SharkTeam: 2023 Cryptocurrency Crime Analysis Report
TechFlow Selected TechFlow Selected

SharkTeam: 2023 Cryptocurrency Crime Analysis Report
Cyberattacks remain a primary cause of significant losses.
Authored by: SharkTeam
In 2023, the Web3 industry experienced over 940 security incidents of varying scale, representing a year-on-year increase of more than 50% compared to 2022, with total losses amounting to $1.79 billion. The third quarter saw the highest number of incidents (360 cases) and the largest financial losses ($740 million), marking a 47% increase from 2022. Particularly in July, 187 security incidents occurred, resulting in losses totaling $350 million.
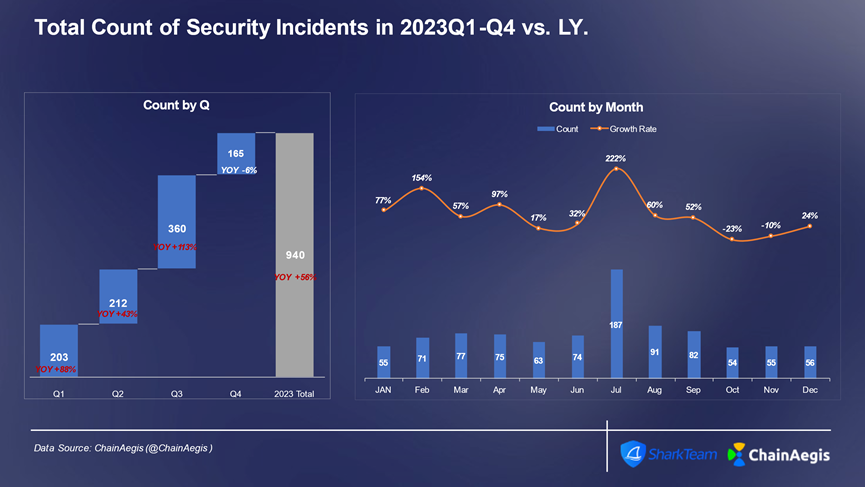
Figure: Quarterly and monthly count of Web3 security incidents in 2023
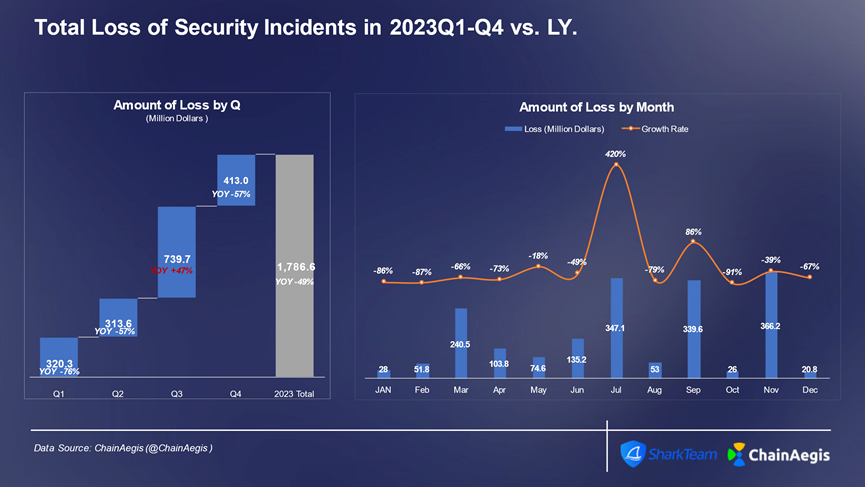
Figure: Quarterly and monthly financial losses from Web3 security incidents in 2023 (in millions of USD)
First, hacking attacks remain a primary cause of major losses. In 2023, there were 216 hacking incidents, causing $1.06 billion in damages. Smart contract vulnerabilities, private key thefts, phishing attacks, and state-sponsored hackers continue to pose significant threats to the security of the Web3 ecosystem.
Second, rug pulls and Ponzi scheme frauds have surged. In 2023, there were 250 rug pull and scam incidents, with BNBChain experiencing the highest frequency. Fraudulent projects lure investors by launching seemingly attractive crypto ventures and providing fake liquidity. Once sufficient funds are collected, perpetrators abruptly steal all assets and transfer them elsewhere. These fraudulent activities not only cause severe financial harm to investors but also significantly raise the difficulty of selecting legitimate projects.
Additionally, ransomware groups increasingly demand cryptocurrency as ransom, including Lockbit, Conti, Suncrypt, and Monti. Cryptocurrencies are harder to trace than fiat currencies, making it increasingly important to use on-chain analysis tools to track and identify ransomware operators.
Finally, after obtaining cryptocurrencies through hacking, fraud, or ransomware, criminals typically launder funds via on-chain transfers and OTC exchanges. Money laundering often combines decentralized and centralized methods, with centralized exchanges being the most concentrated venues, followed by on-chain mixing platforms.
2023 was also a year of substantial progress in Web3 regulation. Key events such as the relaunch of FTX 2.0, sanctions against Binance, Tether blocking Hamas-related addresses, and the SEC approving spot Bitcoin ETFs in January 2024 indicate that regulators are increasingly intervening in Web3's development.
This report provides a systematic analysis of critical topics in 2023, including Web3 hacks, rug pulls and scams, ransomware, cryptocurrency money laundering, and regulatory developments, aiming to understand the overall security landscape of the crypto industry.
I. Smart Contract Vulnerabilities
Smart contract exploits primarily occurred on Ethereum. In the second half of 2023, Ethereum experienced 36 such attacks, resulting in losses exceeding $200 million, followed by BNBChain. Business logic flaws and flash loan attacks remained the most common exploitation techniques.
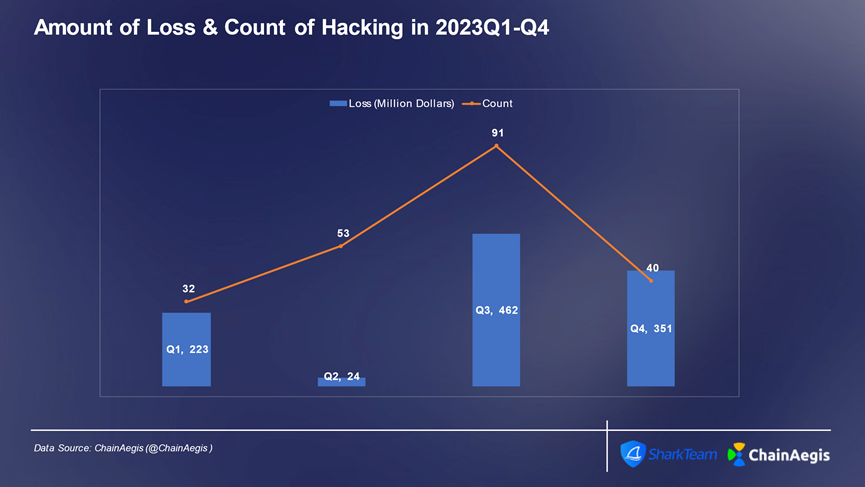
Figure: Quarterly count and financial loss of Web3 hacking incidents in 2023 (in millions of USD)
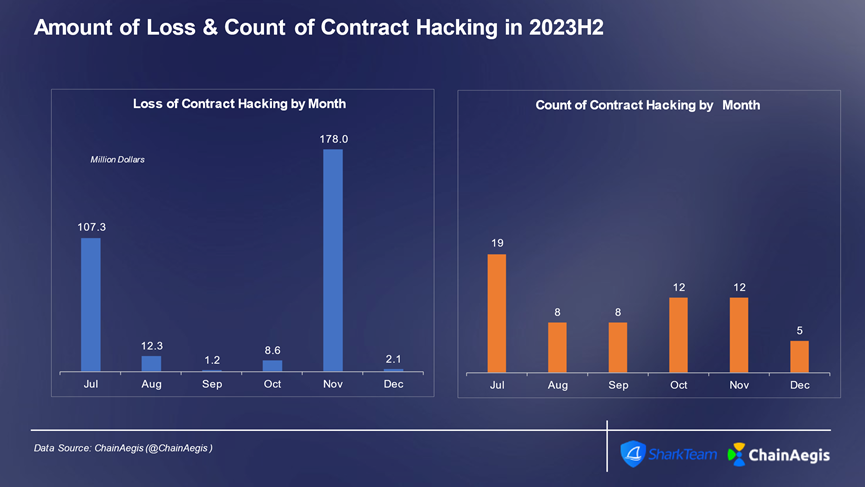
Figure: Monthly count and financial loss of smart contract exploit attacks in Web3 H2 2023
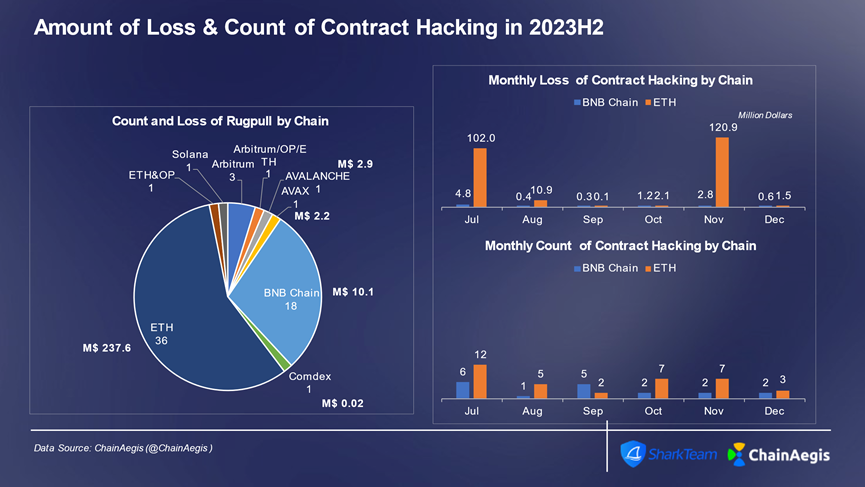
Figure: Monthly count and financial loss of smart contract exploit attacks across different chains in Web3 H2 2023
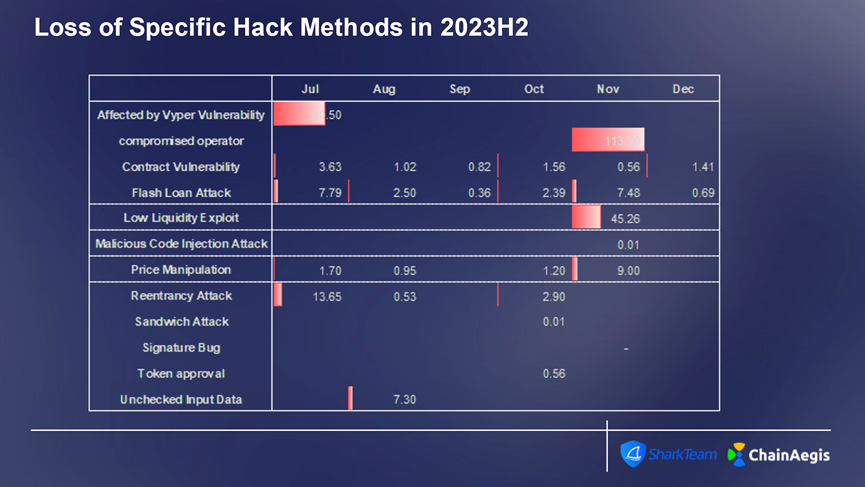
Figure: Count and financial loss of specific smart contract exploit techniques used in Web3 H2 2023
Case Study: Vyper Vulnerability Led to Attacks on Curve, JPEG'd, and Others
Take the attack on JPEG'd as an example:
Attacker address: 0x6ec21d1868743a44318c3c259a6d4953f9978538
Attacker contract: 0x9420F8821aB4609Ad9FA514f8D2F5344C3c0A6Ab
Attack transaction:
0xa84aa065ce61dbb1eb50ab6ae67fc31a9da50dd2c74eefd561661bfce2f1620c
(1) The attacker (0x6ec21d18) created contract 0x466B85B4 and borrowed 80,000 WETH via flash loan from [Balancer: Vault].
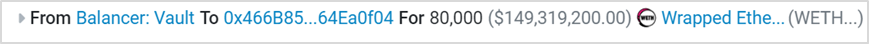
(2) The attacker (0x6ec21d18) added 40,000 WETH into the pETH-ETH-f (0x9848482d) liquidity pool, receiving 32,431 pETH.
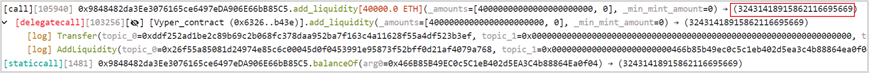
(3) Subsequently, the attacker (0x6ec21d18) repeatedly removed liquidity from the pETH-ETH-f (0x9848482d) pool.
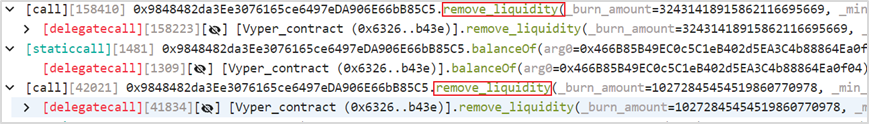
(4) Finally, the attacker (0x6ec21d18) obtained 86,106 WETH, repaid the flash loan, and exited with a profit of 6,106 WETH.
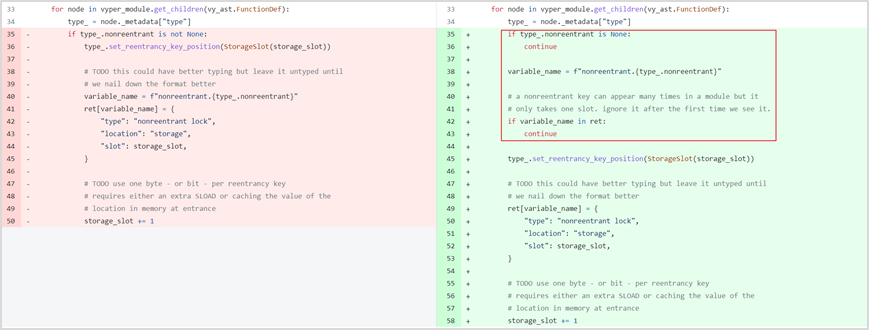
Vulnerability Analysis: This was a classic reentrancy attack. Bytecode decompilation of the compromised project’s contract reveals that the add_liquidity and remove_liquidity functions verify different storage slots. Using distinct storage slots can render reentrancy locks ineffective. This suggests a potential underlying design flaw in Vyper.
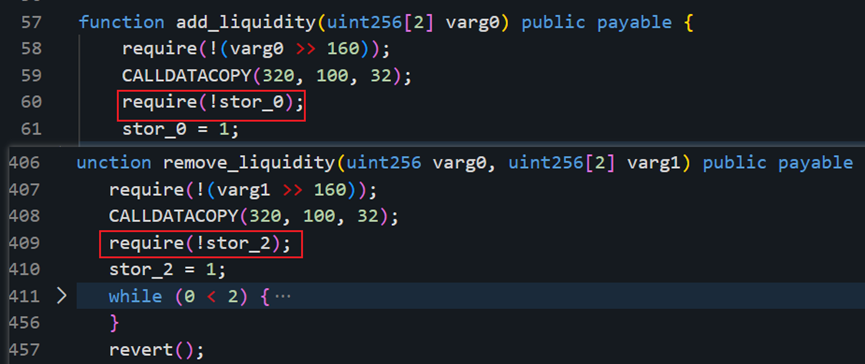
Combined with official statements from Curve, the root cause was ultimately identified as a Vyper version vulnerability present in versions 0.2.15, 0.2.16, and 0.3.0, due to flaws in the reentrancy lock mechanism. Comparing versions before 0.2.15 (like 0.2.14) and after 0.3.0 (like 0.3.1), we observe ongoing code updates, while older and newer versions do not exhibit this issue.
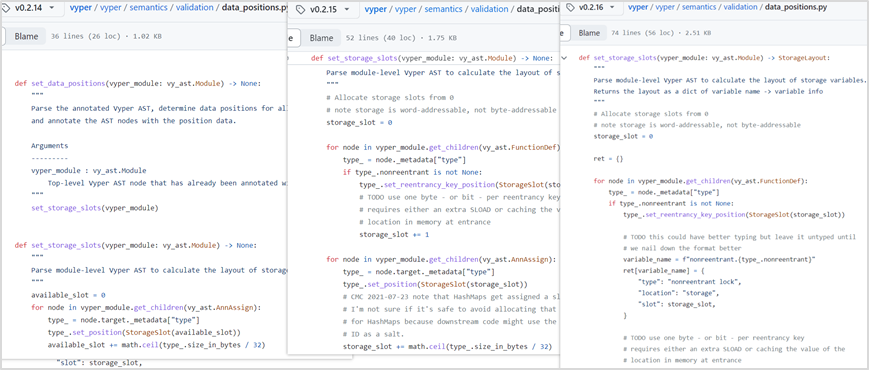
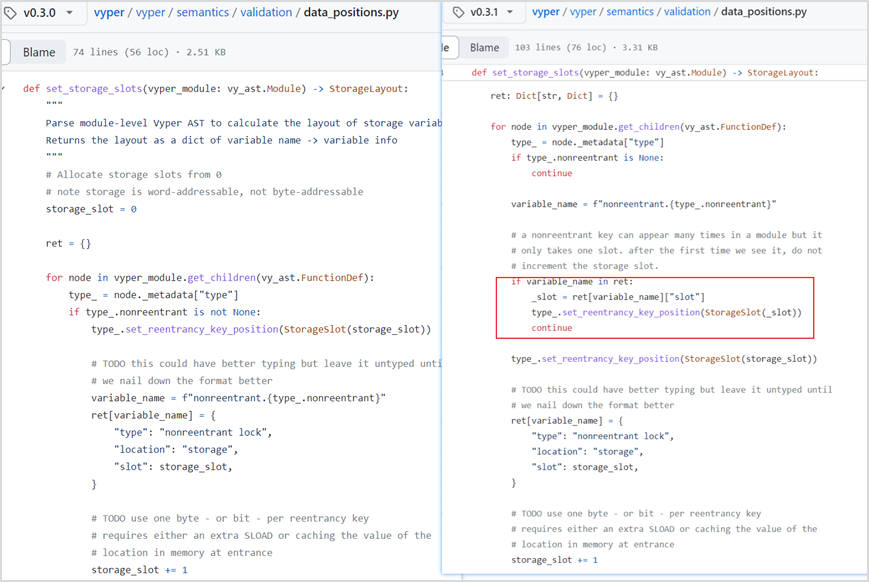
Within Vyper's relevant reentrancy lock configuration file data_positions.py, the value of storage_slot gets overwritten. In ret, the first acquired lock slot is 0; upon subsequent function calls, the lock slot increments by 1, rendering the reentrancy protection ineffective.
II. Phishing Attacks
Phishing attacks are cyberattacks designed to deceive and manipulate targets into revealing sensitive information or performing malicious actions. Typically conducted via email, social media, SMS, or other communication channels, attackers impersonate trusted entities—such as project teams, authoritative organizations, or KOLs—to trick victims into disclosing private keys, seed phrases, or signing transaction authorizations. Similar to contract exploits, phishing attacks peaked in Q3, with 107 incidents reported, including 58 in July alone.
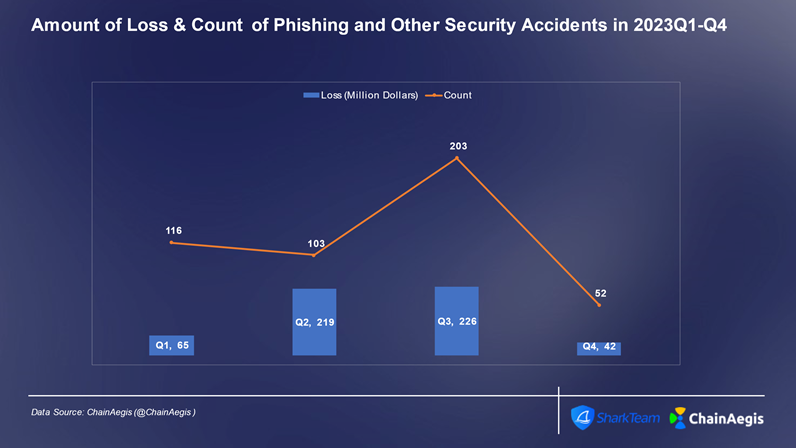
Figure: Quarterly count and financial loss of Web3 phishing attacks in 2023 (in millions of USD)
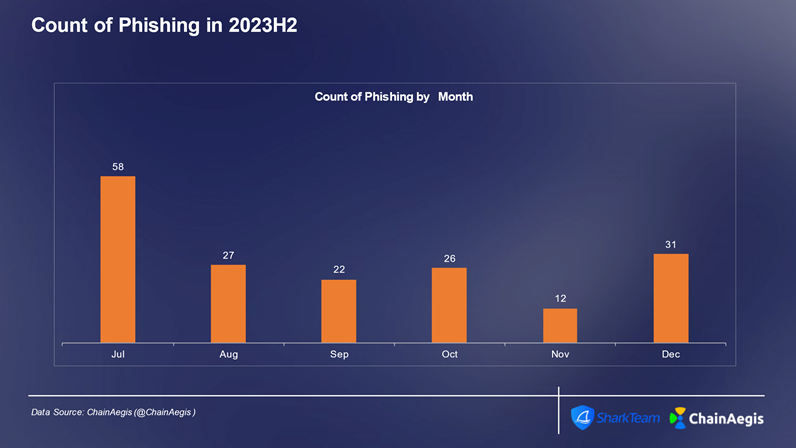
Figure: Monthly count of Web3 phishing attacks in 2023
On-Chain Asset Flow Analysis of a Typical Phishing Attack
On September 7, 2023, an address (0x13e382) fell victim to a phishing attack, suffering losses exceeding $24 million. The hacker stole funds, exchanged them, and then dispersed the proceeds. Ultimately, 3,800 ETH were gradually transferred to Tornado.Cash, 10,000 ETH sent to an intermediary address (0x702350), and 1,078,087 DAI remained in another intermediary address (0x4F2F02).
This is a typical phishing attack where attackers gain wallet authorization or private keys to steal user assets, forming a black industry chain involving phishing and money laundering. Increasingly, scam groups and even state-sponsored hackers are exploiting Web3 in this manner, demanding vigilance from users.
Based on tracking and analysis from SharkTeam’s on-chain big data platform ChainAegis (https://app.chainaegis.com/), we analyze the scam process, fund flows, and on-chain behaviors of this phishing attack.
(1) Phishing Process
The victim address (0x13e382) authorized rETH and stETH to scammer address 1 (0x4c10a4) via 'Increase Allowance'.

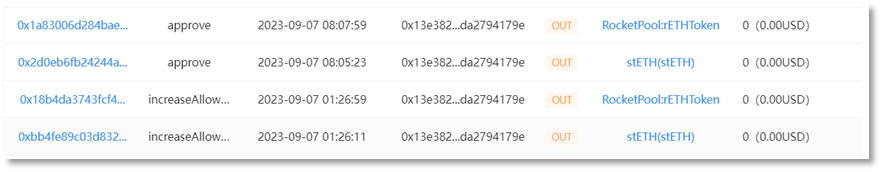
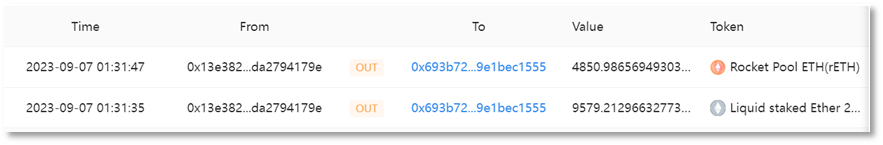
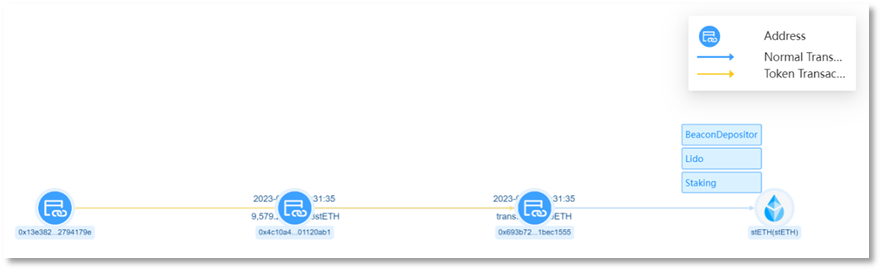
Scammer address 1 (0x4c10a4) transferred 9,579 stETH from the victim address (0x13e382) to scammer address 2 (0x693b72), worth approximately $15.32 million.
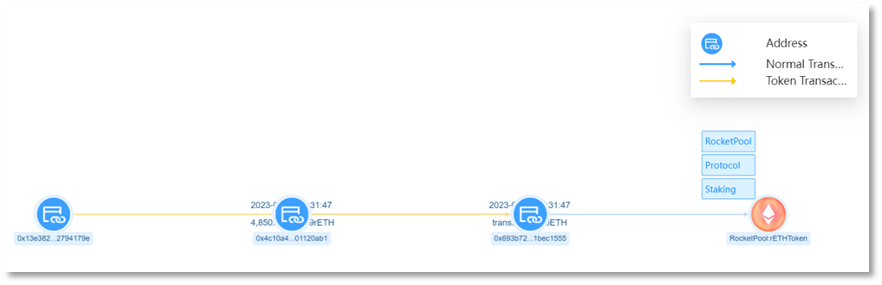
Scammer address 1 (0x4c10a4) transferred 4,850 rETH from the victim address (0x13e382) to scammer address 2 (0x693b72), worth approximately $8.41 million.
(2) Asset Exchange and Transfer
Convert stolen stETH and rETH into ETH. Starting from early morning on September 7, 2023, scammer address 2 (0x693b72) executed multiple trades across UniswapV2, UniswapV3, and Curve, converting 9,579 stETH and 4,850 rETH into a total of 14,783.9413 ETH.
stETH conversion:
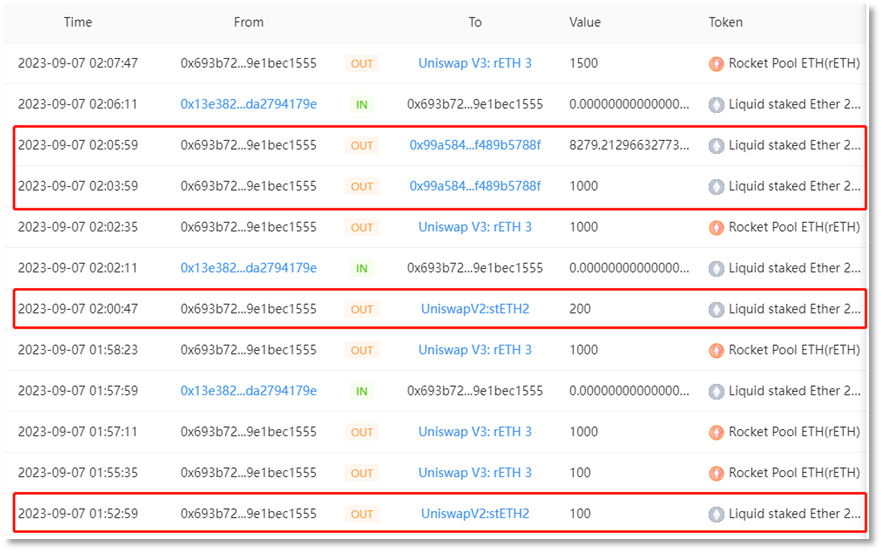
rETH conversion:

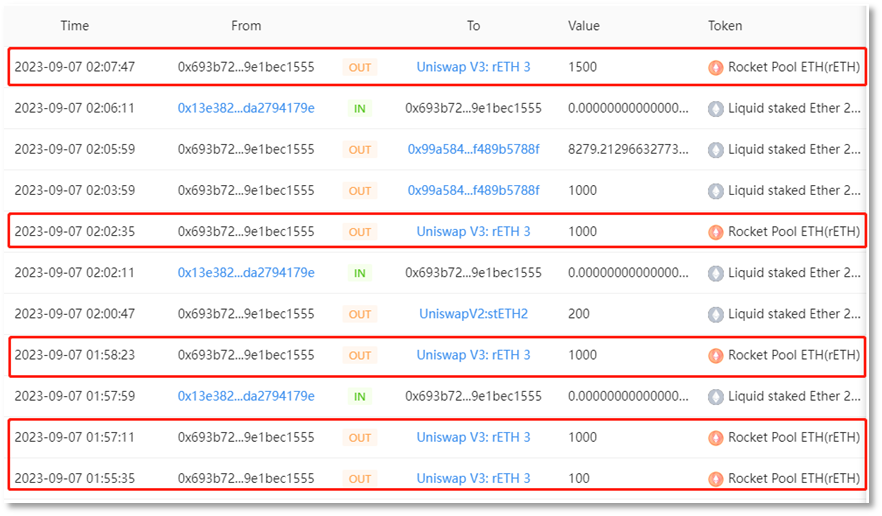
Partially convert ETH into DAI. Scammer address 2 (0x693b72) swapped 1,000 ETH for 1,635,047.761675421713685327 DAI via UniswapV3. Using distributed transfer techniques, the scammer moved stolen funds to multiple intermediary wallets, totaling 1,635,139 DAI and 13,785 ETH. Specifically, 1,785 ETH went to intermediary address (0x4F2F02), 2,000 ETH to (0x2ABdC2), and 10,000 ETH to (0x702350). Additionally, intermediary address (0x4F2F02) received 1,635,139 DAI the next day.
Intermediary wallet address (0x4F2F02) fund flow:
This address holds 1,785 ETH and 1,635,139 DAI after one layer of transfers. It disperses DAI funds and converts small amounts to ETH.
First, starting from early morning on September 7, 2023, the scammer transferred 529,000 DAI across 10 transactions. The first seven transactions totaling 452,000 DAI were sent from the intermediary address to 0x4E5B2e (FixedFloat), the eighth to 0x6cC5F6 (OKX), and the last two totaling 77,000 DAI to 0xf1dA17 (eXch).
Second, on September 10, 28,052 DAI were converted into 17.3 ETH via UniswapV2.
From September 8 to September 11, 18 transactions gradually transferred all 1,800 ETH to Tornado.Cash.
After these transfers, 1,078,087 DAI remained untransferred in this address.
Intermediary address (0x2ABdC2) fund flow:
This address holds 2,000 ETH after one layer of transfer. On September 11, it transferred 2,000 ETH to intermediary address (0x71C848).
Subsequently, intermediary address (0x71C848) conducted two rounds of fund transfers on September 11 and October 1, executing 20 transactions of 100 ETH each, totaling 2,000 ETH sent to Tornado.Cash.
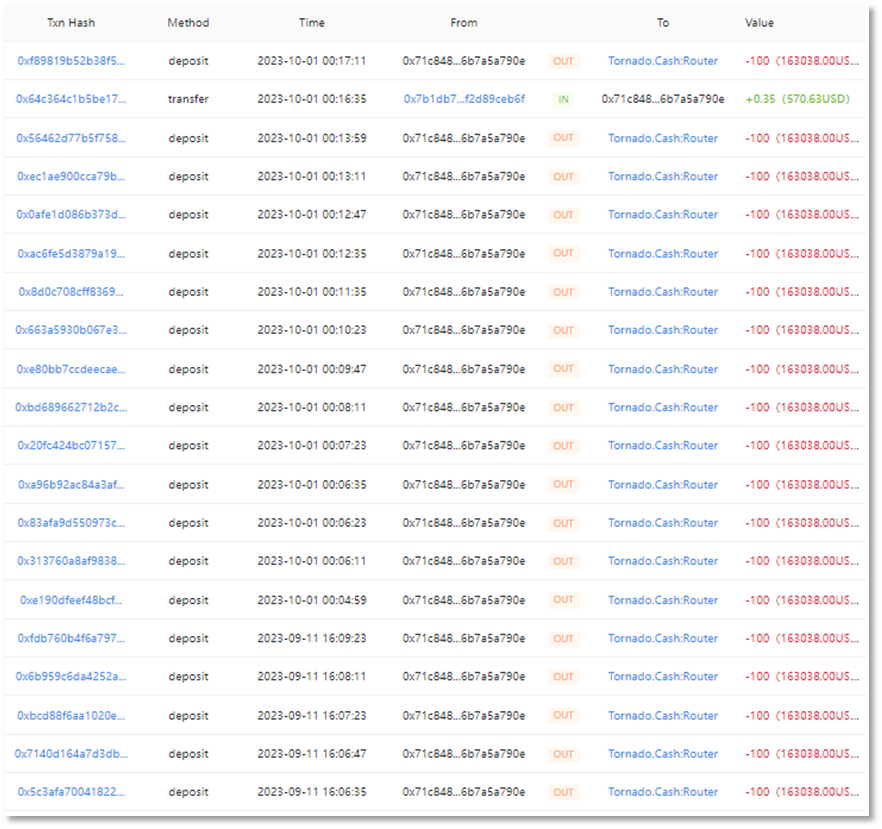
This address holds 10,000 ETH after one layer of transfer. As of October 8, 2023, the 10,000 ETH remains in this account without further movement.
Address Clue Tracking: By analyzing historical transactions of scammer address 1 (0x4c10a4) and scammer address 2 (0x693b72), we found an EOA address (0x846317) transferred 1.353 ETH to scammer address 2 (0x693b72). The funding sources of this EOA address involve hot wallet addresses of centralized exchanges KuCoin and Binance.
III. Rug Pulls and Scams
In 2023, rug pull incidents showed a significant upward trend, peaking at 73 cases in Q4 with losses totaling $19 million, averaging about $26,000 per incident. Q2 had the highest quarterly losses from rug pulls, followed by Q3, both exceeding 30% of annual total losses.
In the second half of 2023, there were 139 rug pull incidents and 12 scam cases, resulting in losses of $71.55 million and $340 million respectively.
During H2 2023, most rug pull incidents occurred on BNBChain, accounting for 91 cases (over 65%) with losses of $29.57 million (41% of total losses). Ethereum ranked second with 44 cases and $7.39 million in losses. Besides Ethereum and BNBChain, August saw the BALD rug pull on Base chain, causing severe losses of $25.6 million.
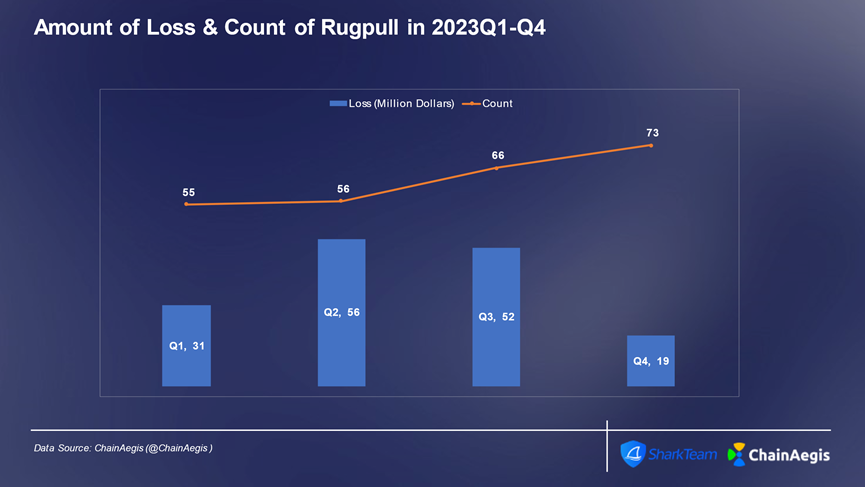
Figure: Quarterly count and financial loss of Web3 rug pull and scam incidents in 2023 (in millions of USD)
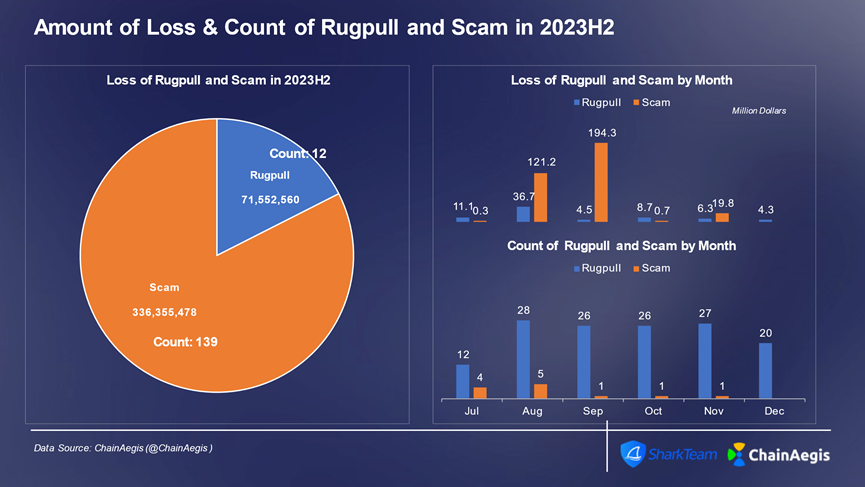
Figure: Monthly count and financial loss of Web3 rug pull and scam incidents in H2 2023
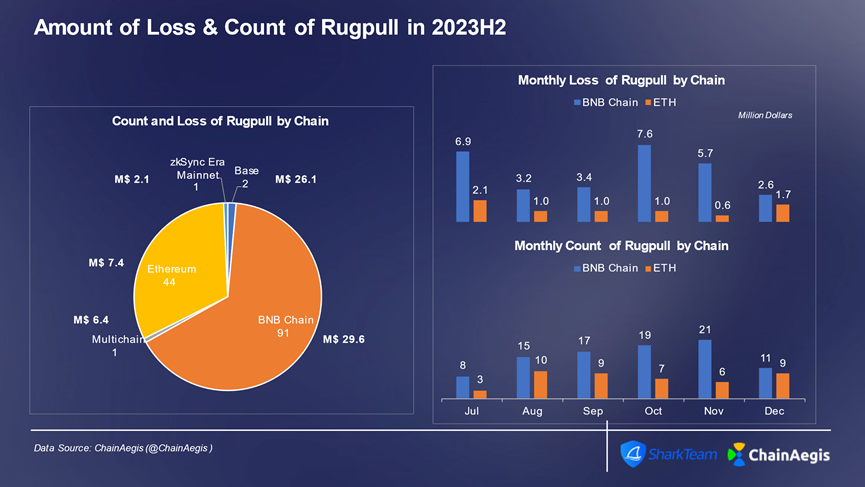
Figure: Monthly count and financial loss of Web3 rug pull incidents across different chains in H2 2023
Analysis of Rug Pull Factory Behavior
On BNBChain, a "rug pull factory" model has become popular for mass-producing fraudulent tokens. Let's examine the scam patterns behind fake SEI, X, TIP, and Blue tokens.
(1) Fake SEI
First, the fake SEI token owner 0x0a8310eca430beb13a8d1b42a03b3521326e4a58 exchanged 1 USDT for 249 fake SEI tokens.
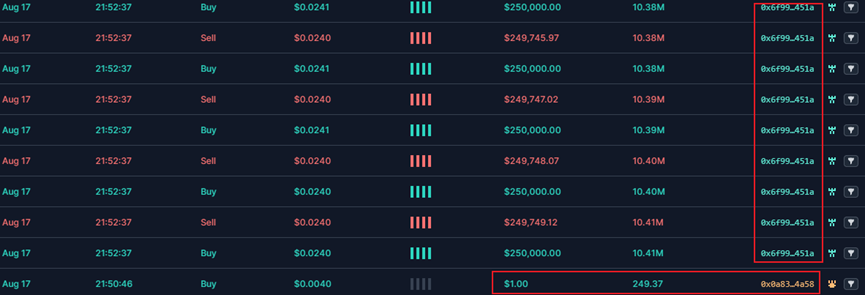
Then, 0x6f9963448071b88FB23Fd9971d24A87e5244451A performed bulk buy and sell operations, significantly increasing liquidity and driving up the token price.
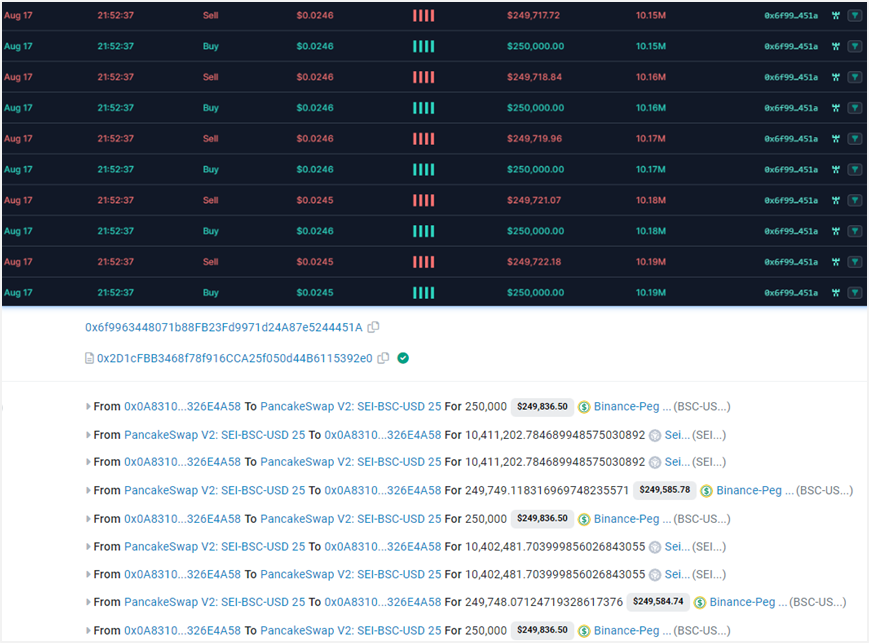
Through phishing and other promotional tactics, many users were lured into buying, further increasing liquidity and doubling the token price.
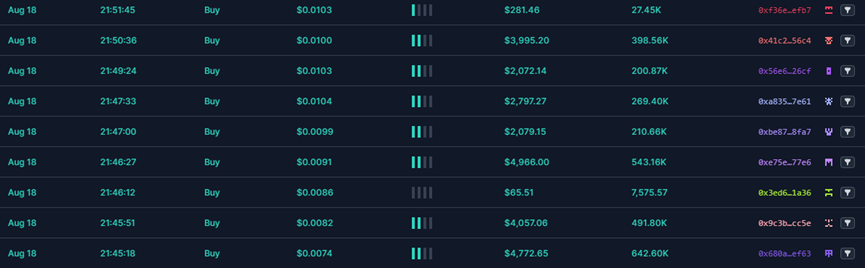
When the token price reached a certain level, the owner executed sell orders to execute the rug pull. As shown below, the timing and prices of harvesting varied.
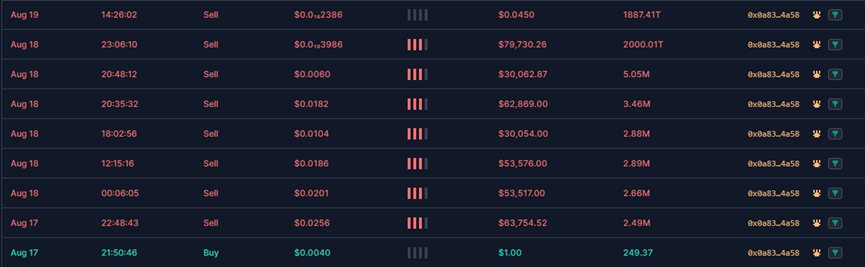
(2) Fake X, Fake TIP, Fake Blue
Similarly, the token owner 0x44A028Dae3680697795A8d50960c8C155cBc0D74 for X, TIP, and Blue exchanged 1 USDT for their respective tokens.
Then, like the fake Sei token, 0x6f9963448071b88FB23Fd9971d24A87e5244451A performed bulk buy and sell operations, significantly increasing liquidity and driving up the price.
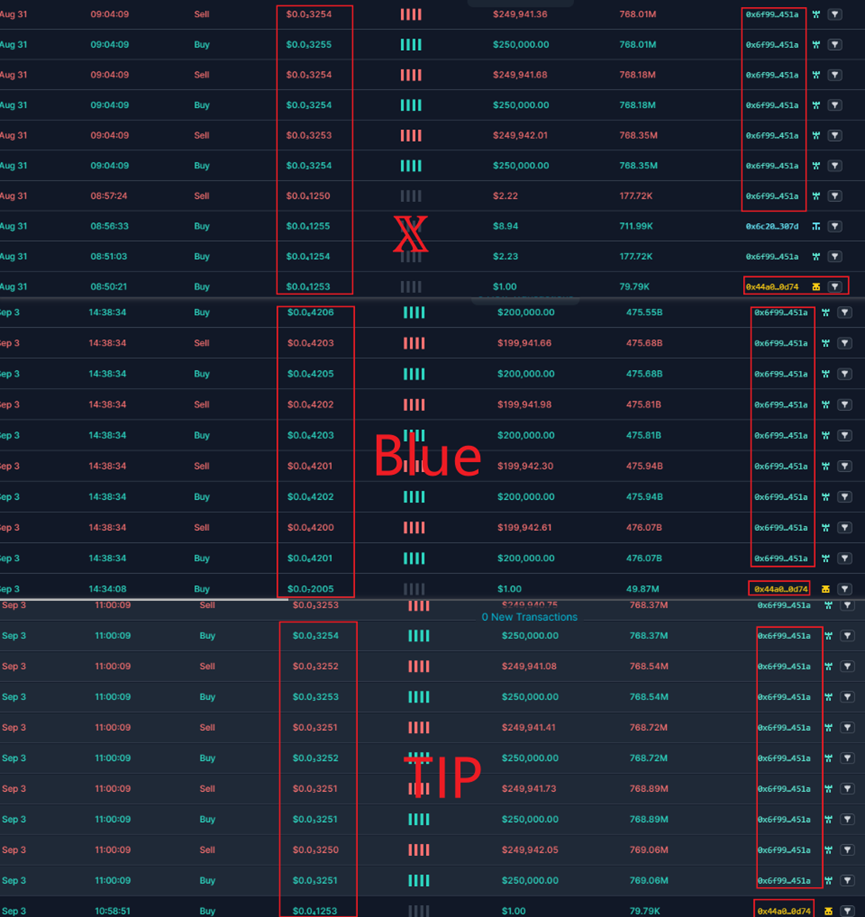
Then, through phishing and other promotion methods, large numbers of users were enticed to buy, further increasing liquidity and doubling the token price.
Like the fake SEI case, when the token price reached a certain threshold, the owner sold off holdings to complete the rug pull. As shown below, the timing and prices of harvesting varied.
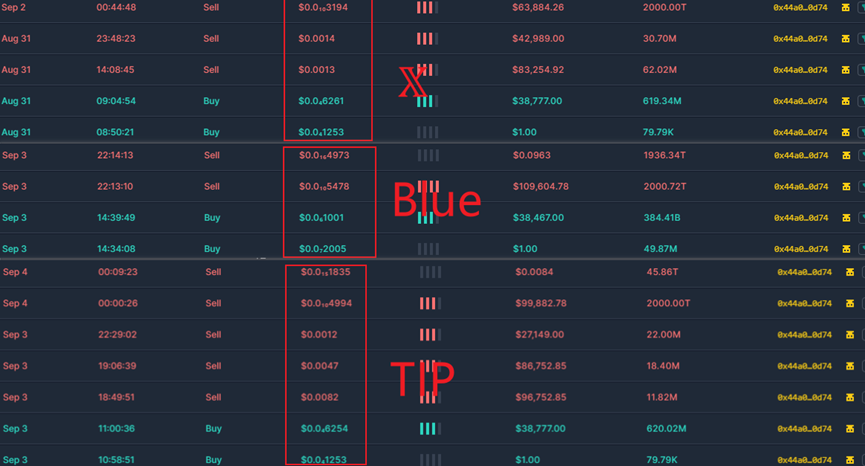
Below are the price fluctuation charts for fake SEI, fake X, fake TIP, and fake Blue tokens:
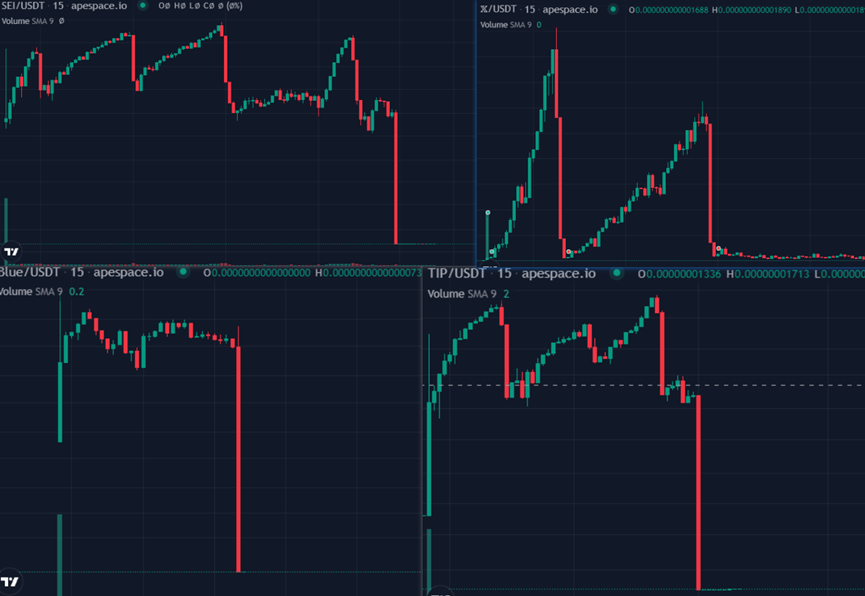
From fund tracing and behavioral pattern analysis, we observe:
In fund溯源, creators of token factories and tokens receive funds from multiple EOA accounts. These accounts transact among themselves—some through phishing addresses, others from prior rug pull profits, and some via mixers like Tornado Cash—forming complex and intertwined financial networks. Different addresses have created multiple token factory contracts and produced numerous tokens.
Analyzing rug pull behaviors, we identified address
0x6f9963448071b88FB23Fd9971d24A87e5244451A as one funding source, using batch operations to manipulate token prices. Address 0x072e9A13791f3a45fc6eB6AD38e6ea258C080cc3 also acted as a funder, providing capital to multiple token holders.
Analysis reveals a well-organized Web3 scam syndicate operating a black industry chain involving trend monitoring, automated token issuance, automated trading, false promotion, phishing, and rug pull harvesting—mostly active on BNBChain. These fraudulent tokens closely mimic trending industry narratives, making them highly deceptive and persuasive. Users must remain vigilant and rational to avoid unnecessary losses.
IV. Ransomware
In 2023, ransomware attacks continued to threaten institutions and enterprises globally. These attacks have grown increasingly sophisticated, leveraging various techniques to exploit vulnerabilities in organizational systems and networks. Proliferating ransomware poses significant risks to global businesses, individuals, and critical infrastructure. Attackers continuously refine their strategies, utilizing leaked source code, intelligent attack frameworks, and emerging programming languages to maximize illicit gains.
LockBit, ALPHV/BlackCat, and BlackBasta are currently the most active ransomware groups.
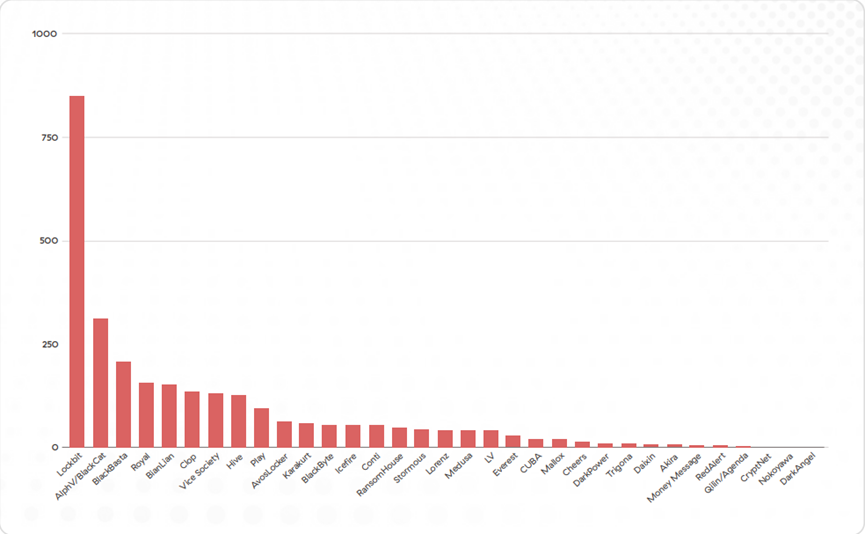
Figure: Number of victims by ransomware groups
Nowadays, more ransomware groups collect ransoms via cryptocurrency. For instance, LockBit recently attacked several high-profile organizations—including TSMC at the end of June, Boeing in October, and ICBC’s U.S. subsidiary in November—mostly demanding Bitcoin payments. After receiving ransoms, LockBit engages in cryptocurrency money laundering. Below, we analyze LockBit’s money laundering model as a representative example.
According to ChainAegis analysis, LockBit predominantly uses BTC to collect ransoms, employing different receiving addresses. Some addresses and corresponding amounts are listed below, with individual ransom demands ranging from 0.07 BTC to 5.8 BTC (approximately $2,551 to $211,311).
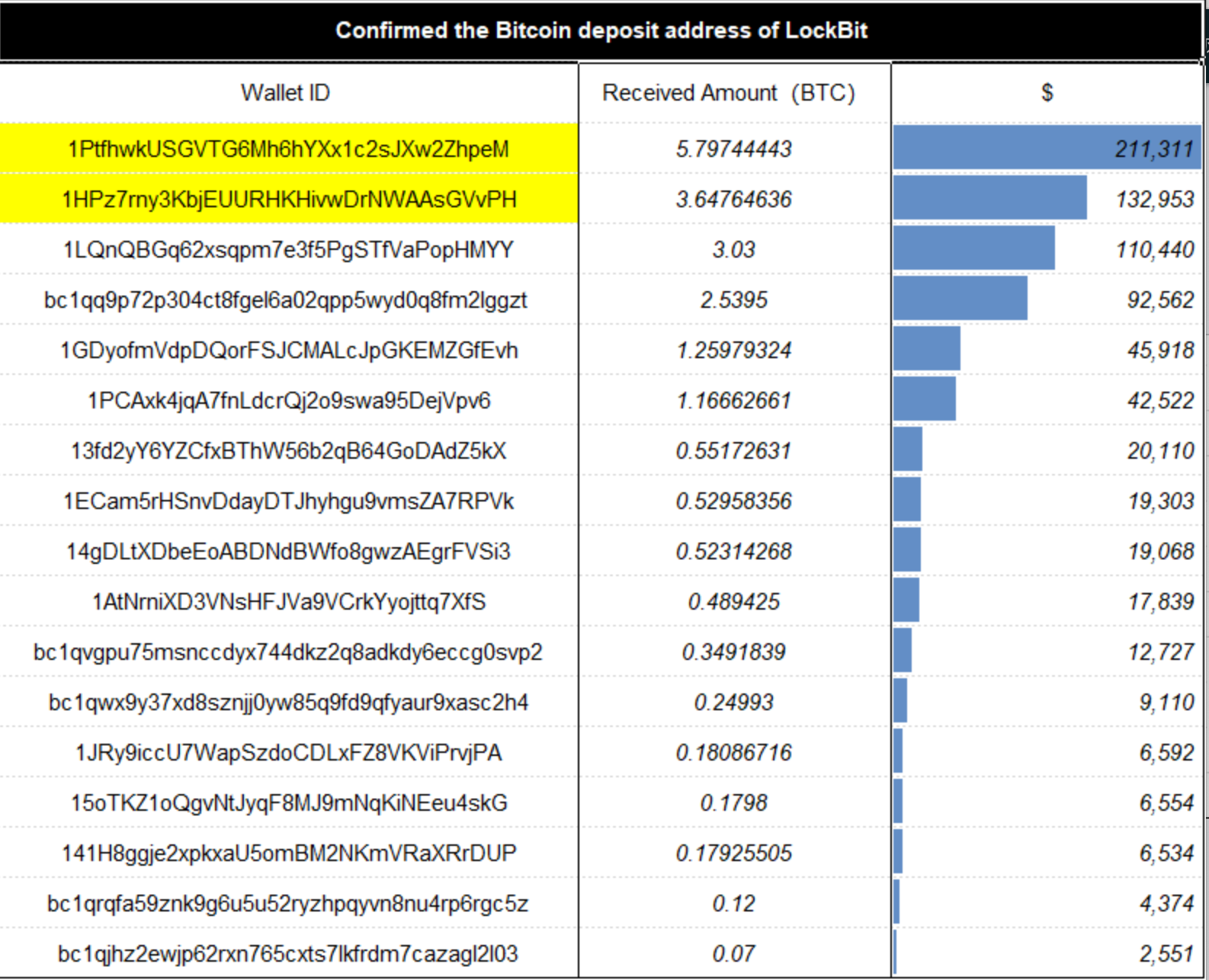
Figure: Selected LockBit ransom collection addresses and amounts
We conduct on-chain address tracking and anti-money laundering analysis for the two addresses with the highest ransom amounts:
Ransom collection address 1: 1PtfhwkUSGVTG6Mh6hYXx1c2sJXw2ZhpeM;
Ransom collection address 2: 1HPz7rny3KbjEUURHKHivwDrNWAAsGVvPH.
(1) Ransom Collection Address 1: 1PtfhwkUSGVTG6Mh6hYXx1c2sJXw2ZhpeM
As shown below, address 1 (1Ptfhw) received 17 on-chain transactions between March 25, 2021, and May 15, 2021. After receiving funds, assets were quickly transferred to 13 core intermediary addresses. These intermediaries further relayed funds to six secondary intermediaries: 3FVzPX…cUvH, 1GVKmU…Bbs1, bc1qdse…ylky, 1GUcCi…vSGb, bc1qan…0ac4, and 13CPvF…Lpdp.
Intermediate address 3FVzPX…cUvH eventually flowed into darknet address 361AkMKNNWYwZRsCE8pPNmoh5aQf4V7g4p.
Intermediate address 13CPvF…Lpdp made 500 micro-transactions of 0.00022 BTC each to CoinPayments, aggregating 0.21 BTC into CoinPayments address bc1q3y…7y88, effectively laundering funds through CoinPayments.
Other intermediate addresses ultimately flowed into centralized exchanges Binance and Bitfinex.
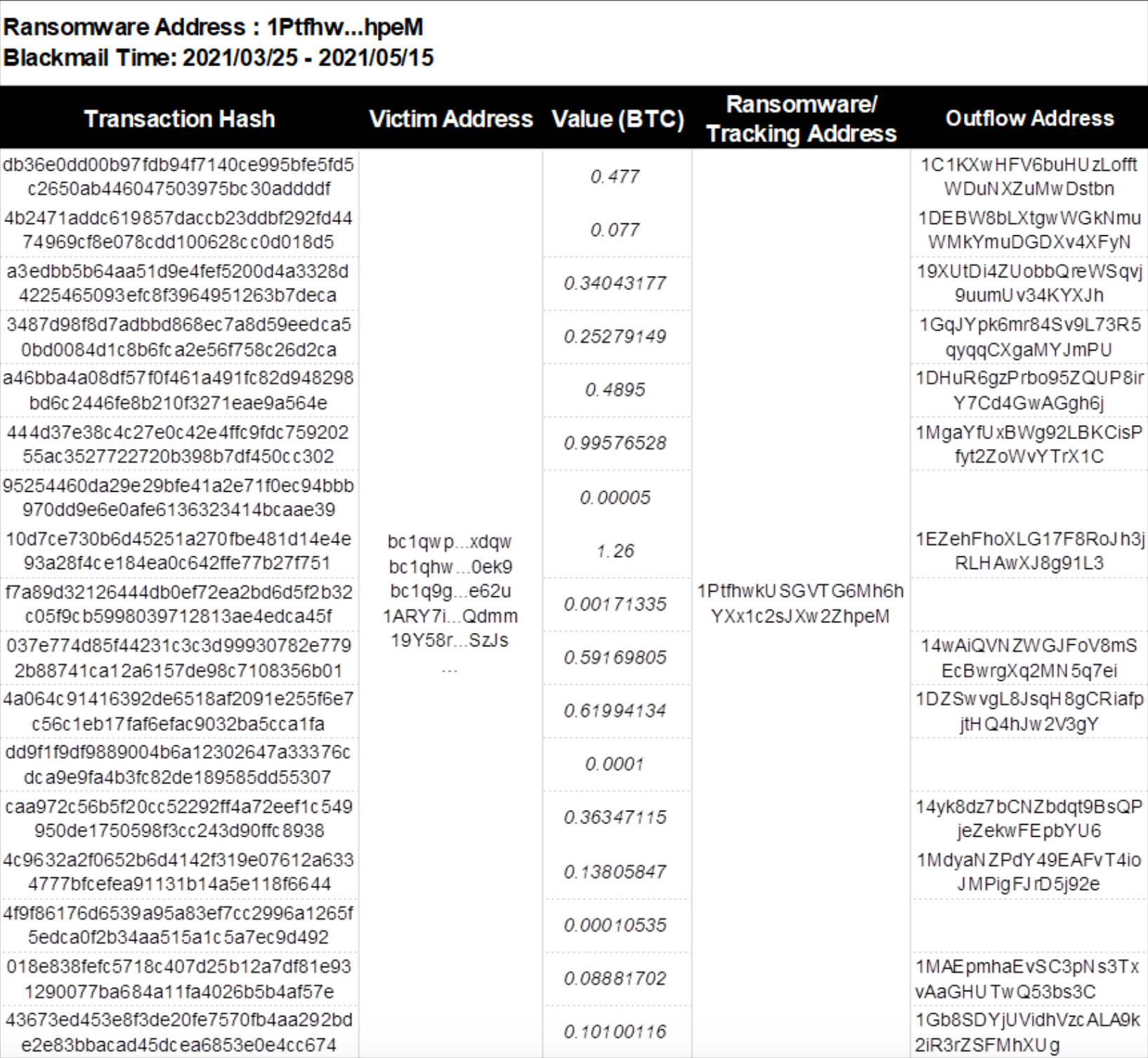
Figure: Fund inflows and outflows for address 1 (1Ptfhw…hpeM)
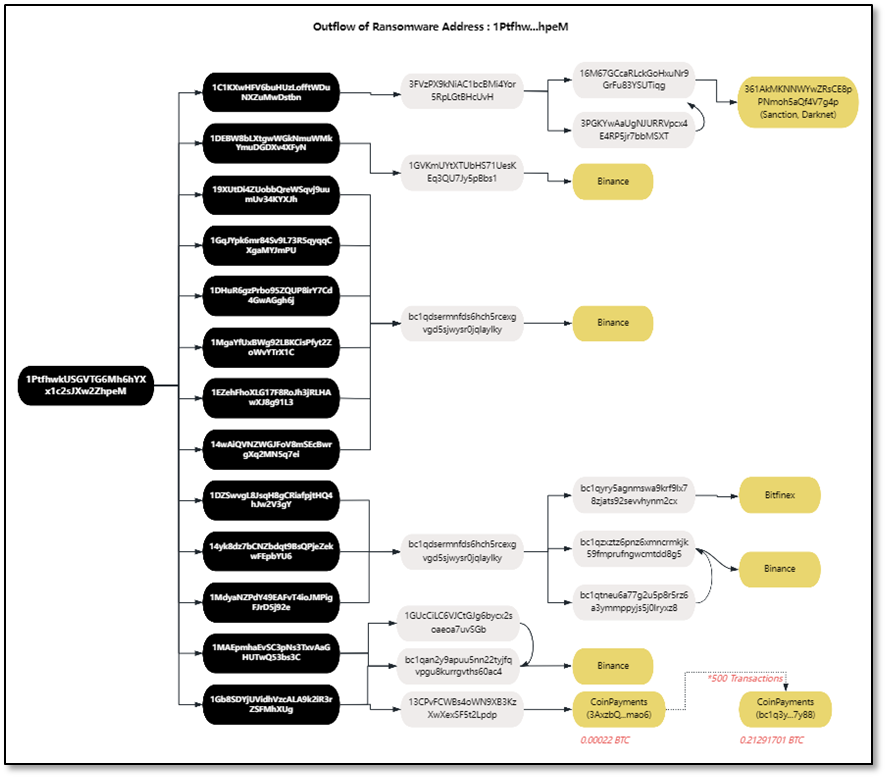
Figure: Fund flow tracking for address 1 (1Ptfhw…hpeM)
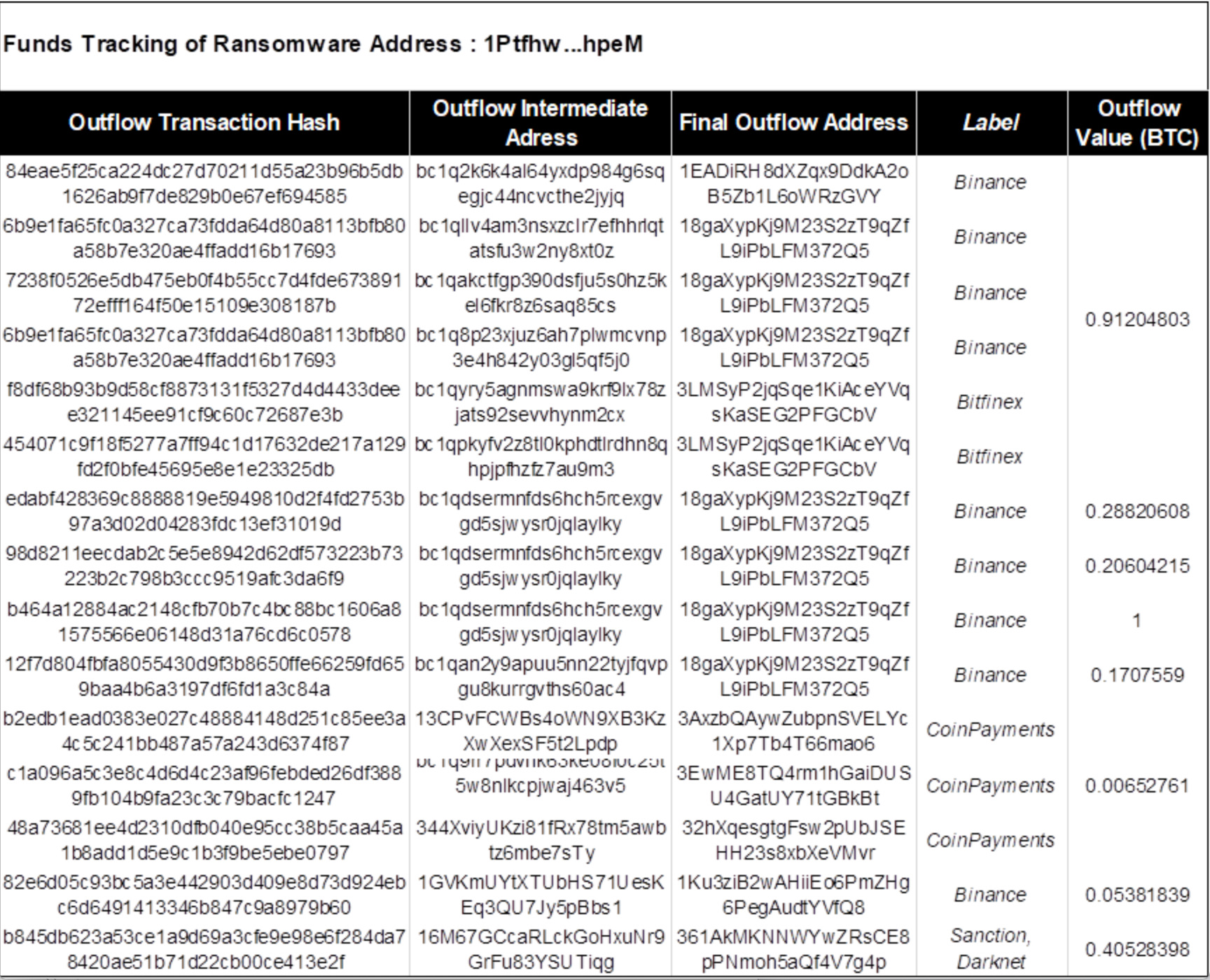
Figure: Intermediate addresses and detailed fund flows associated with address 1 (1Ptfhw…hpeM)

Figure: Transaction graph of address 1 (1Ptfhw…hpeM)
(2) Ransom Collection Address 2: 1HPz7rny3KbjEUURHKHivwDrNWAAsGVvPH
Between May 24 and May 28, 2021, victims paid 4.16 BTC to LockBit operators via 11 transactions. Immediately, address 2 (1HPz7rn...VvPH) rapidly transferred 1.89 BTC to intermediate address 1: bc1qan…0ac4, 1.84 BTC to intermediate address 2: 112QJQj…Sdha, and 0.34 BTC to intermediate address 3: 19Uxbt…9RdF.
Eventually, intermediate addresses 2 and 3 transferred all funds to intermediate address 1: bc1qan…0ac4. Then, bc1qan…0ac4 continued transferring funds—part directly to Binance, and part through layered intermediaries ultimately reaching Binance and other platforms for laundering.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News