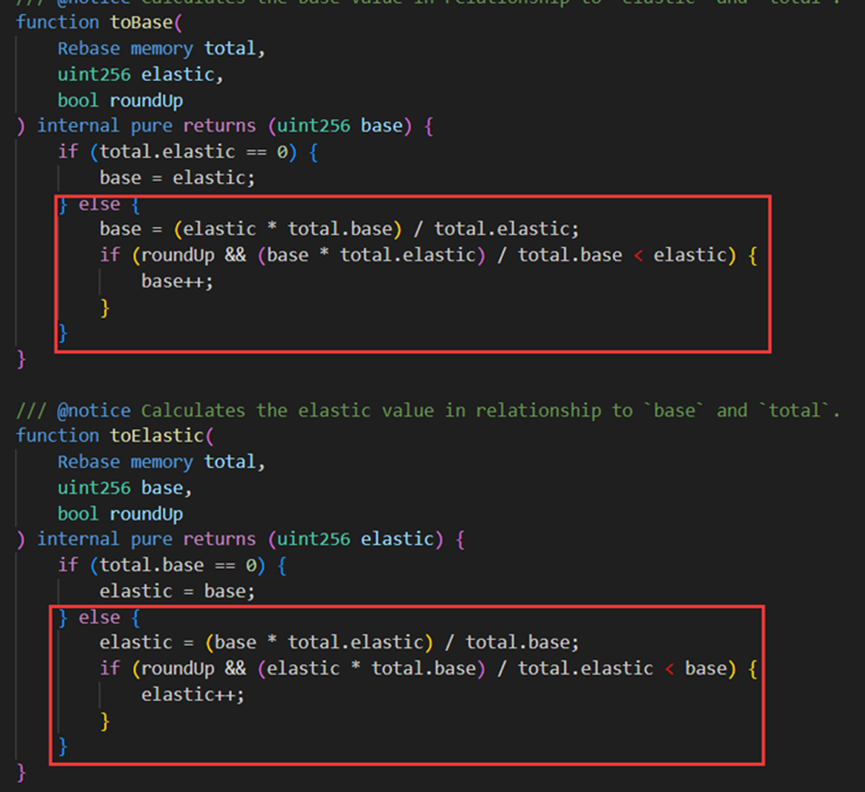
The attacker (0x87F58580) first repaid other users' loans, setting the elastic variable to 0 and the base variable to 97.
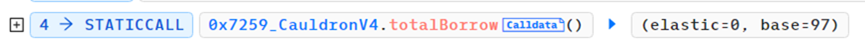
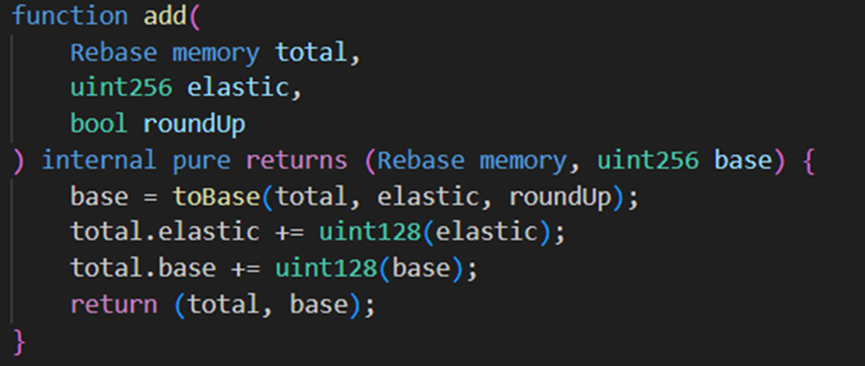
Then, repeatedly calling the borrow and repay functions with parameter amount set to 1, during the first call to borrow function, since elastic=0, the above if logic executes and returns to the add function, resulting in elastic = 1 and base = 98.
The attacker (0x87F58580) then called the borrow function again with input 1; since elastic=1, the else logic executed, returning a value of 98, so upon returning to the add function, elastic=2 and base=196.
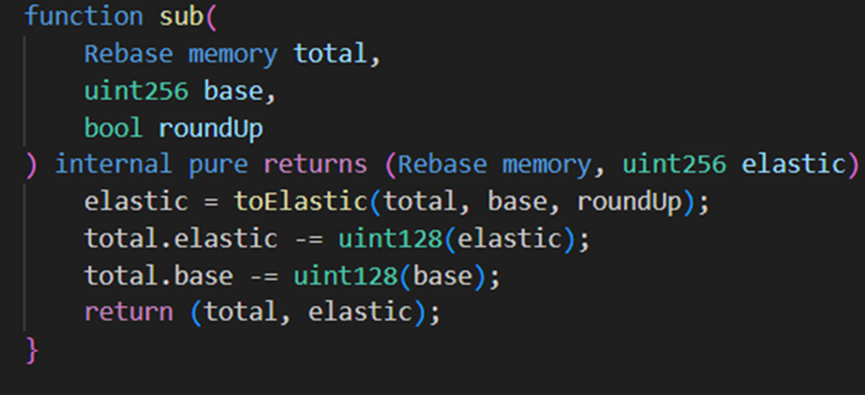
However, when the attacker (0x87F58580) called the repay function with input 1, since elastic=2, the else logic executed, calculating the new elastic value as 1*2/98 = 0, but due to the subsequent ceiling rounding step, the returned value became 1. Upon returning to the sub function, elastic reverted back to 1, while base became 195.
It can be seen that after one borrow-repay cycle, the elastic variable remains unchanged while the base variable nearly doubles. Exploiting this vulnerability, the hacker performed frequent borrow-repay cycles and finally called repay once more, ultimately achieving elastic=0 and base = 120080183810681886665215049728.
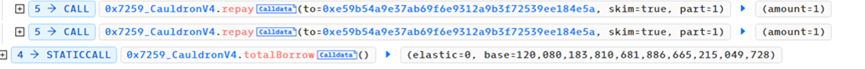
Once the ratio between elastic and base variables became severely imbalanced, the attacker (0x87F58580) could borrow large quantities of MIM tokens by depositing only minimal collateral, completing the attack.
3.2 DeGame Phishing Attack and the Pink Drainer Scam Group
In March 2024, a Web3 user unknowingly clicked a phishing link posted by a compromised official DeGame Twitter account and suffered asset loss.
Afterward, the user mistakenly believed DeGame had committed internal fraud and publicly disclosed the incident on Twitter. A number of KOLs, media outlets, and many users unknowingly amplified the story, significantly damaging DeGame's brand image and platform reputation.
Following the incident, DeGame activated its emergency response plan and assisted affected users in attempting to recover assets. The sequence of events in the DeGame phishing attack is outlined as follows:
(1) Between 4:00 AM and 9:30 AM on March 14, the official DeGame X account (@degame_l2y) posted four airdrop tweets, all containing links to fake phishing websites mimicking DeGame's official site. One user reported losing approximately 57 PufETH after clicking one of these airdrop links;
(2) After 9:30 AM, DeGame's Twitter operator discovered and removed the phishing links. Simultaneously, DeGame notified all users via official social media and community channels and issued a public warning announcement.
(3) During the period when DeGame’s official Twitter account was compromised, the victim encountered the phishing website link and instructions posted by the attacker. Unaware of the deception, the user assumed the link was part of an official token airdrop event jointly hosted by DeGame and another project, followed the attacker's prompts after clicking the link, and consequently lost their assets.
(4) After the user connected their wallet via the phishing website, the site automatically detected whether any assets were present in the wallet. If assets were found, it immediately prompted the user to sign a Permit Token Approval transaction. Unlike regular on-chain transactions, this signature is entirely off-chain and anonymous, potentially exploitable for illicit purposes. Moreover, users could interact with application contracts using an additional authorization signature (Permit) without prior approval.
(5) In this breach, the phishing hacker obtained the victim's signed Permit Token Approval transaction authorizing the phishing contract address 0xd560b5325d6669aab86f6d42e156133c534cde90, then submitted the Permit call to Approve in the attack transaction to obtain token authorization and transfer the stolen funds.
(6) The phishing tool provider was the scam group Pink Drainer. Pink Drainer operates as Malware-as-a-Service (MaaS), enabling attackers to rapidly deploy malicious websites and illegally acquire assets through this malware. In this theft, approximately 25% of the stolen funds were transferred to PinkDrainer: Wallet 2—the second numbered wallet address of the PinkDrainer phishing gang—representing an automatic revenue share paid by the perpetrator who used PinkDrainer's phishing tools.
3.3 Surge in Rugpull Incidents Due to Mass Rugpull Operations
The sharp rise in Rugpull incidents in 2024 is closely related to factory contracts creating multiple fraudulent tokens en masse. SharkTeam's security research team conducted a detailed analysis of these Rugpull incidents. During the investigation, we found that Rugpull factory contracts on BNB Chain have initiated over 70 Rugpulls in the past month. These mass Rugpull operations typically exhibit the following behavioral characteristics:
(1) These tokens are created via createToken operations executed by token factory contracts. Within the createToken function, parameters required include: token name, symbol, decimals, supply, owner address, factory contract address for pair creation, and the BUSD-T stablecoin address. The factory contract used for pair creation leverages PancakeSwap’s factory contract, and each token has a distinct owner address.
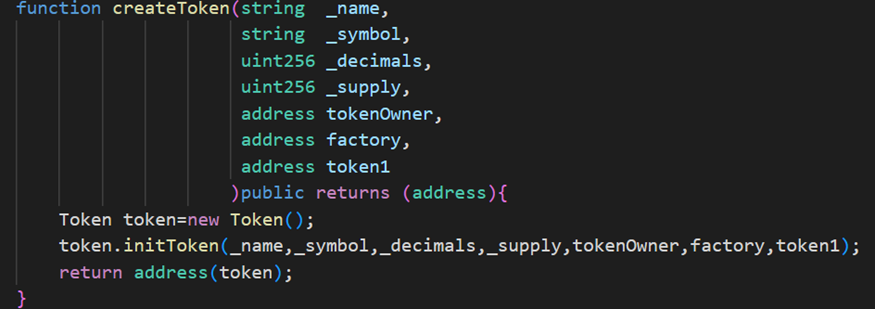
(2) Token owners use other addresses to conduct bulk buy and sell operations on Rugpull tokens. These actions significantly increase liquidity and gradually drive up token prices.
(3) Through phishing and promotional tactics, large numbers of users are enticed to purchase, further increasing liquidity and doubling token prices.
(4) When token prices reach certain thresholds, the owners execute massive sell-offs, effectively pulling the rug.
Behind these activities lies a well-organized Web3 scam syndicate forming a black industry chain involving trend exploitation, automated token deployment, automated trading, false promotion, phishing attacks, and Rugpull harvesting. The fraudulent tokens launched are tightly tied to current industry hotspots, making them highly deceptive and persuasive. Users must remain vigilant at all times and exercise rational judgment to avoid losses.
4. Conclusion
Total losses caused by security incidents in Q1 2024 reached $462 million. While rising cryptocurrency prices contributed somewhat to the increased total amount, overall, the Web3 security situation remains grim. Smart contract logic vulnerabilities, the Rugpull black industry chain, and phishing attacks continue to pose major threats to users’ digital asset security. We urge both Web3 users and project teams to enhance their security awareness promptly to minimize potential losses.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News