TechFlow news, November 12 — GoPlus analyzed and posted on social media that the Hello 402 contract has some relatively hidden risks—unlimited minting and centralized manipulation vulnerabilities.
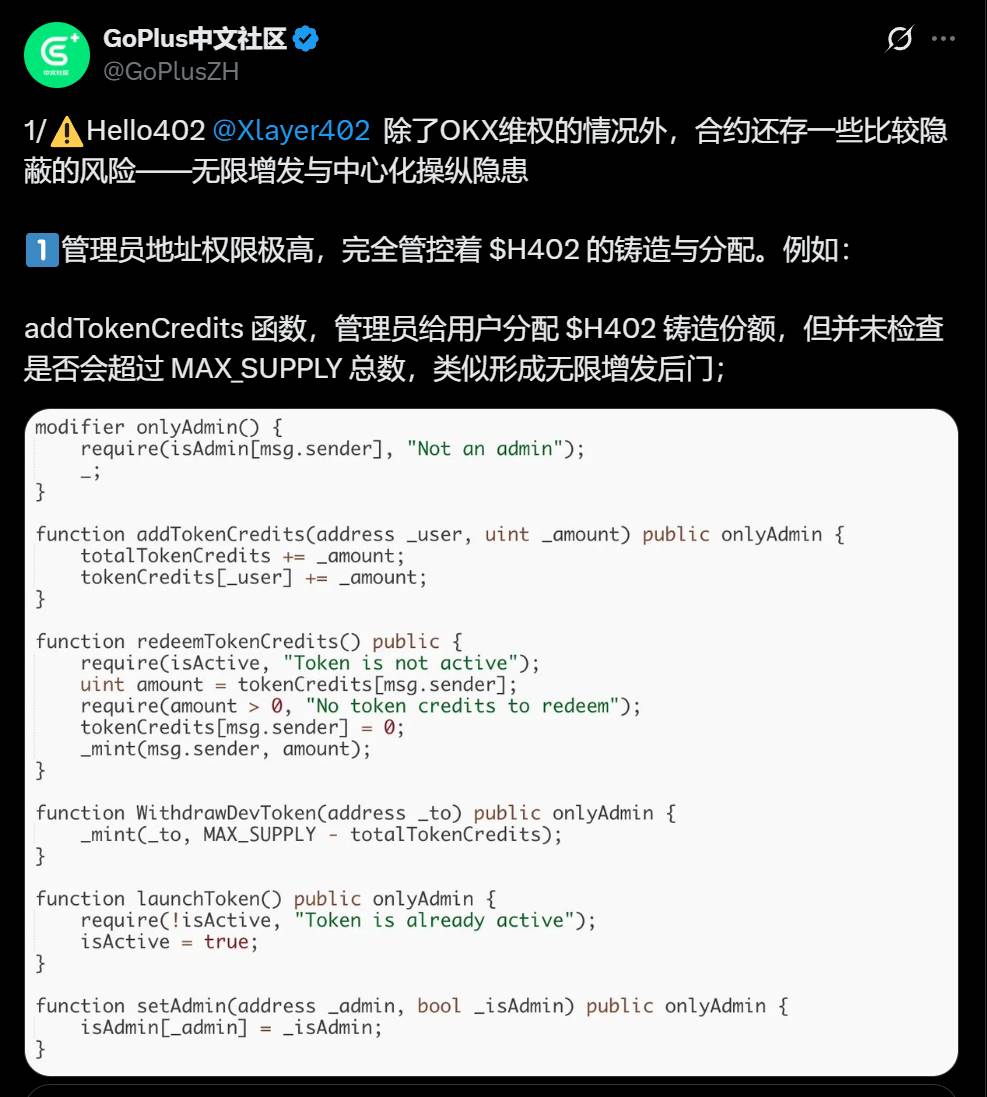
1. The admin address has extremely high privileges, fully controlling the minting and distribution of H402 tokens. For example:
-
The addTokenCredits function allows the administrator to allocate H402 token minting shares to users but does not check whether the total will exceed MAX_SUPPLY, creating a backdoor for unlimited minting;
-
The redeemTokenCredits function enables users to actually mint H402 tokens according to their allocated shares;
-
The WithdrawDevToken function allows the admin address to instantly mint all unallocated shares, posing a high risk of centralized manipulation.
2. The project team's claims on X regarding the WithdrawDevToken function being used only for "token top-up," "ecosystem incentives," and "profit margin" after the private sale ends have not been concretely implemented at the contract level, indicating a high risk of centralized default.
Earlier news: A crypto KOL posted that Hello 402, a project on X Layer, is suspected of having "rugged" (abandoned the project).