GMX Hacked for $42 Million: How Can DeFi Security Be Guaranteed?
TechFlow Selected TechFlow Selected

GMX Hacked for $42 Million: How Can DeFi Security Be Guaranteed?
GMX V1 trading suspended, V2 spared.
Author: ChandlerZ, Foresight News
On July 9, GMX's V1 system on Arbitrum was attacked. The attacker exploited a vulnerability within the contract to withdraw approximately $42 million worth of assets from the GLP liquidity pool. Following the incident, GMX suspended platform trading and blocked GLP minting and redemption functions. The attack did not affect GMX’s V2 system or its native token, but it has reignited discussions about asset management mechanisms in DeFi protocols.
Attack Process and Fund Flow
Security firms PeckShield and SlowMist reported that the attacker exploited a flaw in GMX V1’s AUM calculation logic. This defect caused the contract to update the global average price immediately after opening short positions. Leveraging this, the attacker created a targeted operation path to manipulate token prices and execute profitable redemptions.
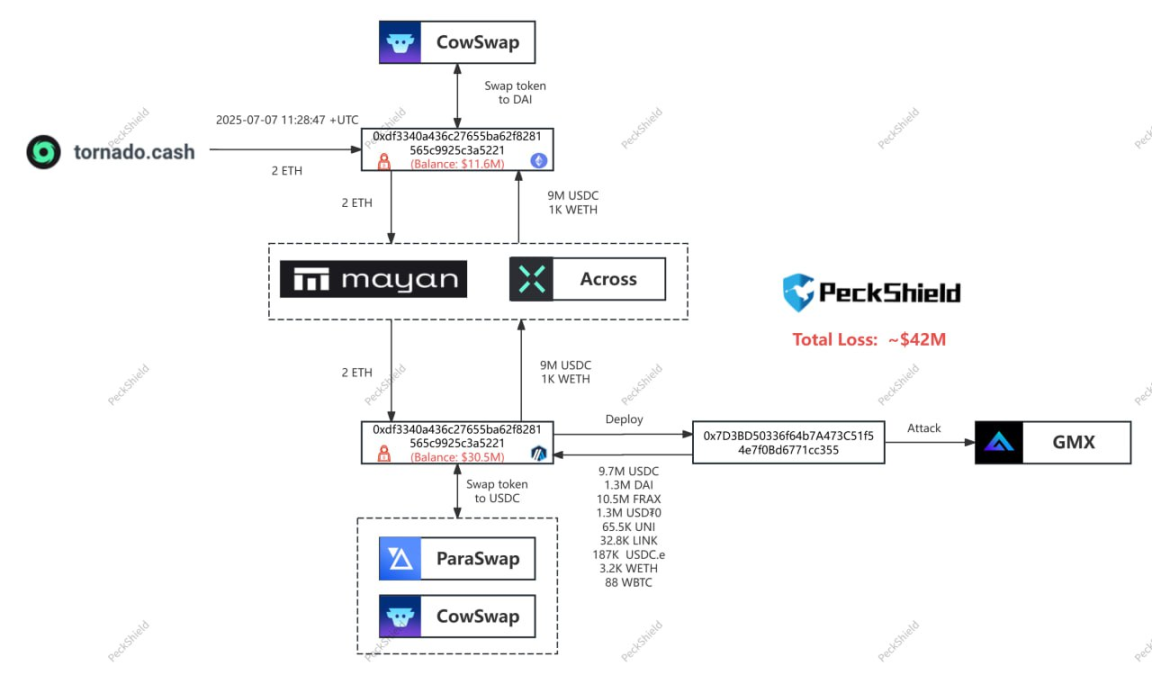
The attacker transferred around $9.65 million from Arbitrum to Ethereum, where it was exchanged into DAI and ETH. Some of these funds were then sent to the mixer protocol Tornado Cash. Approximately $32 million in assets remain on Arbitrum, including tokens such as FRAX, wBTC, and DAI.
Following the incident, GMX sent an on-chain message to the hacker’s address, requesting the return of 90% of the stolen funds in exchange for a 10% white-hat bounty. However, according to latest on-chain data, the hacker has already converted the stolen assets from the GMX V1 pool into ETH.
The stolen assets included WBTC, WETH, UNI, FRAX, LINK, USDC, and USDT. Except for FRAX, all other assets have now been sold for 11,700 ETH (worth approximately $32.33 million), which has been distributed across four wallets. As a result, the GMX hacker currently holds 11,700 ETH (worth ~$32.33 million) and 10.495 million FRAX across five wallets, totaling about $42.8 million in value.
Analyst Yujin noted that this move likely indicates the hacker has rejected GMX’s offer to return assets in exchange for a 10% bounty.
Vulnerability in Contract Logic
Security analysts pointed out that the attacker did not exploit unauthorized access or bypass permission controls. Instead, they operated within expected function logic, repeatedly calling functions during execution by exploiting timing gaps in state updates—classic reentrancy behavior.
SlowMist stated that the root cause lies in a design flaw in GMX v1: opening short positions immediately updates the globalShortAveragePrices, which directly affects AUM calculations and consequently manipulates GLP token pricing. The attacker leveraged the Keeper’s ability to enable "timelock.enableLeverage" during order execution—a prerequisite for creating large short positions—to exploit this vulnerability. Through reentrancy, the attacker opened massive short positions, manipulated the global average price, artificially inflated the GLP price within a single transaction, and profited via redemption.
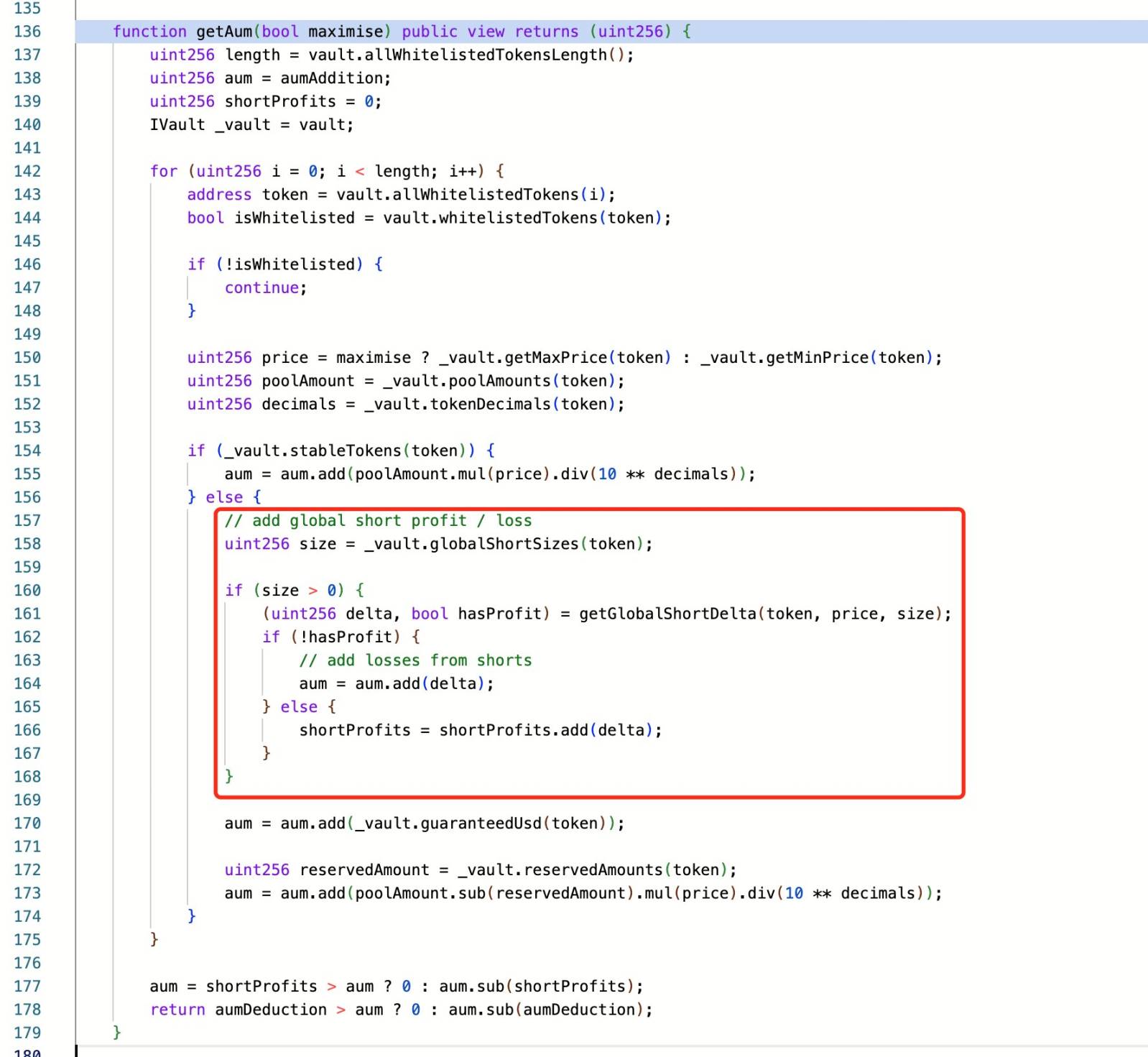
This type of attack is not new in DeFi. When balance or position updates lag behind asset minting or redemption, temporary inconsistent states can be exposed, allowing attackers to construct exploit paths and extract undercollateralized assets.
GMX V1 uses a shared liquidity pool design—a unified vault composed of multiple users’ assets, with account information and liquidity status managed by smart contracts. GLP is the representative LP token for this pool, with its price and exchange rate dynamically calculated based on on-chain data and contract logic. Such synthetic token systems carry observable risks, including amplified arbitrage opportunities, manipulation vectors, and inter-call state delays.
Official Response
Shortly after the attack, GMX issued a statement clarifying that only the V1 system and its GLP fund pool were affected. GMX V2, the native token, and other markets remained secure. To prevent further attacks, the team suspended all trading operations on V1 and disabled GLP minting and redemption on both Arbitrum and Avalanche.
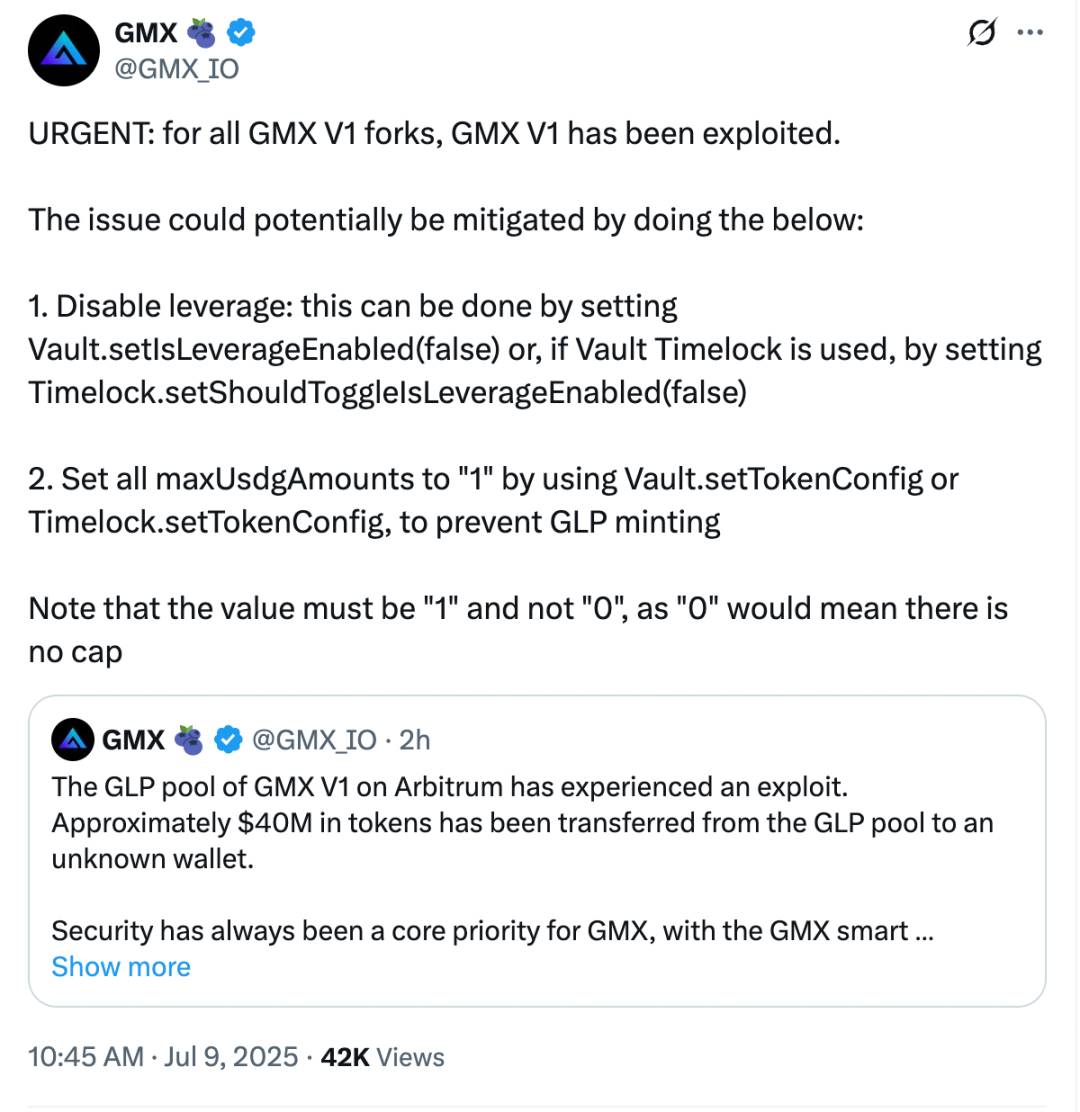
The team also stated their current focus is on restoring operational security and auditing internal contract mechanisms. V2 does not inherit V1’s logic structure and employs different mechanisms for liquidation, pricing, and position handling, resulting in limited exposure to similar risks.
GMX’s token dropped over 17% within 24 hours of the attack, falling from around $14.42 to a low of $10.30, though it has since slightly recovered to $11.78. Prior to the incident, GMX had recorded over $30.5 billion in cumulative trading volume, served more than 710,000 registered users, and maintained open interest exceeding $229 million.
Ongoing Pressure on Crypto Asset Security
The GMX attack is not an isolated case. Since 2025, total losses from hacks in the cryptocurrency industry have already surpassed those of the same period last year. Although the number of incidents declined in Q2, this does not indicate reduced risk. According to CertiK, total losses due to hacks, scams, and exploits in the first half of 2025 exceeded $2.47 billion—nearly 3% higher than the $2.4 billion lost in all of 2024. Two major breaches—the Bybit cold wallet theft and the Cetus DEX intrusion—accounted for $1.78 billion in combined losses, making up the majority of total damages. This concentration of high-value heists highlights that high-value assets still lack sufficient isolation and redundancy mechanisms, and platform design vulnerabilities remain unresolved.
In terms of attack types, wallet compromises have caused the most severe financial damage. There were 34 such incidents in the first half, resulting in the loss of approximately $1.7 billion. Compared to technically complex exploits, wallet attacks typically rely on social engineering, phishing links, or privilege deception—lower technical barriers with highly destructive outcomes. Hackers are increasingly targeting user-side entry points for assets, especially in cases where multi-factor authentication is not enabled or hot wallets are used.
Meanwhile, phishing attacks continue to grow rapidly, becoming the most frequent attack vector. A total of 132 phishing incidents were recorded in the first half, causing cumulative losses of $410 million. Attackers use fake websites, spoofed contract interfaces, or forged transaction confirmation flows to trick users into unintended actions, thereby stealing private keys or authorization rights. Attackers are constantly refining their tactics to make phishing attempts harder to detect, making user awareness and security tooling critical lines of defense.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News