Security Firm Turns "Hacker": Recounting the Origins and Events of the Kraken vs. CertiK Showdown
TechFlow Selected TechFlow Selected

Security Firm Turns "Hacker": Recounting the Origins and Events of the Kraken vs. CertiK Showdown
When so-called white-hat security firms turn into "hackers," the line between black and white in Web3's wild world seems no longer so clear-cut.
By TechFlow
June 20 — Today’s spotlight is on a heated crypto controversy between cryptocurrency exchange Kraken and blockchain security firm CertiK. A storm of online outrage is unfolding, with many prominent figures and KOLs in the industry accusing CertiK on X (formerly Twitter) of extortion and hacker-like behavior. What exactly happened?
Kraken, a U.S.-based crypto exchange, has long operated a bug bounty program that rewards individuals who report security vulnerabilities.
Kraken’s Chief Security Officer stated on X that a security researcher had previously reported a critical vulnerability through this program.
The flaw allowed malicious actors to generate assets in their Kraken accounts without completing actual deposits. Upon receiving the report, Kraken immediately patched the vulnerability.
But upon further review, something didn’t add up — the reporter’s intentions were far from noble.
The security researcher increased their own account balance by $4, and also shared the exploit with two others, who proceeded to withdraw nearly $3 million from Kraken accounts.
Kraken then attempted to cooperate with the researcher to recover the funds, but was met with refusal. Instead, the researcher demanded that Kraken engage with their company’s BD team (sales representatives), and refused to return any funds until Kraken first provided an estimated hypothetical loss amount. This is not ethical white-hat behavior — it's extortion!
Kraken’s security team was furious, labeling these actions not as responsible disclosure, but as criminal extortion. They’ve decided to treat the incident as a criminal case and are coordinating with law enforcement.
And the company refusing to return the funds? Who could it be?
None other than the other protagonist of this story — security firm CertiK.
CertiK responded to the allegations, stating:
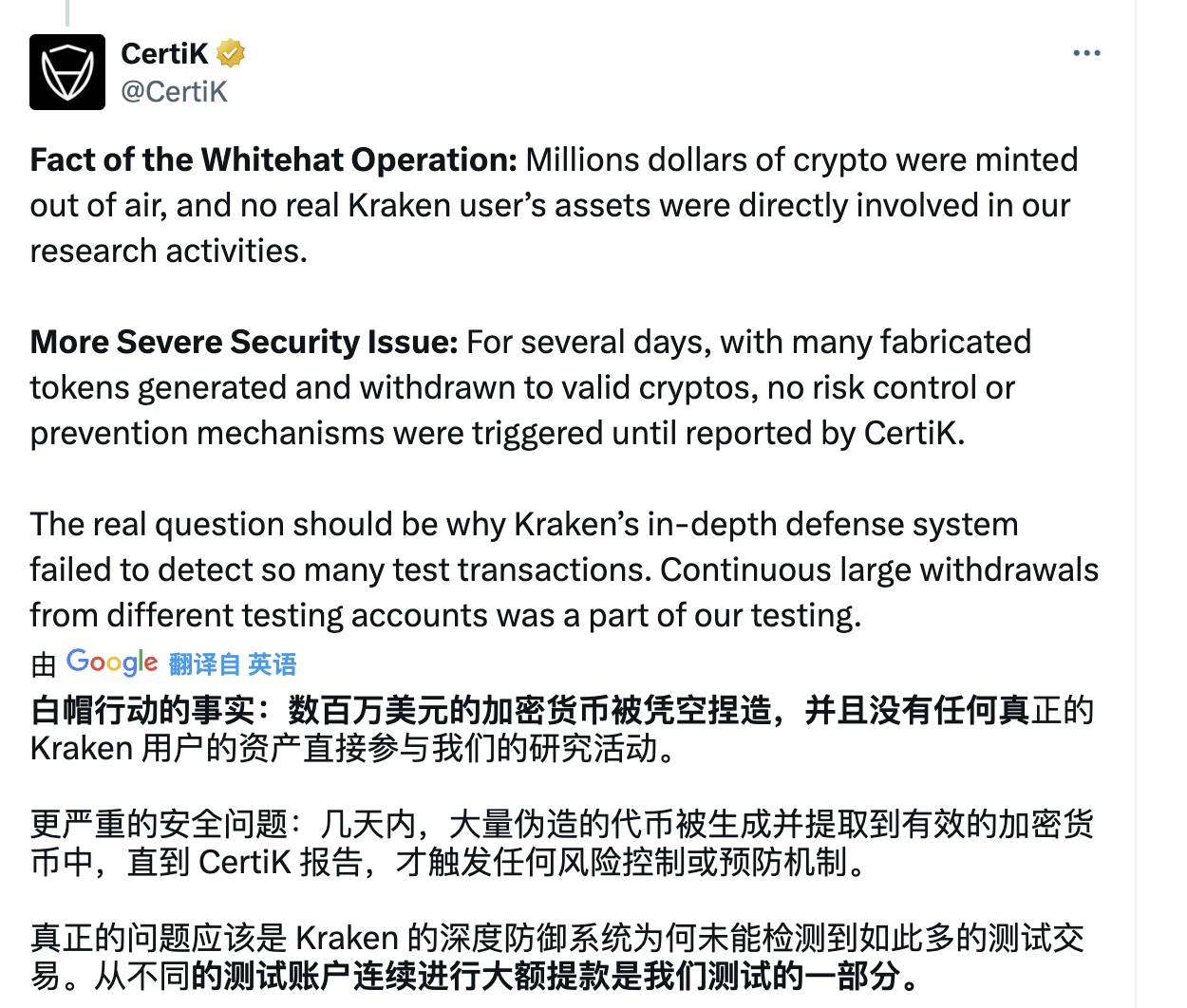
They discovered a severe security vulnerability on Kraken’s exchange that could have led to losses of hundreds of millions of dollars. Through testing, they identified three major issues, and more alarmingly, no alerts were triggered during multiple days of testing.
After the fix, Kraken’s security operations team allegedly threatened CertiK employees, demanding unreasonable repayment of mismatched amounts of cryptocurrency — without even providing a wallet address for repayment.
CertiK also published a timeline of events, claiming they first detected the issue as early as June 5.
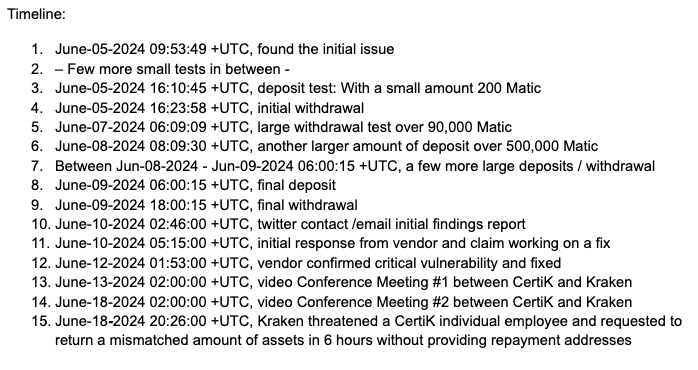
As the story spread, more details emerged.
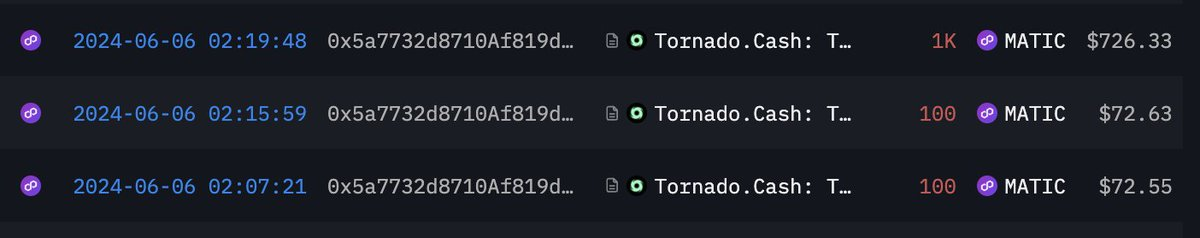
@0xBoboShanti discovered that a wallet address linked to a CertiK security researcher had already begun probing and testing as early as May 27 — contradicting CertiK’s official timeline.
Additionally, Coinbase executive director @jconorgrogan pointed out that CertiK interacted with Tornado Cash, a cryptocurrency mixer specifically designed for laundering funds. He commented in CertiK’s thread: “You do realize Tornado Cash is sanctioned by OFAC (Office of Foreign Assets Control), right? And your company is registered in the U.S., correct?”
Browsing the discussions on X, the backlash is overwhelming, with widespread accusations that CertiK has transformed from a security firm into an extortionist hacker group.
Hype, founder of Hype Investments, stated:
“CertiK stole $3 million from Kraken, demanded a bounty, and refused to return the money. They confirmed it all in a single tweet. Now they’re moving all the funds into Tornado.cash to prevent authorities from seizing them.”
Adam Cochran, a well-known crypto KOL with 210k followers, said: “Certik just admitted they’re the security firm that hacked Kraken and tried to extort more money. Given how often Certik-audited projects get hacked, and now this — yet Certik still exists? Unbelievable. These are criminals.”
One bystander in the comments, @cryptopsychdoc, offered a biting analogy:
“Certik is like catching your cheating girlfriend red-handed. When you confront her, she turns it around and blames you for checking her phone.”
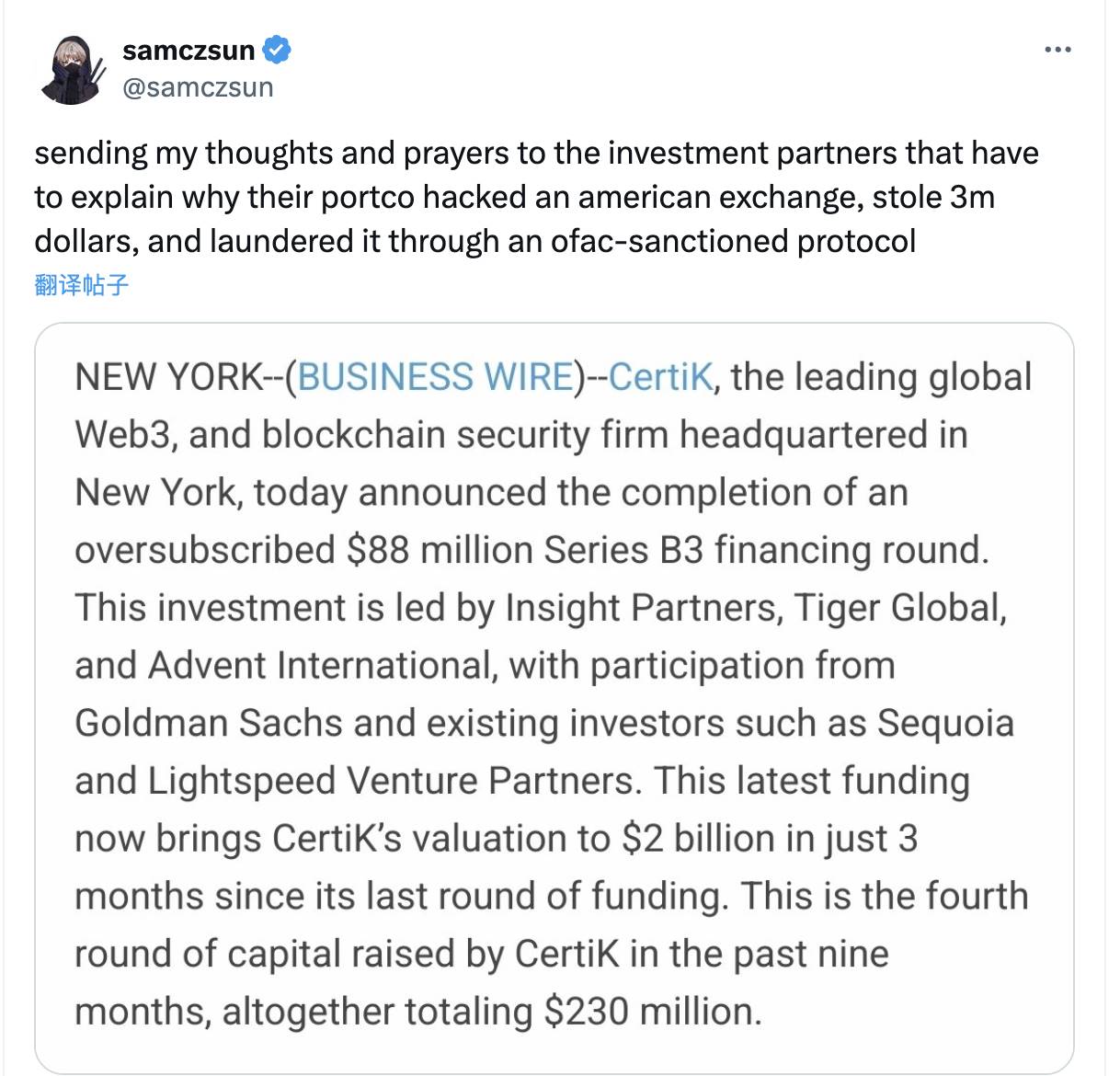
Paradigm’s CTO sarcastically retweeted CertiK’s past funding announcement: “My best wishes to the investment partners who now have to explain why their portfolio company hacked a U.S. exchange, stole $3 million, and laundered it through an OFAC-sanctioned protocol.”
According to previous reports, in April 2022, CertiK announced an $88 million Series B3 round led by Insight Partners, Tiger Global, and Advent International, with participation from Goldman Sachs, Sequoia Capital, and Lightspeed. In just nine months, CertiK completed four funding rounds totaling $230 million, reaching a valuation of $2 billion.
We tried to find more direct responses from CertiK: When will they return the assets? Why won’t they return them? If the claimed amount is inaccurate, what should it be? And why did they interact with Tornado Cash?
Yet their latest response repeatedly emphasizes: “The real question should be why Kraken’s layered defense system failed to detect so many test transactions. Large withdrawals from multiple test accounts were part of our testing process.”
It reads like mockery — “It’s simply because you’re too weak!”
Looking at the full sequence of events, when a self-proclaimed white-hat security firm acts like a hacker, the line between right and wrong in the wild world of Web3 appears increasingly blurred.
The irony deepens when you consider that “CertiK” itself is derived from the English word “Certification.” When the “certifier” needs certification of their own ethics, the impression of a makeshift operation becomes even stronger.
Don't Trust, Just Verify.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News