Lost $5,000 from encrypted wallet after connecting to hotel Wi-Fi for three days
TechFlow Selected TechFlow Selected

Lost $5,000 from encrypted wallet after connecting to hotel Wi-Fi for three days
That day, I didn't sign any transaction to transfer funds, but rather signed an authorization license.
Author: The Smart Ape
Translation: TechFlow
A few days ago, I went with my family to a nice hotel for the year-end holiday. One day after leaving the hotel, my wallet was completely drained. I couldn't figure it out at all—after all, I hadn't clicked any phishing links or signed any malicious transactions.
After hours of investigation and bringing in experts for help, I finally uncovered the truth. It all came down to the hotel’s Wi-Fi network, a short phone call, and a series of foolish mistakes.
Like most crypto enthusiasts, I brought my laptop along, thinking I could squeeze in some work while spending time with my family. My wife repeatedly insisted that I not work during those three days—I really should have listened to her.
Like other guests, I connected to the hotel's Wi-Fi network. It required no password—just login through a captive portal.

I worked as usual during my stay, without doing anything risky: no creating new wallets, no clicking strange links, no visiting suspicious dApps. I just browsed X (Twitter), checked my balances, Discord, and Telegram.
At one point, I received a call from a friend in the crypto space. We chatted about market trends, Bitcoin, and other crypto topics. But what I didn’t know was that someone nearby was eavesdropping on our conversation—and realized I was involved in cryptocurrency. That was my first mistake. From our conversation, the attacker learned I was using a Phantom wallet and that I held a significant amount.
That’s when he set his sights on me.
In public Wi-Fi networks, all devices share the same network, and actually, devices can see each other far more than you'd expect. There is almost no real protection between users, making "Man-in-the-Middle Attacks" possible. The attacker acts like an invisible intermediary, quietly inserting themselves between you and the internet—like someone secretly reading and altering your mail before it reaches you.
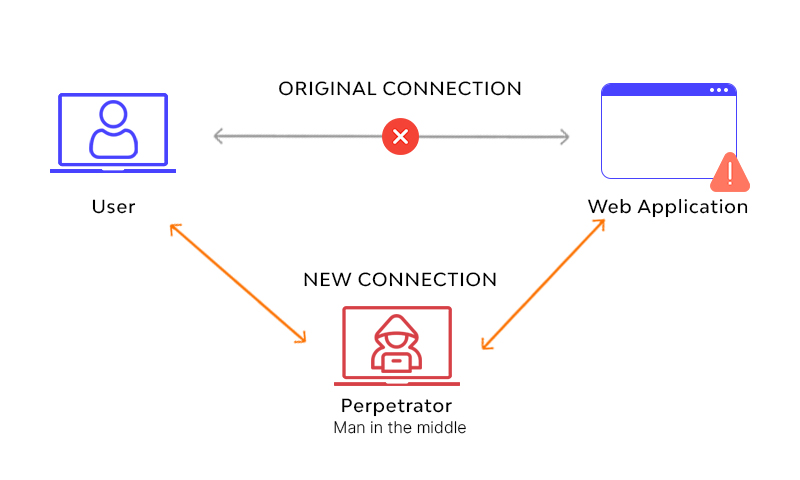
While browsing the web on the hotel Wi-Fi, one website appeared to load normally—but in reality, malicious code had been injected into the page. At the time, I noticed nothing unusual. Had I used security tools, I might have detected this, but unfortunately, I didn’t.
Normally, websites may request your wallet to sign certain operations. Phantom would pop up a window where you choose to approve or reject. Usually, you’d trust the site and browser enough to go ahead and sign. But that day, I shouldn’t have.
Just as I was swapping tokens on @JupiterExchange, the malicious code triggered a wallet request that replaced my legitimate swap transaction. I could have spotted it by carefully reviewing the transaction details, but since I was already conducting a swap on Jupiter, I didn’t suspect anything.
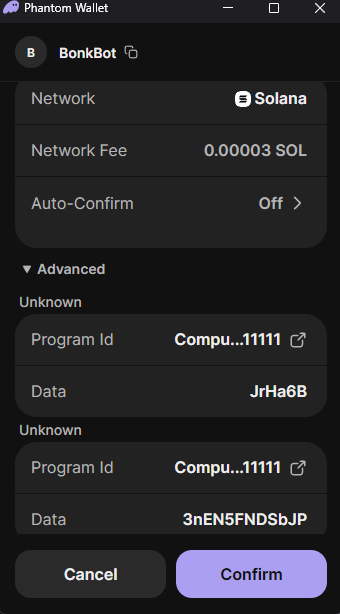
That day, I didn’t sign any fund-transfer transaction—instead, I signed an authorization. And that’s exactly why my assets were stolen days later.
The malicious code didn’t ask me to send SOL (Solana) directly—that would’ve been too obvious. Instead, it asked me to “grant access,” “approve account,” or “confirm session.” In simple terms, I gave another address permission to act on my behalf.
I approved it because I thought it was related to my Jupiter operation. The message from Phantom looked technical, showed no amount, and didn’t indicate an immediate transfer.
And that was all the attacker needed. He waited patiently until I left the hotel, then struck. He moved my SOL, pulled out my tokens, and transferred my NFTs to another address.
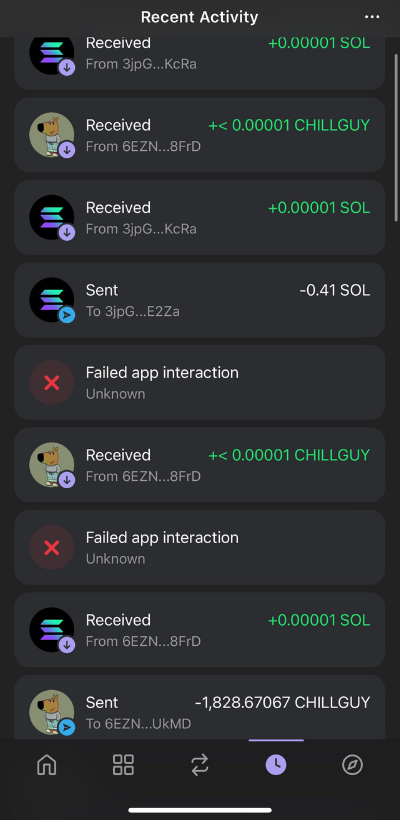
I never thought this could happen to me. Fortunately, this wasn’t my main wallet—it was a hot wallet meant for specific operations, not long-term asset storage. Still, I made many mistakes, and I believe I bear primary responsibility.
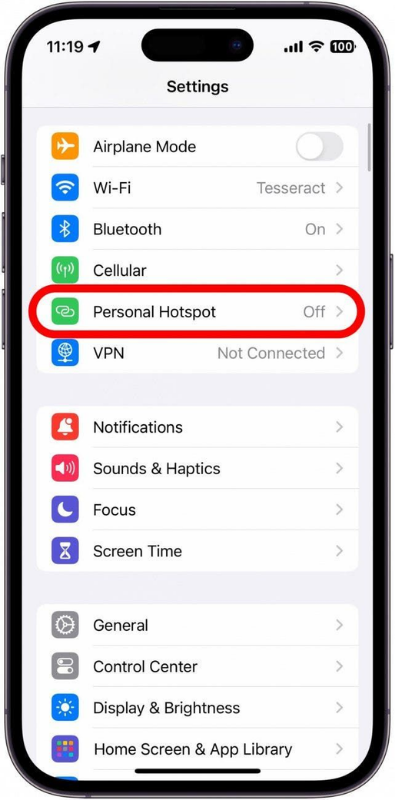
First, I should never have connected to the hotel’s public Wi-Fi. I should have used my phone’s hotspot instead.
My second mistake was discussing cryptocurrency in a public area of the hotel, where many people could overhear. My father once warned me never to let others know I’m involved in crypto. This time I was lucky—some people have been kidnapped or worse over their crypto holdings.
Another mistake: I approved a wallet request without full attention. Because I assumed it came from Jupiter, I didn’t analyze it carefully. In fact, every wallet request should be thoroughly reviewed—even on apps you trust. Requests can be intercepted and may not actually originate from the app you think.
In the end, I lost around $5,000 from a secondary wallet. While not the worst-case scenario, it’s still deeply frustrating.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News