ZKP + Bitcoin: What Empowerments Will It Bring to the Bitcoin Network?
TechFlow Selected TechFlow Selected

ZKP + Bitcoin: What Empowerments Will It Bring to the Bitcoin Network?
Bitcoin has a natural affinity for integration with zero-knowledge proofs.
Author: Kyle Liu, Investment Manager at Bing Ventures
Key Takeaways
-
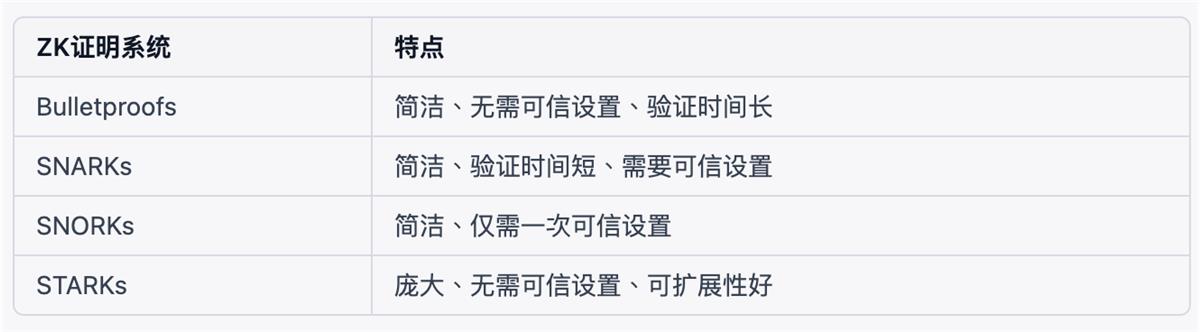
Zero-knowledge proofs (ZKPs) can enhance Bitcoin's privacy by concealing transaction details such as amounts, addresses, inputs, and outputs, while preserving transaction validity and integrity. This prevents third parties from tracking or analyzing user transaction activities.
-
ZKPs can improve Bitcoin’s scalability by reducing the size of transaction data and verification time. For example, using ZK-STARKs or their improved versions allows bundling multiple transactions together and verifying them via zero-knowledge proofs, thereby saving space and time.
-
ZKPs can boost Bitcoin’s innovation by enabling more functionalities and applications. For instance, leveraging ZK-SNARKs enables complex logic and computations to be executed without exposing information or increasing overhead, allowing for more sophisticated and flexible smart contracts.
-
Ultimately, zero-knowledge proofs will make Bitcoin more trustless and decentralized, aligning with its core values. As the technology continues to evolve and improve, the potential of Bitcoin combined with ZKPs will be increasingly unlocked.
An increasing number of teams are adopting zero-knowledge proof (ZKP) technology in blockchain infrastructure and dApps. However, most projects are built on Ethereum. In reality, Bitcoin and zero-knowledge proofs have a natural compatibility, yet this area currently lacks sufficient attention. How could integrating ZKP technology empower the Bitcoin network? In this research article from Bing Ventures, we explore this topic from both technical principles and application prospects.
Zero-knowledge proof (ZKP) is a mathematical method that allows one party (the prover) to prove a statement to another party (the verifier) without revealing any additional information about the statement itself. This method is highly effective for protecting privacy, as the prover can provide evidence to the verifier without disclosing any underlying data.
Bitcoin has a natural affinity with zero-knowledge proofs. Bitcoin is a decentralized digital currency that uses blockchain to record transactions, with all transaction data being publicly accessible. However, this also means anyone can view Bitcoin transaction records, posing risks of privacy leakage. Zero-knowledge proofs can address this issue.
By utilizing zero-knowledge proofs, Bitcoin users can encrypt transaction data and prove its validity without revealing any information, achieving a higher level of privacy protection. Additionally, zero-knowledge proofs can enhance Bitcoin’s scalability. Currently, Bitcoin’s transaction speed is limited by blockchain size and network congestion, restricting its use in large-scale commercial applications. With zero-knowledge proofs, users can batch process large volumes of transactions and compress the size of their proofs significantly, improving Bitcoin’s scalability and efficiency.
Source: Bing Ventures
Background and Fundamental Principles
ZK-SNARKs and ZK-STARKs
Both ZK-SNARKs and ZK-STARKs are variants of zero-knowledge proofs, sharing the common goal of proving the validity of certain data or operations without revealing sensitive information. However, they differ in implementation, performance, and application scope.
ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) is a zero-knowledge proof technique based on elliptic curve cryptography. It transforms complex computational problems into succinct proofs that are extremely small in size and non-interactive. This means ZK-SNARKs can verify computation correctness without revealing any details of the computation. Primary applications of ZK-SNARKs include cryptocurrencies and privacy protection.
ZK-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge) is a newer type of zero-knowledge proof technology, offering greater flexibility and security compared to ZK-SNARKs. Unlike ZK-SNARKs, ZK-STARKs do not rely on elliptic curve cryptography but instead use hash functions and polynomial interpolation techniques. This makes ZK-STARKs more reliable, as they depend on the irreversibility of hash functions rather than unpredictable mathematical assumptions. Although ZK-STARKs produce larger proofs than ZK-SNARKs, they offer better verifiability and thus can be applied in broader domains such as distributed computing and IoT security.

Source: Matter Labs
Challenges of Integrating Zero-Knowledge Proofs into Bitcoin
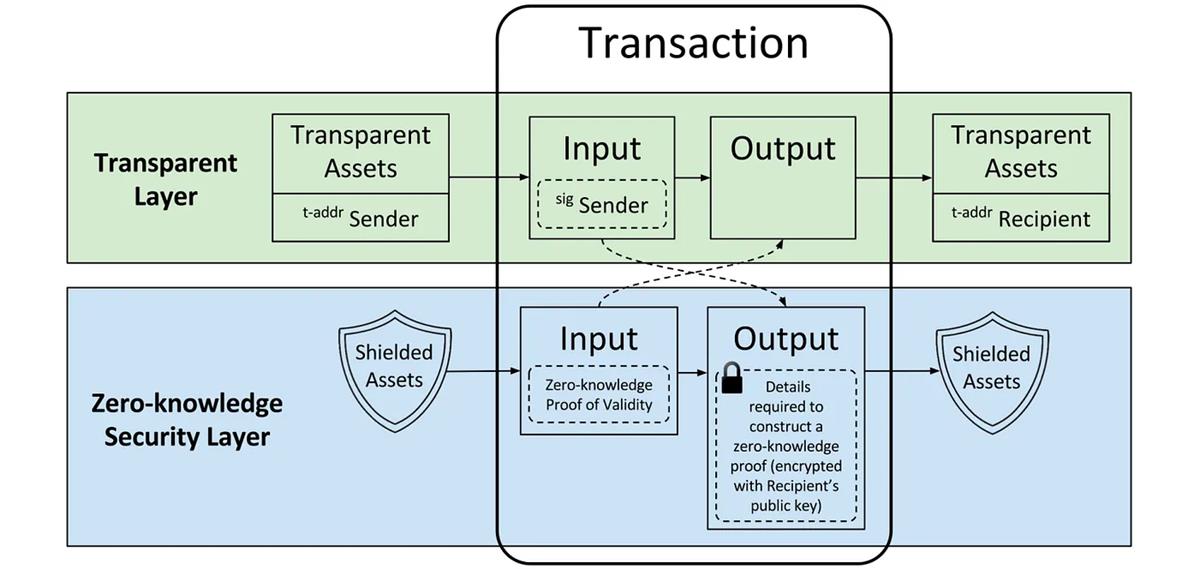
Taking Zcash as an example, it employs ZK-SNARKs—a zero-knowledge proof technology—to hide detailed transaction information such as transaction amounts and participant identities, achieving stronger privacy protection. The technical framework of Zcash’s use of ZK-SNARKs works roughly as follows:
-
Zcash has two types of addresses: transparent addresses (t-addresses) and shielded addresses (z-addresses). Transparent addresses function similarly to Bitcoin addresses, where transaction amounts and participants are publicly visible on the blockchain. Shielded addresses, however, use zero-knowledge proofs to protect transaction amount and participant privacy.
-
When a user sends funds from one shielded address to another, they must generate a ZK-SNARKs proof demonstrating they hold sufficient funds and have not double-spent. This process involves complex mathematical and cryptographic operations such as generating public parameters, computing hashes, and constructing arithmetic circuits.
-
Generating ZK-SNARKs proofs requires substantial computational resources and time, but verifying them is fast and simple. Verifiers only need to confirm that transactions comply with blockchain rules, without accessing any information about transaction amounts or participants.
-
By employing ZK-SNARKs, Zcash achieves fully anonymous yet verifiable transactions, enhancing user privacy and usability while maintaining blockchain security and decentralization.
However, Zcash’s zero-knowledge proof technology has limitations. First, Zcash is UTXO-based, meaning transaction data isn’t fully hidden—only obscured. Attackers may still infer useful information by analyzing transaction patterns and flows, making Zcash’s privacy protection less than fully reliable.
Second, Zcash operates on an independent network based on Bitcoin, making integration with other applications difficult. This limits its broader applicability and hinders development. While Zcash enables private transactions, actual adoption remains low. One reason is that private transactions incur significantly higher costs than public ones, further constraining practical usage.
Source: Ashish
Technical Advantages of ZK-STARKs
While implementing ZK-SNARKs on Bitcoin can achieve transaction anonymity and privacy protection, the technology comes with drawbacks such as requiring trusted setup and significant computational and storage resources. To address these issues, newer zero-knowledge proof technologies like ZK-STARKs have emerged.
In simple terms, the ZK-STARKs process includes the following steps:
-
The prover converts the computation they wish to prove into a system of polynomial equations, using secret information as variables.
-
The prover performs a series of transformations and simplifications on this equation system to obtain a simpler version.
-
The prover samples and encodes the simplified equation system to generate a low-dimensional vector.
-
The prover applies hashing and signing to this vector, producing a short string as the proof.
-
Upon receiving the string, the verifier can check its correctness using public parameters and algorithms, without knowing the secret information or original computation.
Source: Bing Ventures
Compared to ZK-SNARKs, ZK-STARKs offer the following advantages:
-
ZK-STARKs do not require a trusted setup, eliminating reliance on a specific generator and enhancing security.
-
ZK-STARKs require fewer computational and storage resources, making them better suited for lightweight devices and broader application scenarios. Their proof generation process is more efficient than ZK-SNARKs, which involve complex encryption and decryption operations. Moreover, ZK-STARKs can better leverage parallel and distributed computing capabilities, enabling more efficient processing of computational tasks in certain cases.
-
ZK-STARKs support a wider range of algorithms and operations, such as hash functions and polynomial computations, providing greater potential for technological expansion and upgrades.
Source: Vitalik
Integrating Bitcoin with ZK-STARKs
EC-STARKs Technology
STARKs technology is a new cryptographic proof method that enables secure communication with third parties while preserving data privacy. It shifts the burden of computing and storing verification data off-chain, enhancing scalability. Compared to ZK-SNARKs, STARKs are more advanced and resistant to quantum computer attacks.
EC-STARKs is the next-generation evolution of STARKs, aiming to improve Bitcoin’s scalability and security by replacing hash functions with elliptic curves. This technology enables Ethereum-based scalability solutions to become compatible with Bitcoin. Using EC-STARKs, Bitcoin protocols can run off-chain, with proofs stored within STARKs.
In essence, Bitcoin can be simulated within STARKs, allowing highly complex protocols based on Bitcoin tokens to be built using the same elliptic curve keys. EC-STARKs operate within Bitcoin’s off-chain protocols while keeping proofs anchored in STARKs. This approach not only improves Bitcoin’s scalability but also enables the construction of highly intricate protocols on Bitcoin, enhancing privacy.
This technology elevates Bitcoin’s scalability and privacy to a new level, transforming it into a superior platform. Developers can build more sophisticated applications on Bitcoin, solidifying its position in the cryptocurrency market.

Source: Starkware
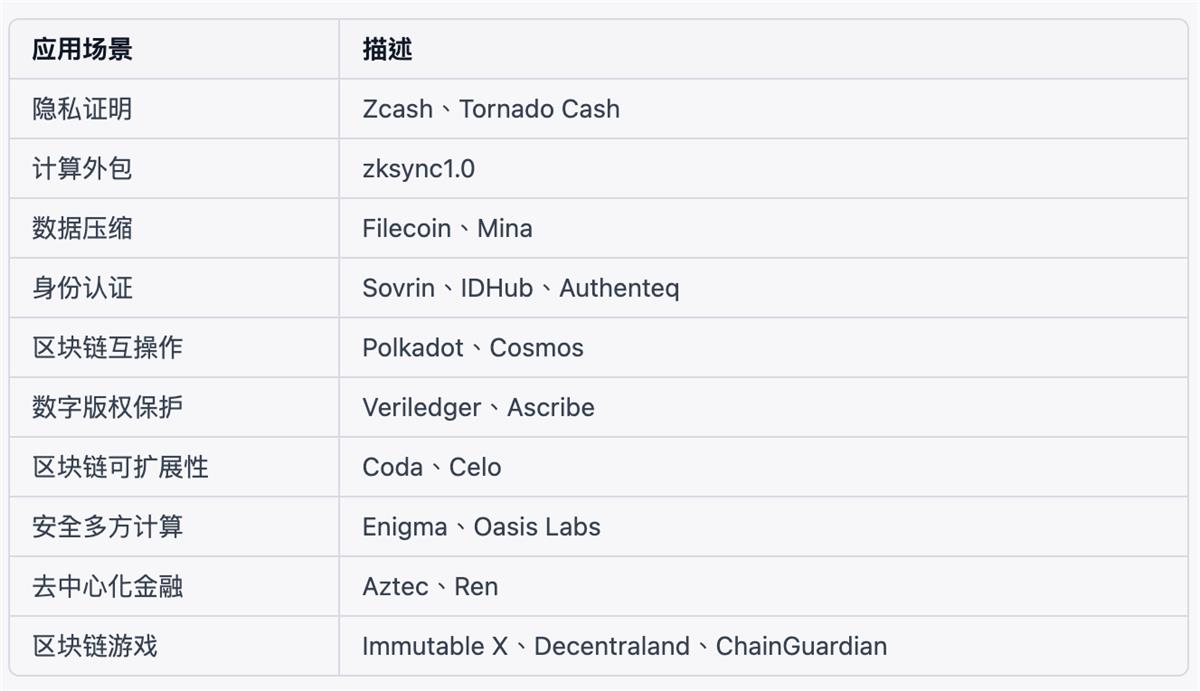
Application Prospects of ZK-STARKs in Bitcoin
The application of ZK-STARKs aligns with Bitcoin’s conservative design philosophy—it does not require trusted setups and instead relies on hash functions, Merkle trees, and polynomials, enhancing transparency and security. An advantage of EC-STARKs on Bitcoin is improved privacy, as transaction details no longer need to be disclosed. Another benefit is reduced storage requirements, as vast amounts of data can be compressed into compact proofs. A challenge, however, is the increased computational demand due to complex mathematical operations. Additionally, greater coordination and standardization are required to ensure compatibility with Bitcoin’s existing protocols and infrastructure.
From a technical implementation perspective, ZK-STARKs applications can be categorized into aspects such as light nodes, full nodes, and verification methods. Light nodes can use STARK proofs for block header states, enabling rapid synchronization. Full nodes can generate validity proofs via UTXO state and adopt utreexo technology to represent UTXO state in a new format, eliminating the need to store the entire UTXO set. In terms of verification, given the utreexo root and final state, incoming blocks can be validated immediately.
Moreover, there are many potential directions for ZK-STARKs applications. For example, combining ZK-STARKs with the Taro protocol could transform Bitcoin into a more versatile asset platform, expanding its use cases. Integrating ZK-STARKs with Taro enhances the protocol’s scalability, enabling it to handle more transactions and support larger-scale applications, opening doors for multi-chain deployment. Additionally, Bitcoin’s long-standing privacy issues could be significantly mitigated through ZK-STARKs. By applying this technology, an entire transaction history can be compressed into a single transaction, effectively concealing user transaction data.
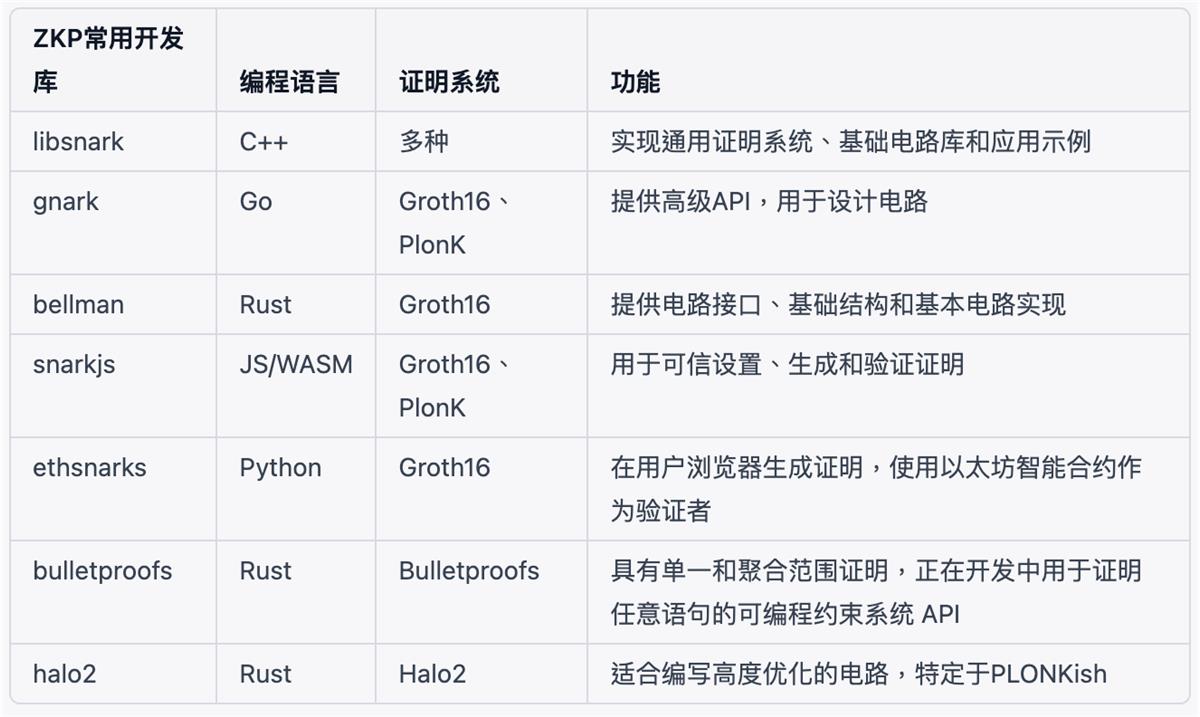
Source: Bing Ventures
Future Watchpoints
Further ahead, ZK-STARKs can be used to verify Bitcoin transactions, including transaction serialization, double-SHA calculations, and secp256k1 operations. These are core components of Bitcoin transaction validation, and using ZK-STARKs ensures a highly secure and reliable verification process. ZK-STARKs can also validate accelerated Cairo built-in functions. Cairo is an efficient zero-knowledge proof system; when integrated with Bitcoin’s accelerated Cairo features, it enables efficient and secure Bitcoin transaction verification.
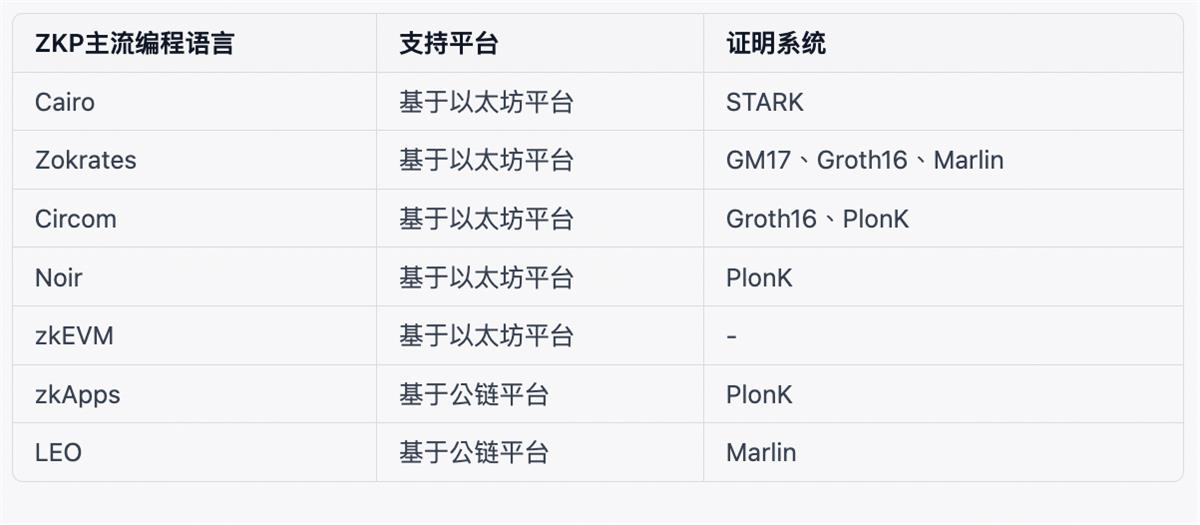
Source: Bing Ventures
ZK-STARKs can also facilitate Taro primitives and asset TLV serialization, as well as MS-SMT implementation and verification. These operations effectively protect the privacy and security of Bitcoin transactions, further enhancing their credibility and reliability. The Lightning Network, as Bitcoin’s Layer-2 solution, can leverage ZK-STARKs technology to enable faster, more secure Bitcoin transactions. Using ZK-STARKs, Lightning Network transactions can be rapidly verified without compromising transaction privacy.
We are seeing growing adoption of zero-knowledge proof technology across blockchain infrastructure and dApps. Some emerging solutions may accelerate ZKP adoption in the blockchain space, better addressing privacy and scalability challenges. However, most projects remain Ethereum-centric, while Bitcoin receives insufficient attention in the ZKP domain. Worse still, engineering practice lags behind academic progress in some respects. More implementation, exploration, and support are needed in this field.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News